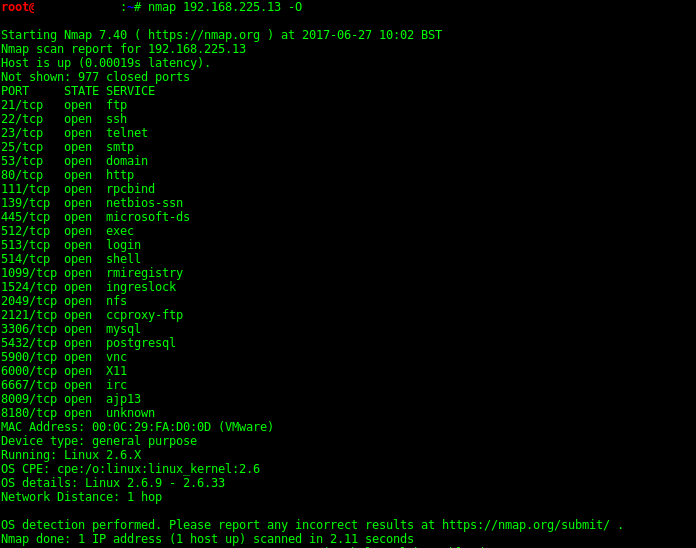
Nmap - Cheatsheet
Nmap Nikto Scan
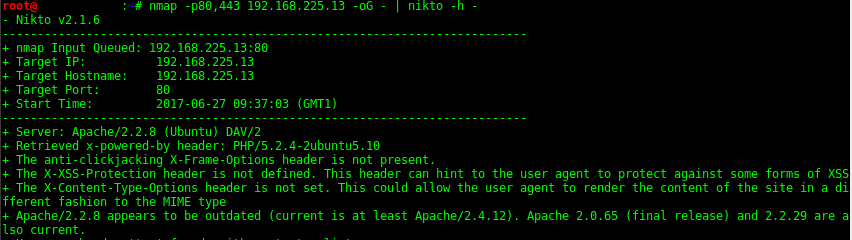
Scans for http (Web) servers on port 80 and pipes into Nikto for scanning.
nmap -p80 10.0.1.0/24 -oG - | nikto.pl -h -
Scans for http/https servers on port 80 & 443 and pipes into Nikto.
nmap -p80,443 10.0.1.0/24 -oG - | nikto.pl -h -
Target Specification
Nmap is able to use hostnames, IP addresses and subnets.
nmap www.company.domain.com
nmap 192.168.1.1
nmap 10.0.0-255.1-254
Target Specific settings
-iL inputfilename: Input from list of hosts/networks
-iR num hosts: Choose random targets
--exclude host1[,host2][,host3],... : Exclude hosts/networks
--excludefile exclude_file: Exclude list from file
Host Discovery
-sL List Scan - simply list targets to scan
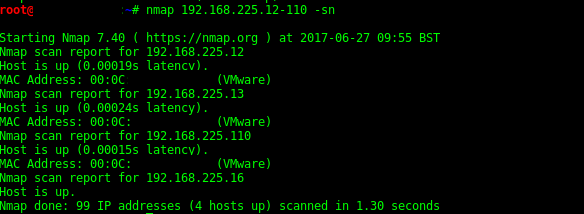
-sn Ping Scan - disable port scan
-Pn Treat all hosts as online -- skip host discovery
-PS/PA/PU/PY[portlist] TCP SYN/ACK, UDP or SCTP discovery to given ports
-PE/PP/PM ICMP echo, timestamp, and netmask request discovery probes
-PO[protocol list] IP Protocol Ping
-n/-R Never do DNS resolution/Always resolve [default: sometimes]
Scan Techniques
-sS TCP SYN scan
-sT Connect scan
-sA ACK scan
-sW Window scan
-sM Maimon scan
-sU UDP Scan
-sN TCP Null scan
-sF FIN scan
-sX Xmas scan
--scanflags Customize TCP scan flags
-sI zombie host[:probeport] Idle scan
-sY SCTP INIT scan
-sZ COOKIE-ECHO scan
-sO IP protocol scan
-b "FTP relay host" FTP bounce scan
Port Specification and Scan Order
-p Specify ports, e.g. -p80,443 or -p1-65535
-p U:PORT Scan UDP ports with Nmap, e.g. -p U:53
-F Fast mode, scans fewer ports than the default scan
-r Scan ports consecutively - don't randomize
--top-ports "number" Scan "number" most common ports
--port-ratio "ratio" Scan ports more common than "ratio"
Service Version Detection
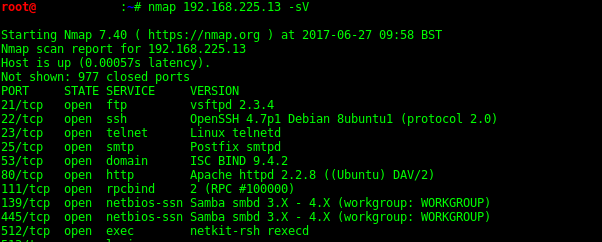
-sV Probe open ports to determine service/version info
--version-intensity "level" Set from 0 (light) to 9 (try all probes)
--version-light Limit to most likely probes (intensity 2)
--version-all Try every single probe (intensity 9)
--version-trace Show detailed version scan activity (for debugging)
Script Scan
-sC equivalent to --script=default
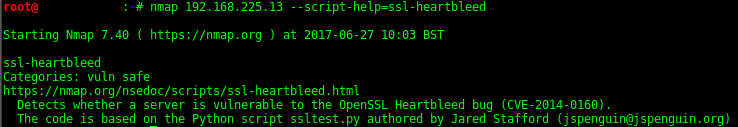
--script="ssl-heartbleed" "ssl-heartbleed" Is the selected script
--script-args=n1=v1,[n2=v2,...] provide arguments to scripts
-script-args-file=filename provide NSE script args in a file
--script-trace Show all data sent and received
--script-updatedb Update script database
--script-help="ssl-heartbleed" Show help about scripts
OS Detection
-O Enable OS Detection
--osscan-limit Limit OS detection to promising targets
--osscan-guess Guess OS more aggressively
Firewalls IDS Evasion and Spoofing
-f; --mtu VALUE Fragment packets (optionally w/given MTU)
-D decoy1,decoy2,ME Cloak a scan with decoys
-S IP-ADDRESS Spoof source address
-e IFACE Use specified interface
-g PORTNUM Use given port number
--source-port PORTNUM
--proxies url1,[url2],... Relay connections through HTTP / SOCKS4 proxies
--data-length NUM Append random data to sent packets
--ip-options OPTIONS Send packets with specified ip options
--ttl VALUE Set IP time to live field
--spoof-mac ADDR/PREFIX/VENDOR Spoof NMAP MAC address
--badsum Send packets with a bogus TCP/UDP/SCTP checksum
Nmap Output Options
-oN Output Normal
-oX Output to XML
-oS Script Kiddie / 1337 speak... sigh
-oG Output greppable - easy to grep nmap output
-oA BASENAME Output in the three major formats at once
-v Increase verbosity level use -vv or more for greater effect
-d Increase debugging level use -dd or more for greater effect
--reason Display the reason a port is in a particular state
--open Only show open or possibly open ports
--packet-trace Show all packets sent / received
--iflist Print host interfaces and routes for debugging
--log-errors Log errors/warnings to the normal-format output file
--append-output Append to rather than clobber specified output files
--resume FILENAME Resume an aborted scan
--stylesheet PATH/URL XSL stylesheet to transform XML output to HTML
--webxml Reference stylesheet from Nmap.Org for more portable XML
--no-stylesheet Prevent associating of XSL stylesheet w/XML output
Recent Posts
Tags
about
active-directory
ad
attack
authentication
backdoor
blackhills
bootloader
burp
bypass
camera
cctv
cheatsheet
computer
crackmapexec
databases
domain
ducky
dump
easy
elastic
empire
enum
escalation
events
exploit
extensions
fatrat
file
generating
generation
guide
hak5
hashes
iis
implants
kcsec
kerberos
kernel
kernelpop
ksec security snapshot
lab
lateral movement
leaked online
linux
marine vessels
metasploit
metasploitable
mimikatz
mongodb
Categories
Active directory Burpsuite Cheatsheet Crackmapexec Empire Events Exploit File transfer Iis Implants Kcsec Kerberos Kernelpop Ksec Ksec snapshot Lab Metasploit Metasploitable Msfvenom Netcat Nfc & rfid Nikto Nmap Pivoting Privilege escalation Proxmark Proxychains Redteam Responder Rubber ducky Shells Sqlmap Sshutle Thefatrat Toolkit Webapp Windows domain Xss