Nmap
What is NMAP ?
Nmap (Network Mapper), Is mother of all port scanners. Commonly used for network discovery and Service/Security enumeration. Use by Pentesters and System admins it can show exposed services on a target as well as system information.
More information can be found on the Devs site HERE
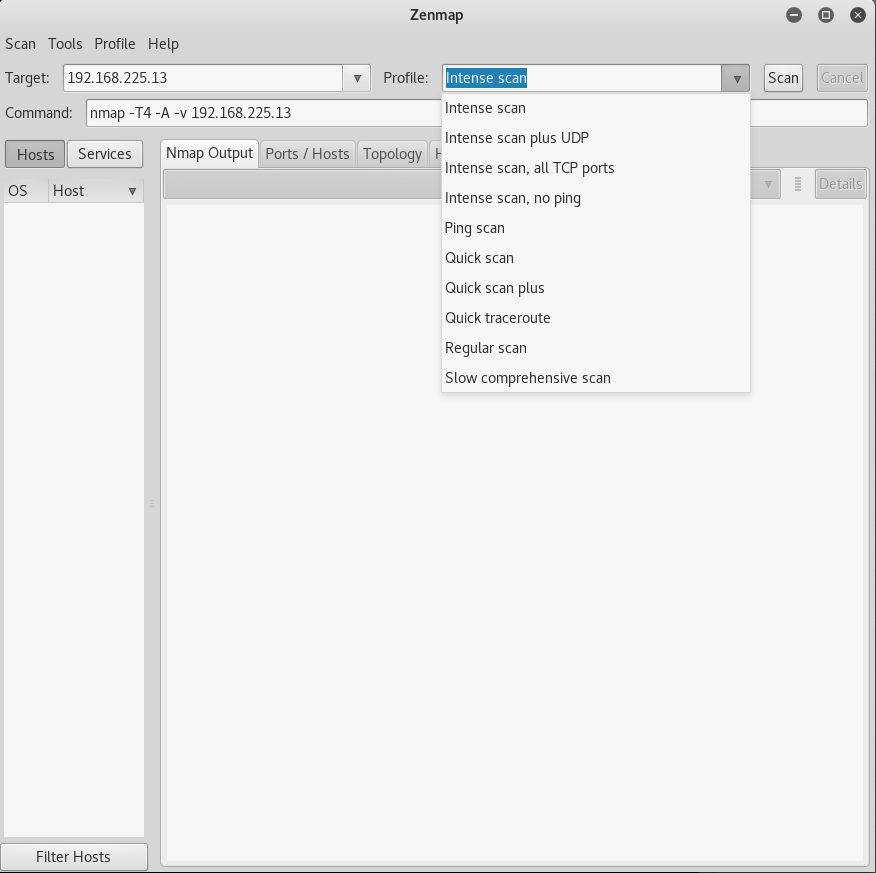
For those who prefer to use a GUI then check out Zenmap.
Key Points of Nmap
- Host discovery
- Port discovery & enumeration
- Service discovery
- Service version detection & enumeration
- Operating system version detection
- MAC address detection
- Vulnerability & exploit detection - NSE Scripts
Default scans
Intense Scan
nmap -T4 -A -v <target>
Intense Scan plus UDP
nmap -sS -sU -T4 -A -v <target>
Intense scan - All TCP Ports
nmap -p 1-65535 -T4 -A -v <target>
Intense Scan - No Ping
nmap -T4 -A -v -Pn <target>
Ping Scan
nmap -sn <target>
Quick Scan
nmap -T4 -F <target>
Quick Scan Plus
nmap -sV -T4 -O -F –version-light <target>
Quick Traceroute
nmap -sn –traceroute <target>
Regular Scan
nmap <target>
Slow Comprehensive scan
nmap -sS -sU -T4 -A -v -PE -PP -PS80,443 -PA3389 -PU40125 -PY -g 53 –script “default or (discovery and safe)” <target>
Using Nmap
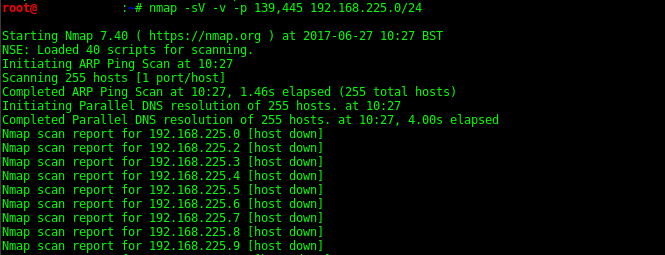
Find NetBios servers on subnet
nmap -sV -v -p 139,445 192.168.1.0/24
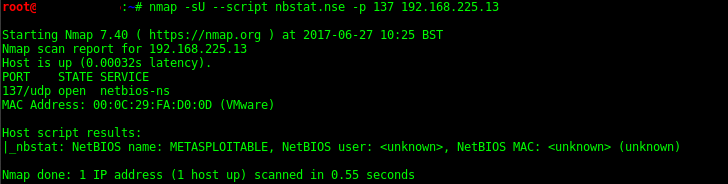
Using Netbios enumeration script (Nbstat.nse)
nmap -sU --script nbstat.nse -p 137 192.168.1.137
Check if Netbios servers are vulnerable to MS08-067
nmap --script-args=unsafe=1 --script smb-vuln-ms08-067.nse -p445 192.168.1.137
Heartbleed Testing
nmap -sV -p 443 --script=ssl-heartbleed 192.168.1.0/24
Basic how to use a script and args
The –script option takes a comma-separated list of categories, filenames, and directory names. Some simple examples of its use:
Loads all scripts in the default and safe categories.
nmap --script default,safe
Loads only the smb-os-discovery script. Note that the .nse extension is optional.
nmap --script smb-os-discovery
Loads the script in the default category, the banner script, and all .nse files in the directory /home/user/customscripts.
nmap --script default,banner,/home/user/customscripts
When referring to scripts from script.db by name, you can use a shell-style ‘*’ wildcard.
Loads all scripts whose name starts with http-, such as http-auth and http-open-proxy. The argument to –script had to be in quotes to protect the wildcard from the shell.
nmap --script "http-*"
More complicated script selection can be done using the and, or, and not operators to build Boolean expressions. The operators have the same precedence as in Lua: not is the highest, followed by and and then or. You can alter precedence by using parentheses. Because expressions contain space characters it is necessary to quote them.
Loads every script except for those in the intrusive category.
nmap --script "not intrusive"
This is functionally equivalent to nmap –script “default,safe”. It loads all scripts that are in the default category or the safe category or both.
nmap --script "default or safe"
Loads those scripts that are in both the default and safe categories.
nmap --script "default and safe"
Loads scripts in the default, safe, or intrusive categories, except for those whose names start with http-.
nmap --script "(default or safe or intrusive) and not http-*"
Names in a Boolean expression may be a category, a filename from script.db, or all. A name is any sequence of characters not containing ‘ ’, ‘,’, ‘(’, ‘)’, or ‘;’, except for the sequences and, or, and not, which are operators.
Recent Posts
Tags
Categories
Active directory Burpsuite Cheatsheet Crackmapexec Empire Events Exploit File transfer Iis Implants Kcsec Kerberos Kernelpop Ksec Ksec snapshot Lab Metasploit Metasploitable Msfvenom Netcat Nfc & rfid Nikto Nmap Pivoting Privilege escalation Proxmark Proxychains Redteam Responder Rubber ducky Shells Sqlmap Sshutle Thefatrat Toolkit Webapp Windows domain Xss