Nmap - NSE Scripts
Scripts info
Get help for a script
nmap --script-help=ssl-heartbleed
updating scripts
nmap --script-updatedb
Location and finding of scripts
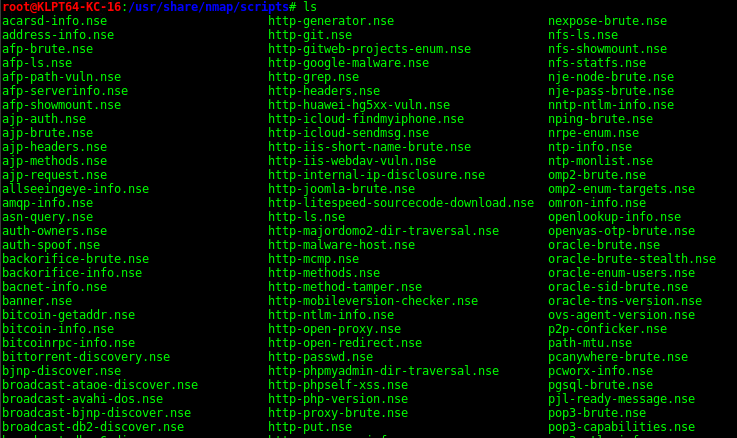
Locate *.nse - Will find all NSE Scripts on machine
/user/share/nmap/scripts/ -Default script location
Top Scripts
SMB subnet discovery
nmap -sS -sV --script smb-enum-shares.nse,smb-os-discovery.nse -p445,139 192.168.1.0/24
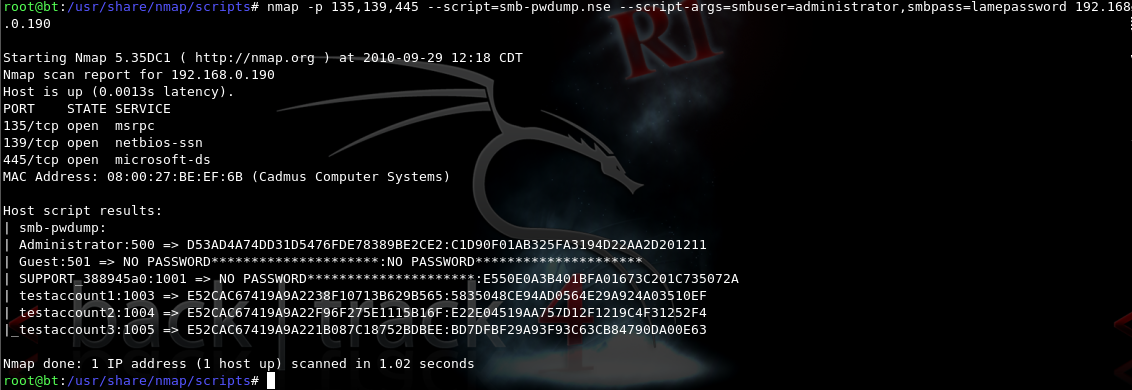
Dump SAM database remotely
nmap -p 135,139,445 --script smb-pwdump --script-args-smbuser=USERNAME,smbpass=PASSWORD <Target>

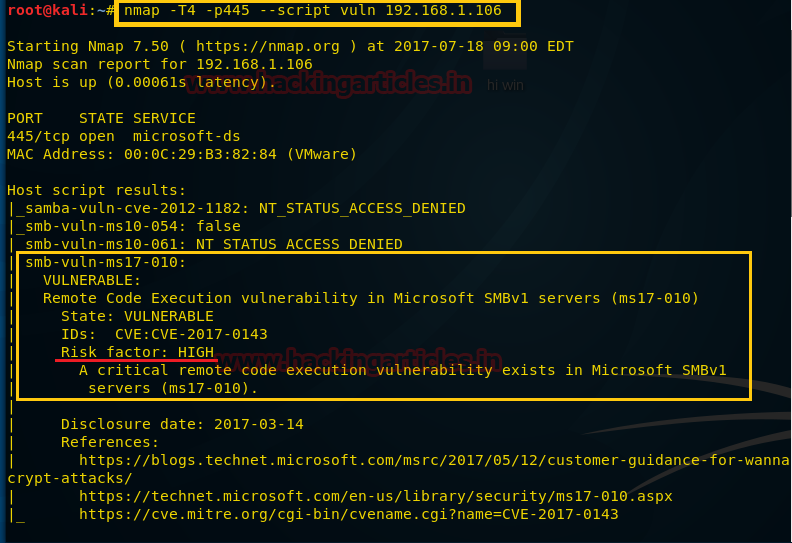
Nmap NSE script to detect MS17-010 vuln used by WannaCry - [Download] (https://github.com/cldrn/nmap-nse-scripts/blob/master/scripts/smb-vuln-ms17-010.nse)
nmap -v --script smb-vuln-ms17-010 -p445 <target>
Scan with all smb NSE scripts
nmap -sV --script smb* <Target>
Scan with all MS SQL NSE scripts
nmap -sV --script ms-sql* <Target>
Scan with all MYSQL NSE scripts
nmap -sV --script mysql* <Target>
Scan with all HTTP NSE scripts (Messy)
nmap -sV --script http* <Target>
Http NSE scripts
Detect Heartbleed SSL Vulnerability
nmap -sV -p 443 –script=ssl-heartbleed.nse <Target>
Gather page titles from HTTP services
nmap --script http-title <Target>
Get HTTP headers of web services
nmap --script http-headers <Target>
Http Enumeration - Find web apps from known paths
nmap --script http-enum <Target>
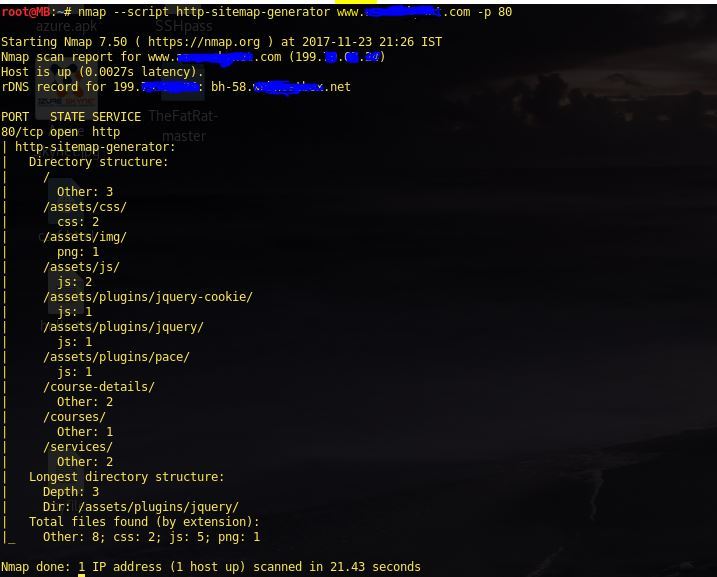
Http Sitemap Generator
nmap --script http-sitemap-generator <target> <port>
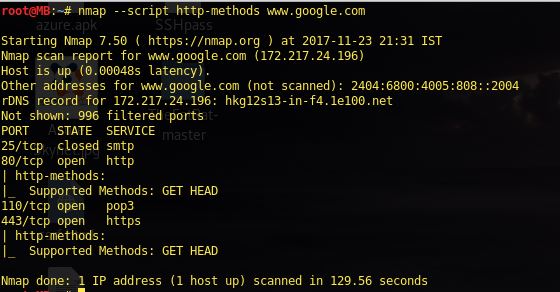
http Methods
nmap --script http-methods <target>
SMB NSE Scripts
Enumerate SMB shares
nmap --script smb-enum-shares <Target>
Enumerate SMB Users
nmap --script smb-enum-users <Target>
Brute force SMB service with password list
nmap --script smb-brute -p445 <Target>
Brute force SMB service with hashes (Hashes and usernames kept in .txt files)
nmap --script smb-brute --script-args=userdb=usernames.txt,passdb=passwords.txt <Target>
Discover SMB OS
nmap --script smb-os-discovery <Target>
Dump hashes remotely - Needs valid credentials
nmap -p 135,139,445 --script smb-pwdump --script-args-smbuser=USERNAME,smbpass=PASSWORD <Target>
Shows logged in sessions - Needs valid credentials
nmap --script smb-enum-sessions -p445 <Target>
SQL Servers
MSSQL Server info
nmap -p1433 --script ms-sql-info <Target>

MSSQL - Bruteforce
nmap -p1433 --script ms-sql-brute <Target>

MSSQL - Bruteforce With custom list
nmap -p1433 –script ms-sql-brute –script-args userdb=/var/usernames.txt,passdb=/var/passwords.txt <target>
MSSQL - Bruteforce With empty/null password
nmap -p1443 --script ms-sql-empty-password <Target>

MSSQL - Discover which user has access to which db (Credentials Needed)
nmap -p1443 --script ms-sql-haddbaccess --script-args mssql.username=USERNAME <target>

MSSQL - List Tables (Credentials Needed)
nmap -p1443 --script ms-sql-tables --script-args mssql.username=USERNAME <Target>

MSSQL - SQL Server xp_cmdshell (Run OS command via xp_cmdshell) This will just print the CMD output default (Ipconfig)
nmap -p1433 --script ms-sql-xp-cmdshell --script-args mssql.username=USERNAME <Target>

To Specify the command to use you need to us the arg “–script-args=ms-sql-xp-cmdshell.cmd=‘COMMAND’” As shown as an example bellow
nmap -p1433 --script ms-sql-xp-cmdshell --script-args=ms-sql-xp-cmdshell.cmd='net users',mssql.username=USERNAME <Target>

Recon
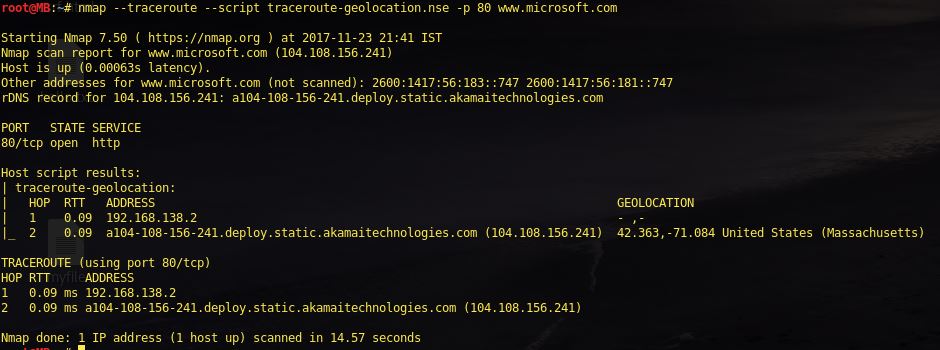
Find Information about IP address
nmap --traceroute --script traceroute-geolocation.nse -p 80 <Target>
DNS Brute Force
nmap -p 80 --script dns-brute.nse <Target>

Find Hosts on IP
nmap -p 80 --script hostmap-bfk.nse <Target>
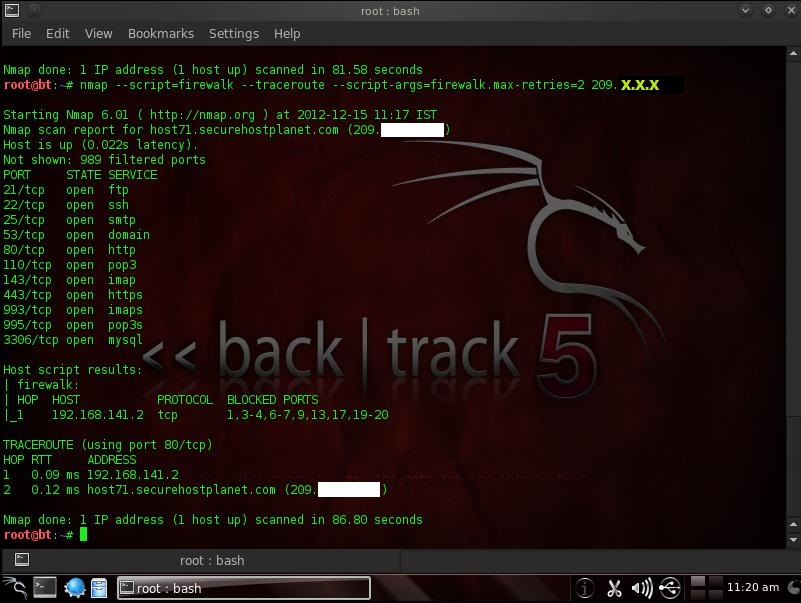
Firewalk - Tries to discover firewall rules using an IP TTL expiration technique.
nmap --script firewalk --traceroute --script-args=firewalk.max-retries=1 <Target>
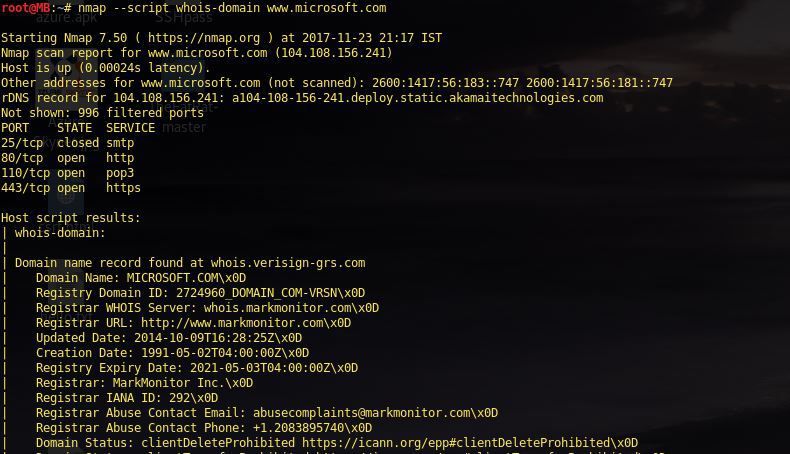
whois domain
nmap --script whois-domain <target>
Shodan API - API Key can be specieid in args or by editing the NSE script itself (Shown in video)
nmap --script shodan-api --script-args 'shodan-api.target=x.y.z.a,shodan-api.apikey=SHODANAPIKEY'
Custom NSE Script repositories
Paulino Calderon (cldrn) - Network security specialist | Open Source contributor | @nmap NSE developer | Chapter leader of @owasp_riviera
https://github.com/cldrn/nmap-nse-scripts/tree/master/scripts
John Bond - b4ldr https://www.linkedin.com/in/john-bond-189887a/
https://github.com/b4ldr/nse-scripts
Peter - peter-hackertarget https://hackertarget.com
https://github.com/peter-hackertarget/nmap-nse-scripts
Sanoop Thomas - s4n7h0 " Let the passion be your purpose. " Security guy, Researcher, Speaker, Creator of Halcyon IDE
https://github.com/s4n7h0/NSE
Aeris Secure - Open source projects from Aeris Secure, mostly relating to information security and security testing
https://github.com/aerissecure/nse
Recent Posts
Tags
Categories
Active directory Burpsuite Cheatsheet Crackmapexec Empire Events Exploit File transfer Iis Implants Kcsec Kerberos Kernelpop Ksec Ksec snapshot Lab Metasploit Metasploitable Msfvenom Netcat Nfc & rfid Nikto Nmap Pivoting Privilege escalation Proxmark Proxychains Redteam Responder Rubber ducky Shells Sqlmap Sshutle Thefatrat Toolkit Webapp Windows domain Xss