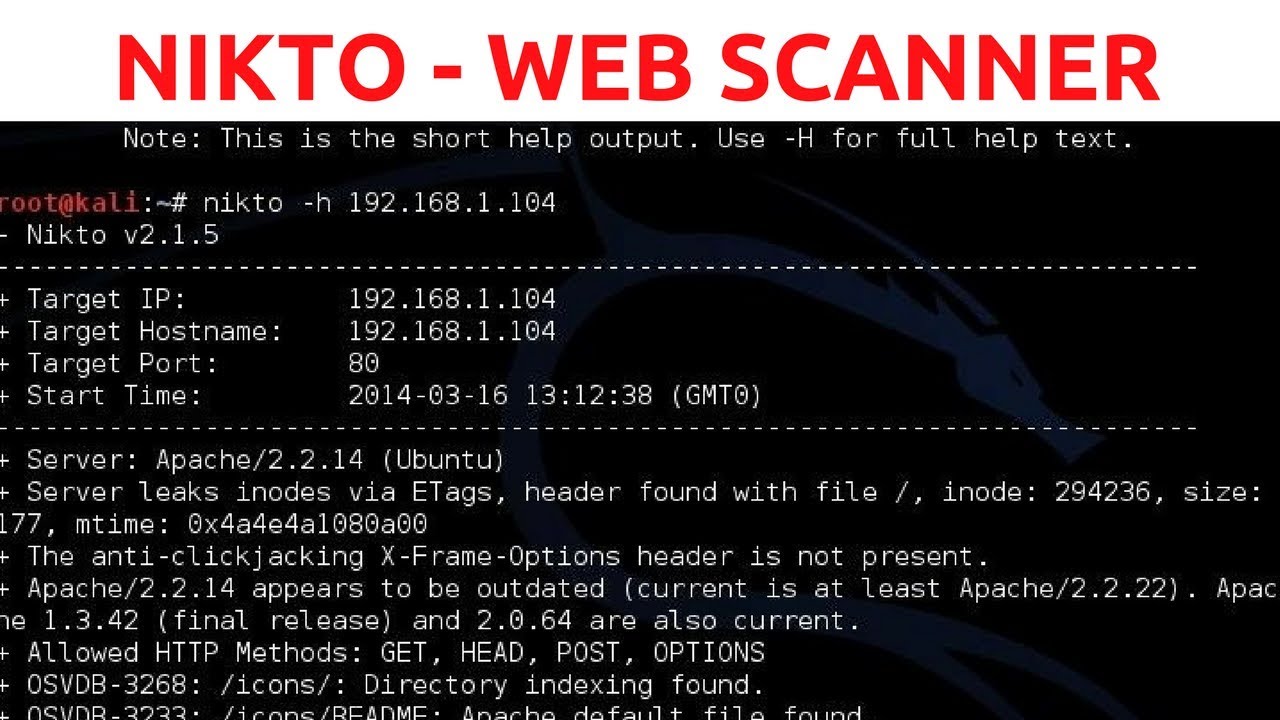
Nikto web server scanner
Nikto web server scanner - https://cirt.net/Nikto2
Full documentation - https://cirt.net/nikto2-docs/
What is nikto
Nikto is an open source scanner written by Chris Sullo and you can use with any web servers (Apache, Nginx, IHS, OHS, Litespeed, etc). Sounds like a perfect in-house tool for web server scanning.
Nikto scan for over 6700 items to detect misconfiguration, risky files, etc and some of the features include;
- You can save report in HTML, XML, CSV
- It supports SSL
- Scan multiple ports on the server
- Find subdomain
- Apache user enumeration
- Checks for outdated components
- Detect parking sites
How to use Nikto
If you’re going to exploit websites and Pentest, Before that you need to make sure what vulnerabilities that site containing and that can be done through information gathering. Trying to attack with various exploits without finding any vulnerabilities isn’t an professional way.
There are a number of tools and applications which is used to find vulnerabilities in websites, but Nikto is one of my favorite tool to examines a website and reports back the potential vulnerabilities that found, which I could use to exploit or hack the site.
The Nikto webserver scanner is an security audit tool which will test for over 6700 items of possible security issues on a website. Including the IP, hostname, port used on service, particular dangerous files, X-SS protection, CGI directories, mis-configured services, vulnerable scripts and other issues. It is open source and structured with plugins that extend the capabilities.
Nikto is inbuilt on majority Pentesting Distro such as Kali Linux. In this tutorial, I’m going to show you how to use Nikto on Kali Linux. So, you do not need to install anything.
Lets get started!
Open terminal,
nikto
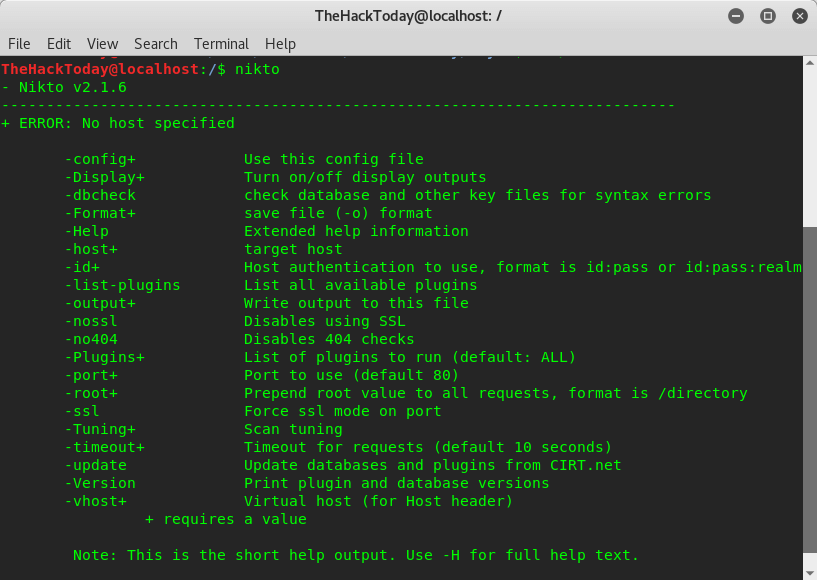
Target address Nikto allowed use the format:
HTTP Service of Typical website on default Port 80: www.thehackertoday.com
HTTPS Service of website on default Port 443: https://www.thehackertoday.com
HTTP Service IP address of website on Port 80: 10.9.17.21
There are multiple args or sytax nikto able to do. However, the simplest way is :
nikto -h $webserver
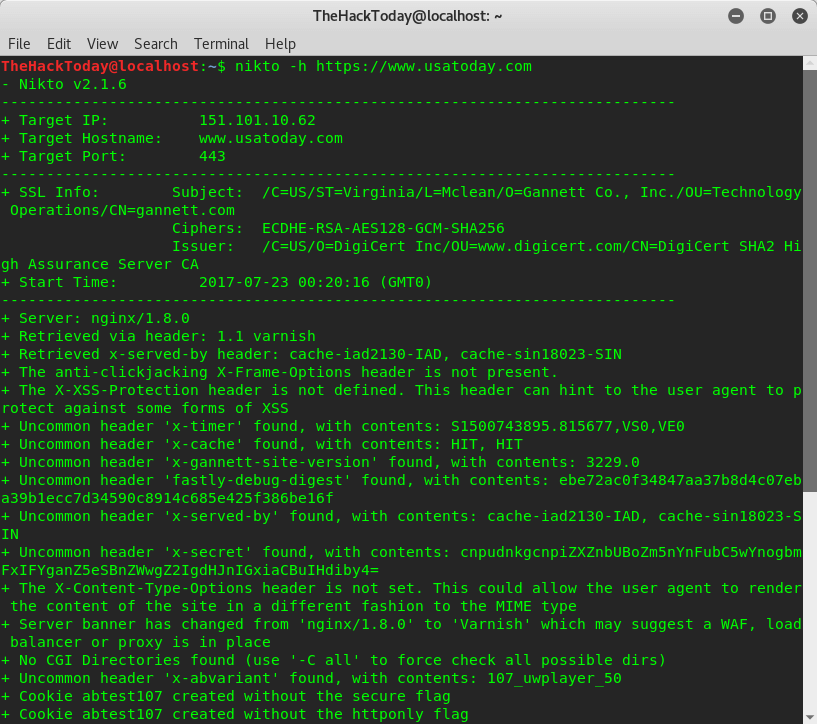
How to Find Website Vulnerabilities Using Nikto on Kali Linux
 First, Nikto tells us the server is Nginx v.1.8.0
First, Nikto tells us the server is Nginx v.1.8.0
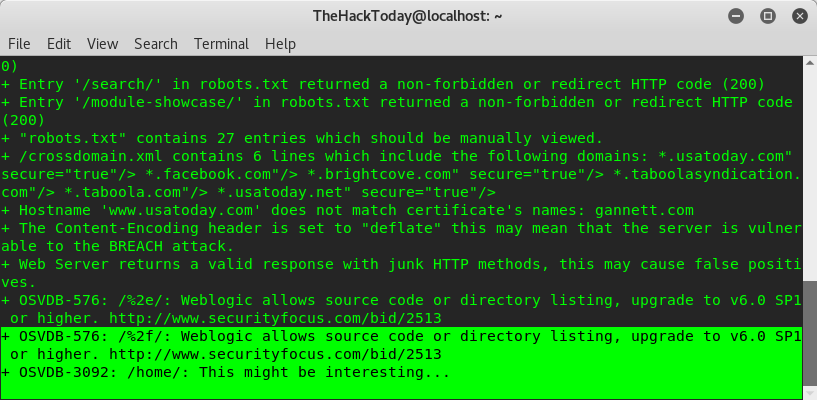
Then, near to the bottom nikto identifies a vulnerability with OSVDB prefix (Open Source Vulnerability Database). Now googling for OSVBD-576, OSVBD-3092 and here we got :
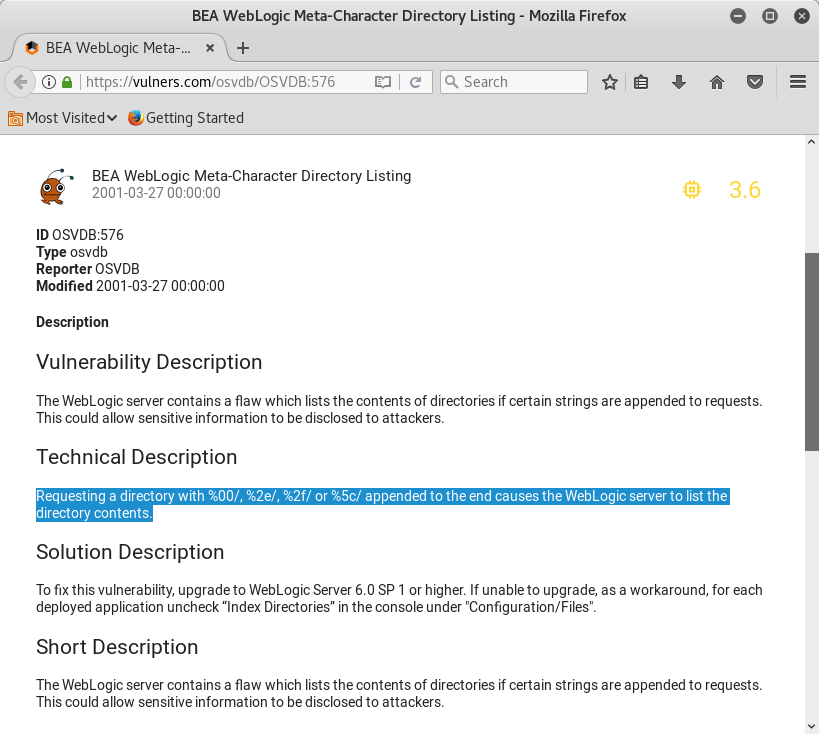
As you can see we know about our target vulnerability and through google we got a exploit method, But we’re not going to show you how to hack your target our intention is just to teach you how to do ethical hacking and report bugs. Using Nikto is simple and more efficient. If you have any questions please join our forum.
Recent Posts
Tags
Categories
Active directory Burpsuite Cheatsheet Crackmapexec Empire Events Exploit File transfer Iis Implants Kcsec Kerberos Kernelpop Ksec Ksec snapshot Lab Metasploit Metasploitable Msfvenom Netcat Nfc & rfid Nikto Nmap Pivoting Privilege escalation Proxmark Proxychains Redteam Responder Rubber ducky Shells Sqlmap Sshutle Thefatrat Toolkit Webapp Windows domain Xss