
Proxmark 3 Dev - Tag enumeration
Basic tags
There are a few tags that come with the proxmark3 dev.
HF Tags - 13.56Mhz
- Mifare 1 S50 white PVC card
- Mifare Ultralight white PVC card
- Mifare UID white PVC card (Chinese Magic Card)
LF Tags - 125Khz
- HID tag
- T5577 tag
- EM4X tag
EM4XXX
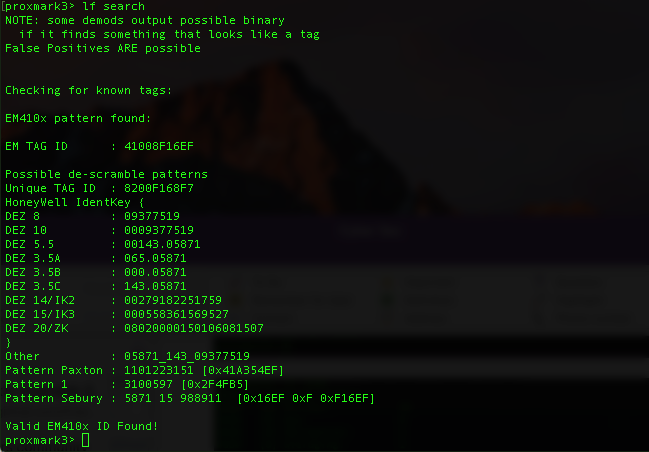
so by running “lf search” proxmark will find any lf tag by the antenna.
lf search
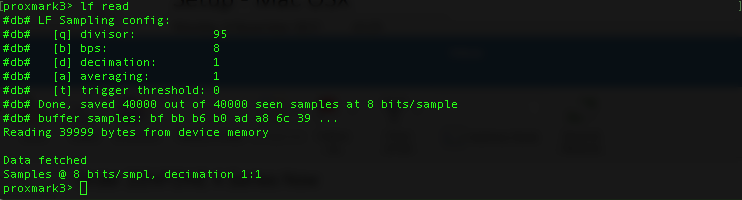
we can also run “lf read” to read the tag info.
lf read
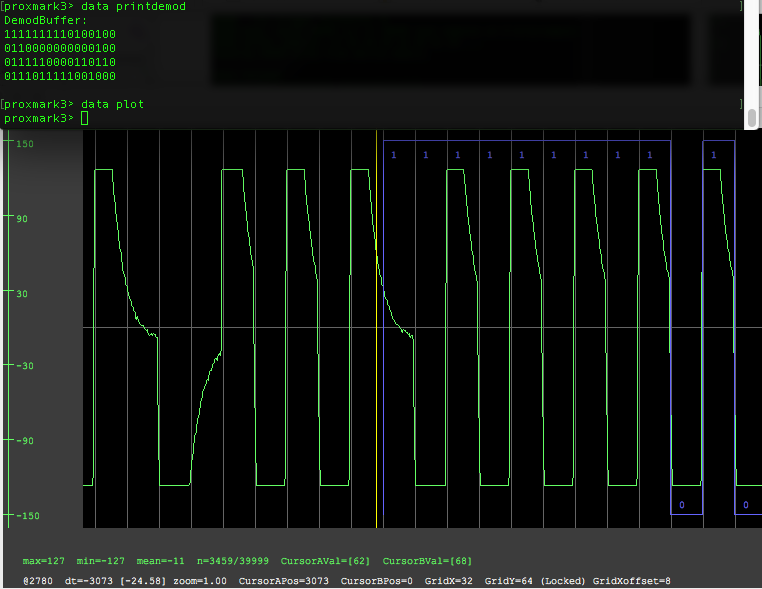
Next let us see the full raw binary for the tag we just read, so issue a data printdemod to output the demodulated tag buffer from the previous demodulation command (lf search)
Then do a data plot to open the graph
data printdemmod
data plot
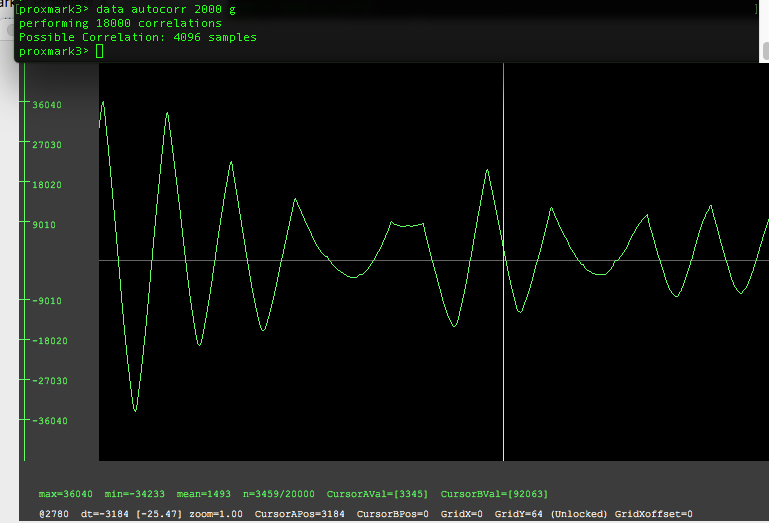
The proxmark client offers a simple autocorrelation feature
data autocorr 2000 g
Mifare s50
High Frequency tag search
hf search
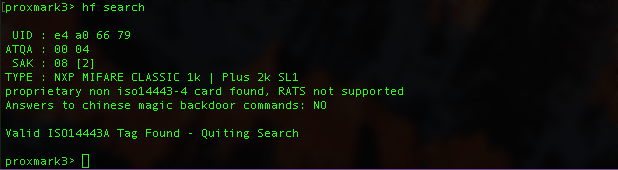
This command executes the ISO 14443-3 Type A anticollision procedure and prints out the info gathered from the card’s responses.
hf 14a reader
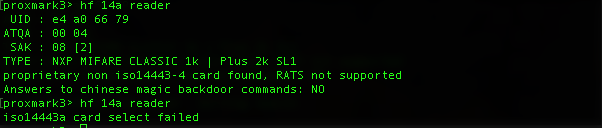
This essentially does nothing else than hf 14a reader except that it only prints out the card’s UID and can do so an arbitrary number of times unattended. This is useful e.g. to analyze the RNG of a card that generates random UIDs. The output is encased in timestamps to indicate the duration of the complete procedure.
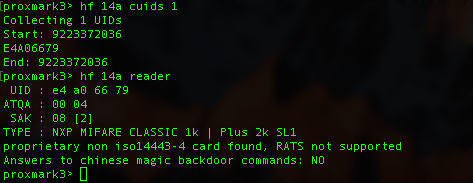
hf 14a cuids 1
Recent Posts
Tags
Categories
Active directory Burpsuite Cheatsheet Crackmapexec Empire Events Exploit File transfer Iis Implants Kcsec Kerberos Kernelpop Ksec Ksec snapshot Lab Metasploit Metasploitable Msfvenom Netcat Nfc & rfid Nikto Nmap Pivoting Privilege escalation Proxmark Proxychains Redteam Responder Rubber ducky Shells Sqlmap Sshutle Thefatrat Toolkit Webapp Windows domain Xss