KSEC Snapshot - Database disclosure
I wanted to spend a bit of time performing some OSINT to show people what’s being leaked online. As part of this series “KSEC Security snapshot” we bring you “Scrutinize your security”. A short glance into how security systems can be vulnerable. That’s right .. Your security solutions are ones compromising your networks, assets and integrity.
Which is the whole purpose of a security system is to make you safe … Not the opposite. So maybe after this series, you wont trust anything. Not even water ! Who knows !
In the first snapshot we located Cameras & webcams.In the second snapshot, we used shodan and other online tools to track marine vessels. That are being leaked online and track their movement.
So by using shodan, we can browse common databases - https://www.shodan.io/explore/category/databases
Query URLS
Some example querys allow us to easily select different databases from a quick target selection.
MySQL: https://www.shodan.io/search?query=product%3AMySQL MongoDB: https://www.shodan.io/search?query=product%3AMongoDB PostgreSQL: https://www.shodan.io/search?query=port%3A5432+PostgreSQL
Quick look at common databases
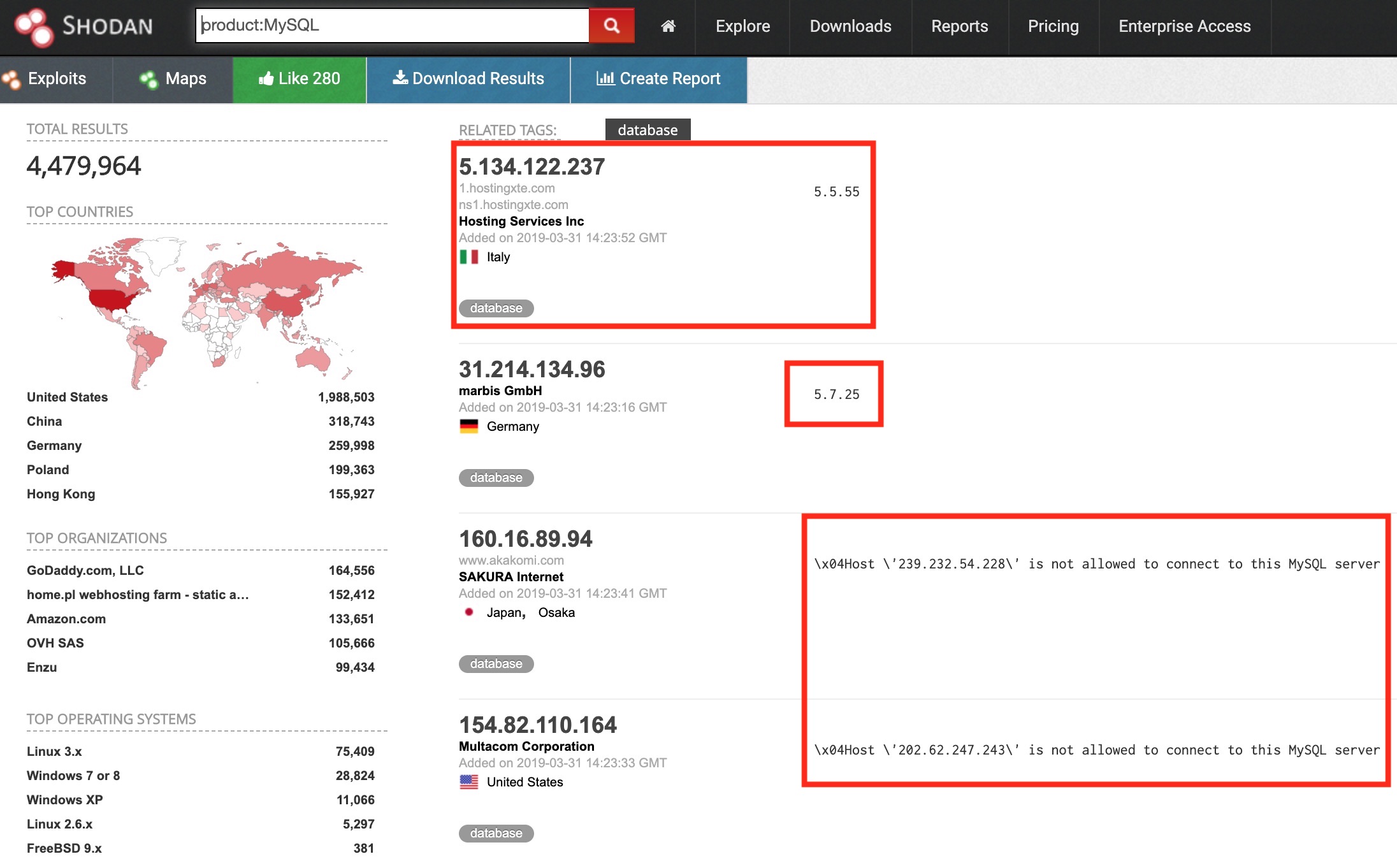
The following is an example search for exposed MySQL databases. This reveals the IP Geo location, version information but also some errors. These show that access whitelisting has been put in place, so despite being open to the internet, they’re not publicly accessible.
You can also see that there’s a total of nearly 4.5 Million MySQL Datbases being listed in shodan.
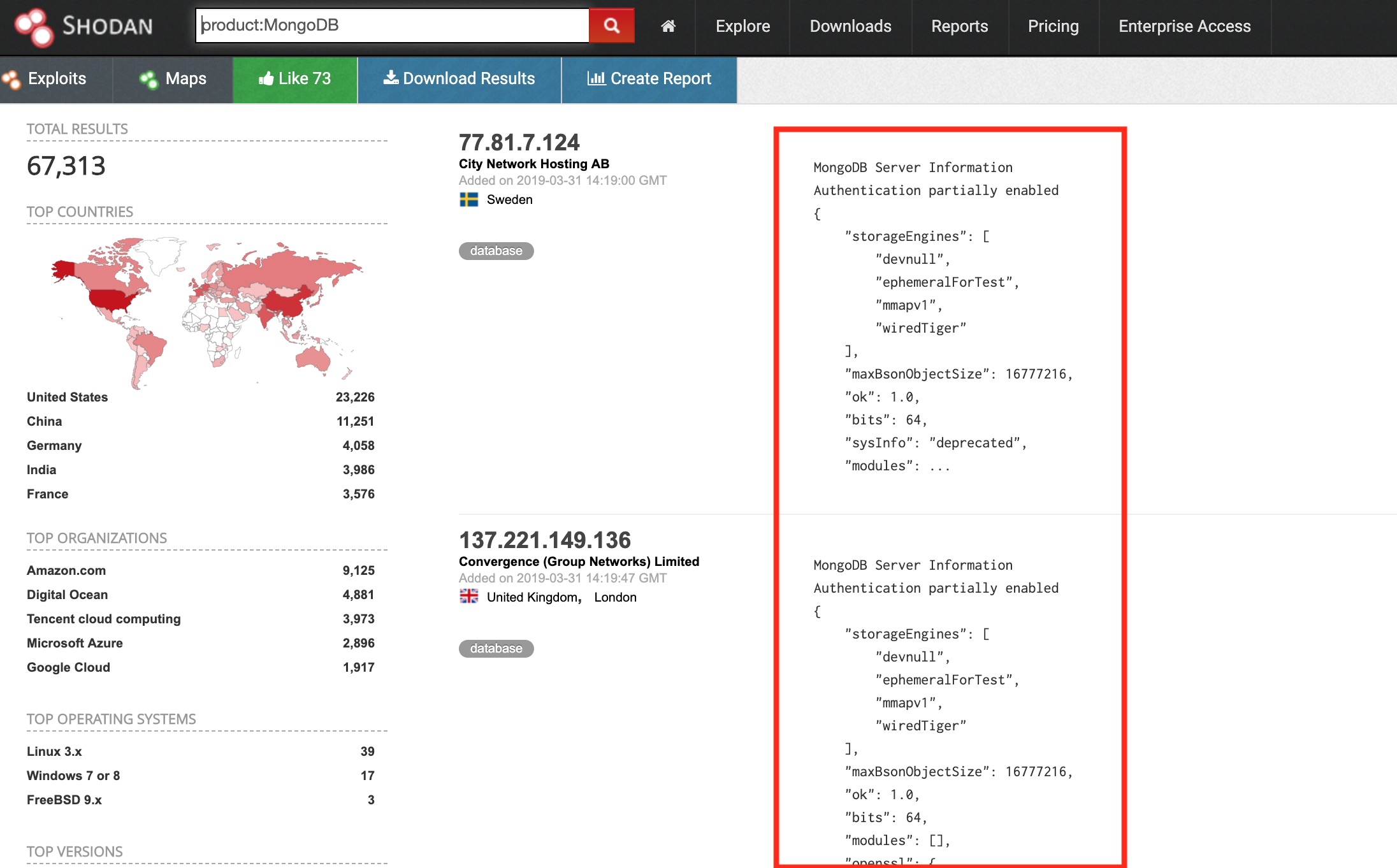
Below is a quick MongoDB search, these pull back a bit more information regarding the underlying service. Despite only 67.3k being exposed, they a very commonly breached database.
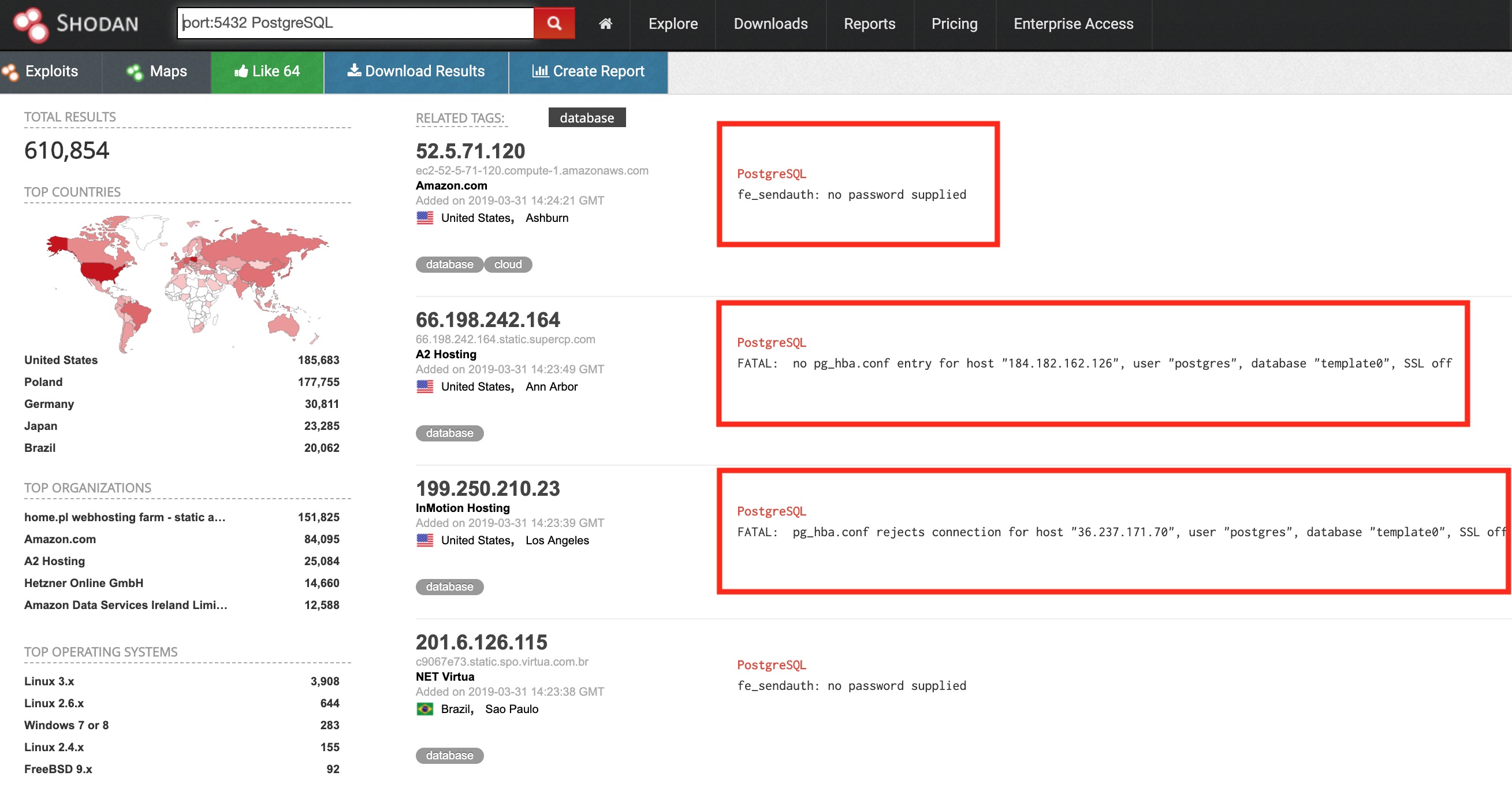
Then we’ve got PostgreSQL which has over 610K stored within shodan. The following shows more whitlisting error but also a no password error. This means that attackers could bruteforce the service until valid credentials have been found.
Digging deeper into exposed services
So far we’ve got millions of exposed without proper whitelisting and all disclosing service enumeration. Lets see if we can get something more… A quick search for Riak on its default port 8087 brings back 200 results.
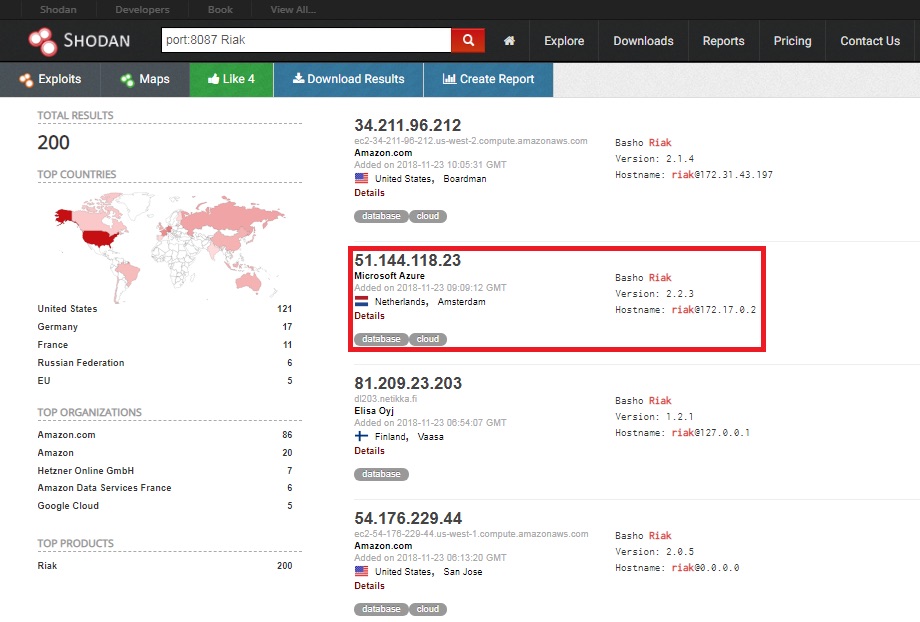
The following result appears to be hosted in Amsterdam but also has some other open ports. SSH running on its default port 22, along with some known Riak ports.
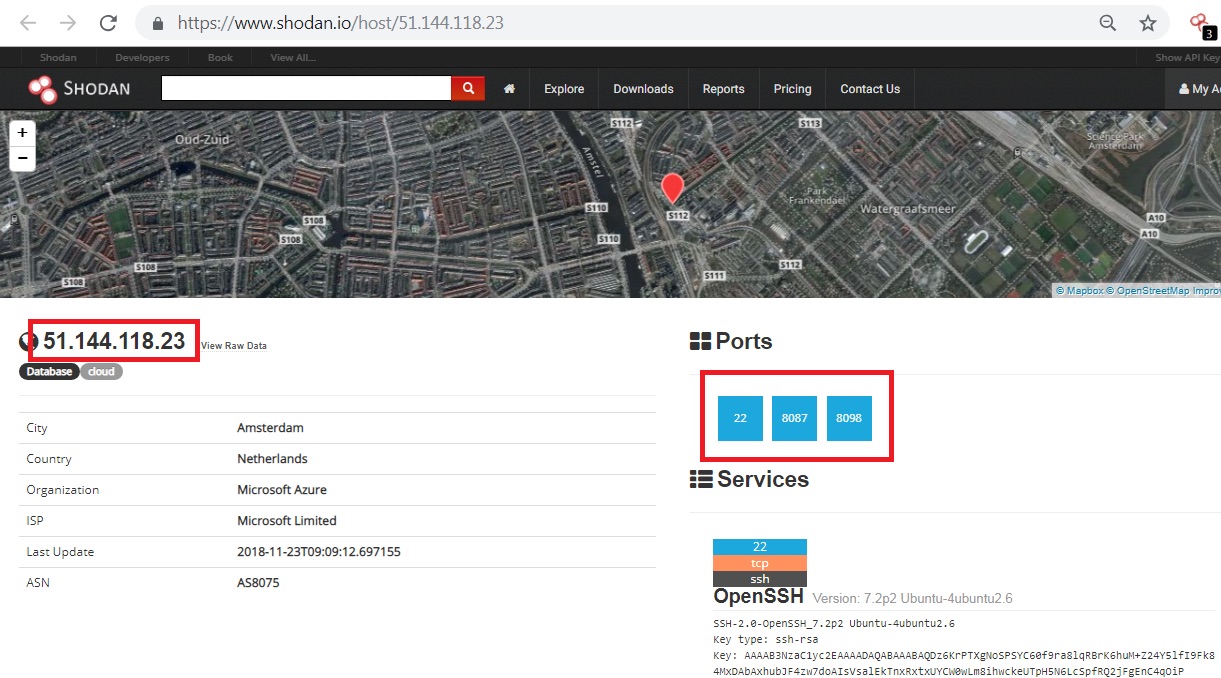
Looks like we’ve landed on the admin page of a Riak database ..unauthenticated.
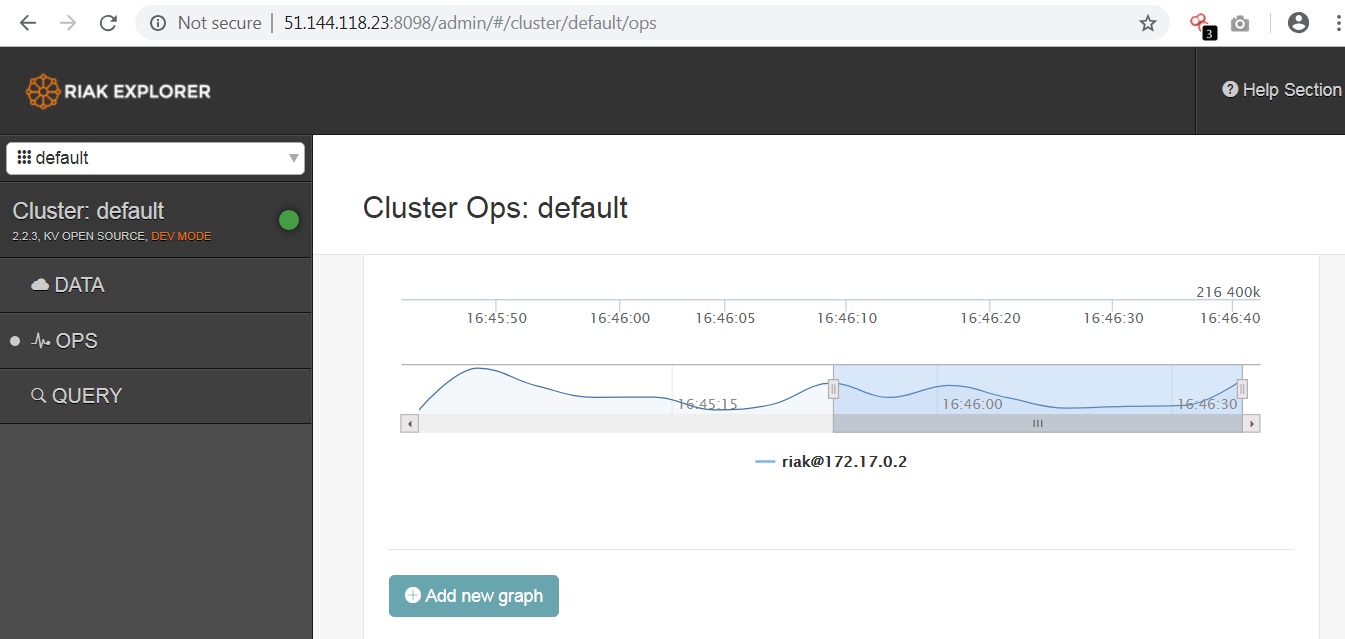
This allows us to create new graphs to retrieve and view host data such as memory processes.
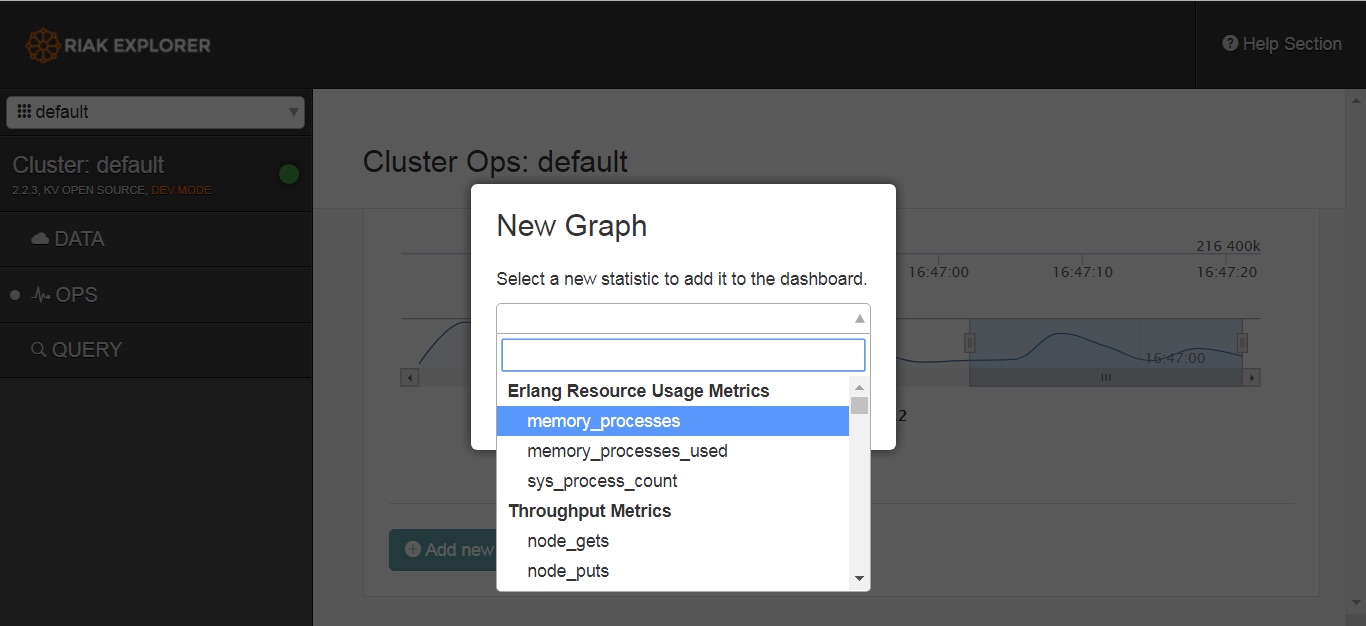
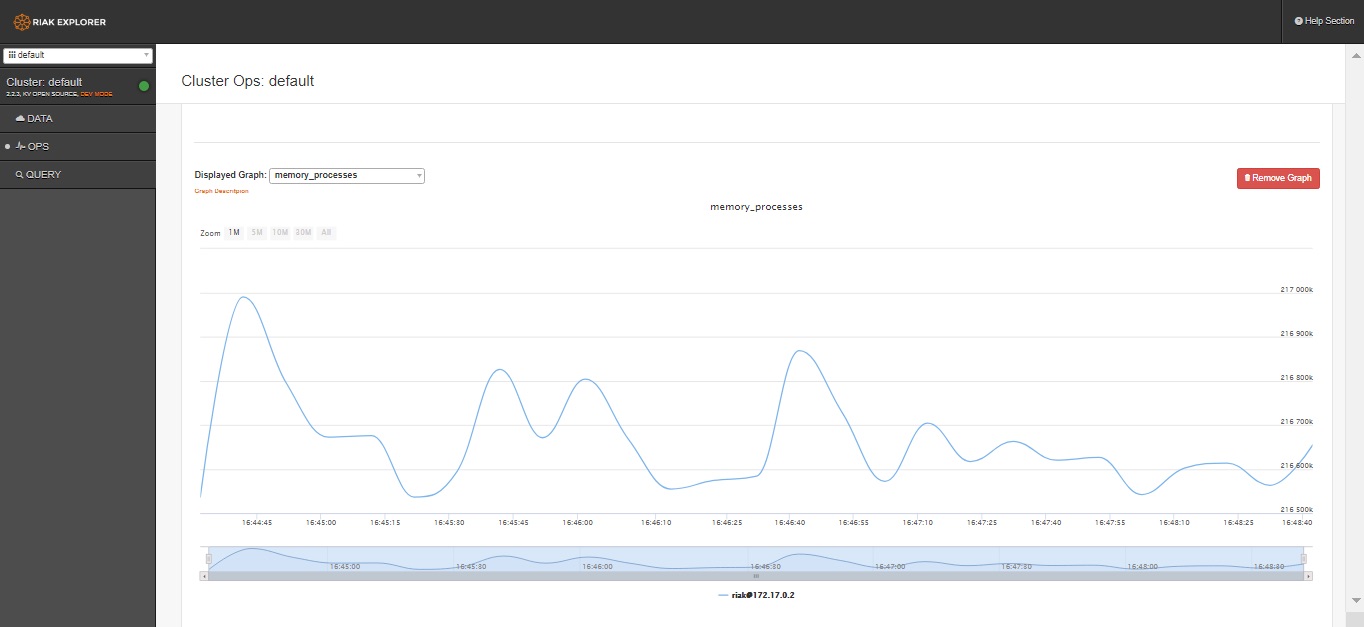
It also allows us access to the hosts configuration, stats and logs. To a potential attacker or pentester, this is very handy. So make sure yours isn’t accessible !
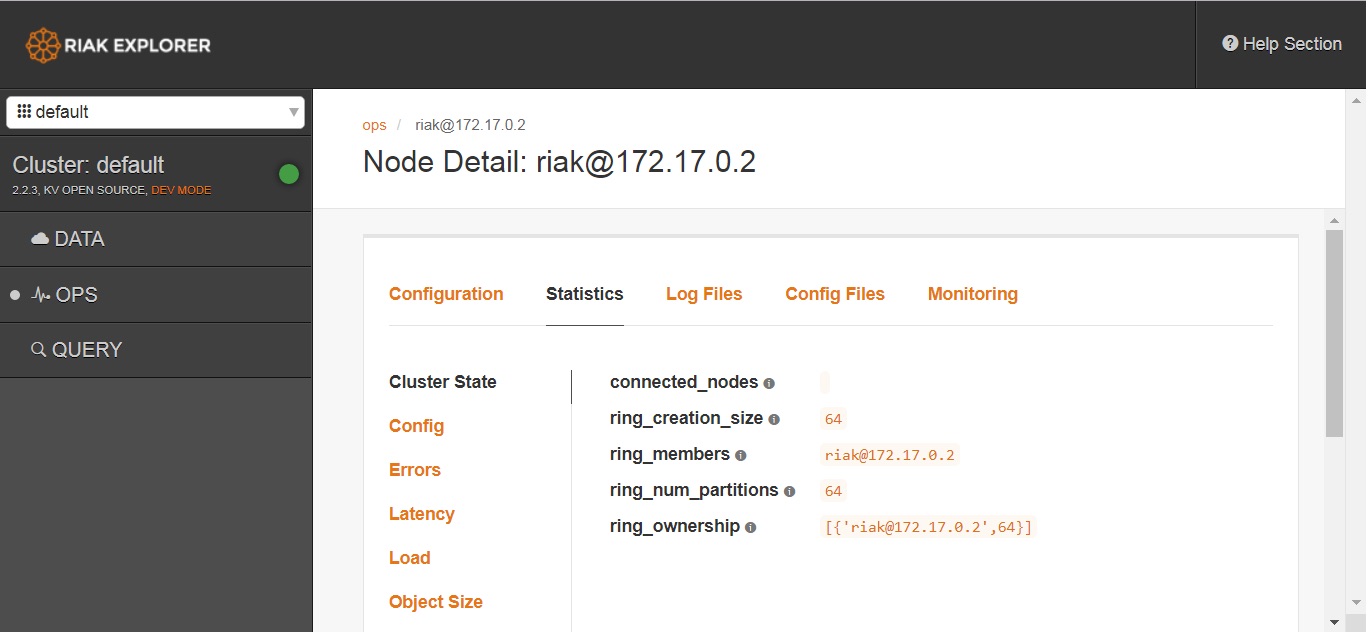
Worst case scenarios
So quick look at another common database .. CouchDB. This shows some nice version information with nearly 5.5K hosts being listed.
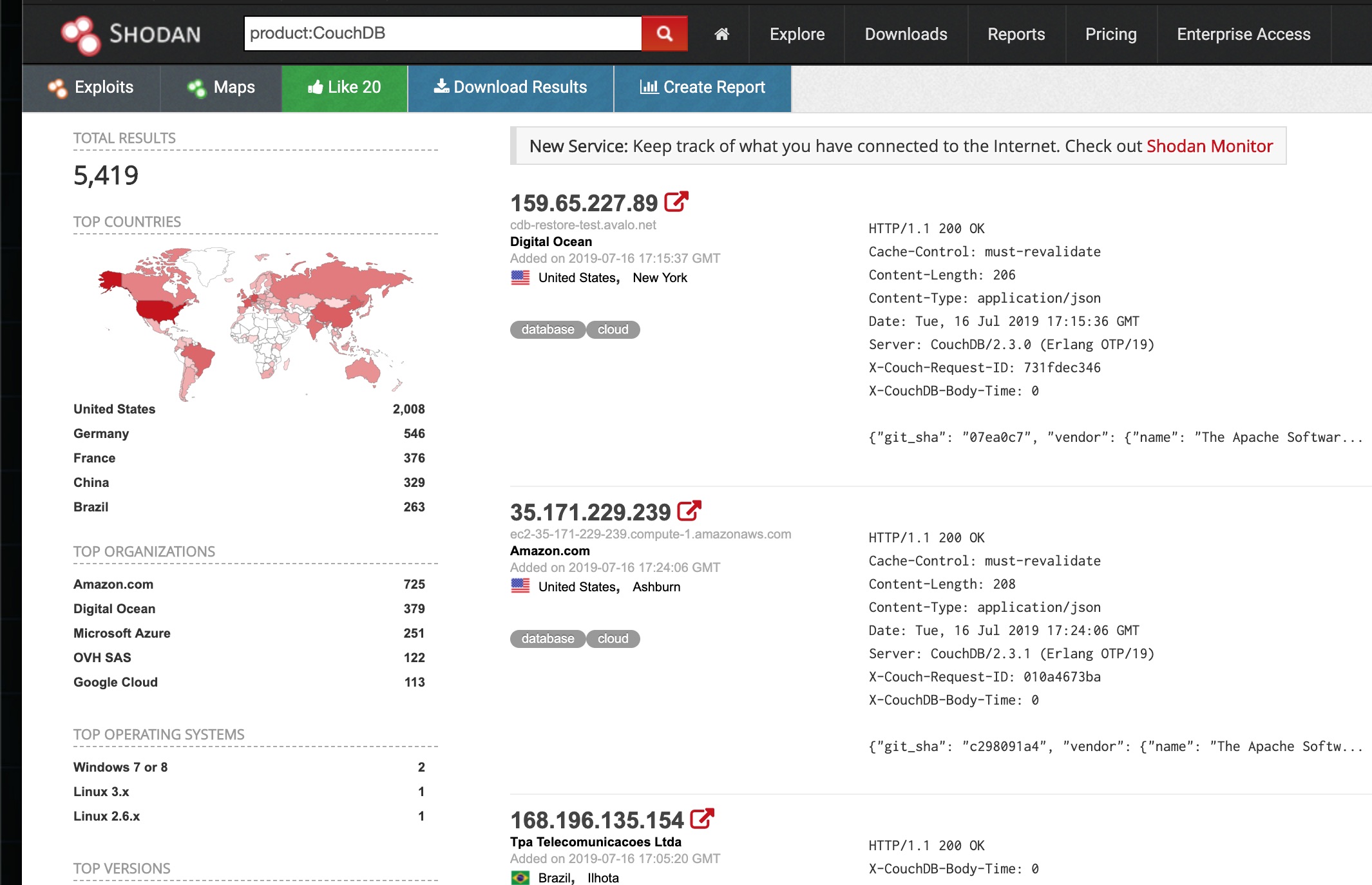
Then I see this one host … couch ouch. That’s a bad pun but not as bad as their setup. The fact shodan has listed this as compromised is bad news for them. Lets see why ..
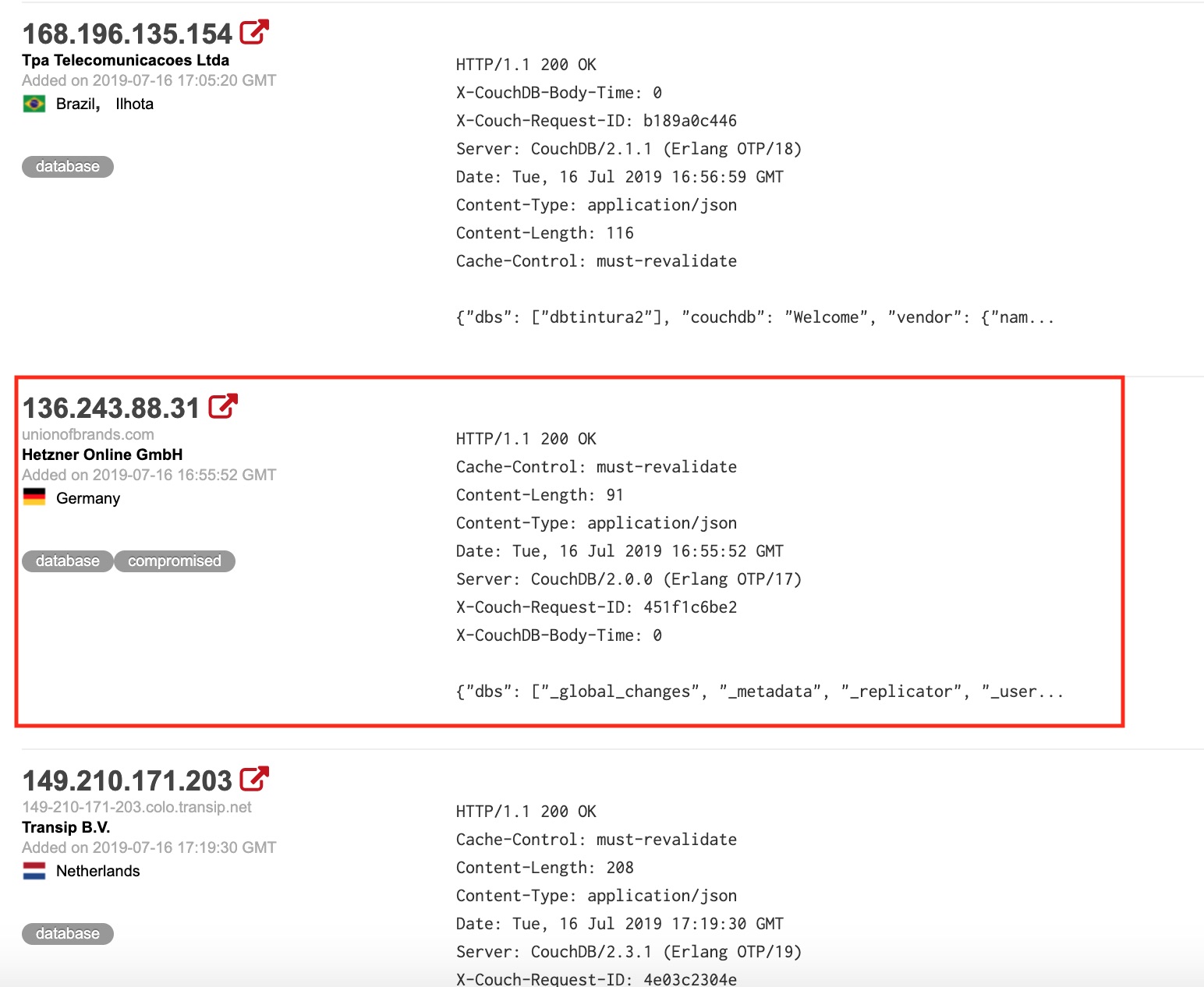
So this turned from “couch ouch” to “couch fucked”.. Those are some bad services to have exposed. RIP to them …
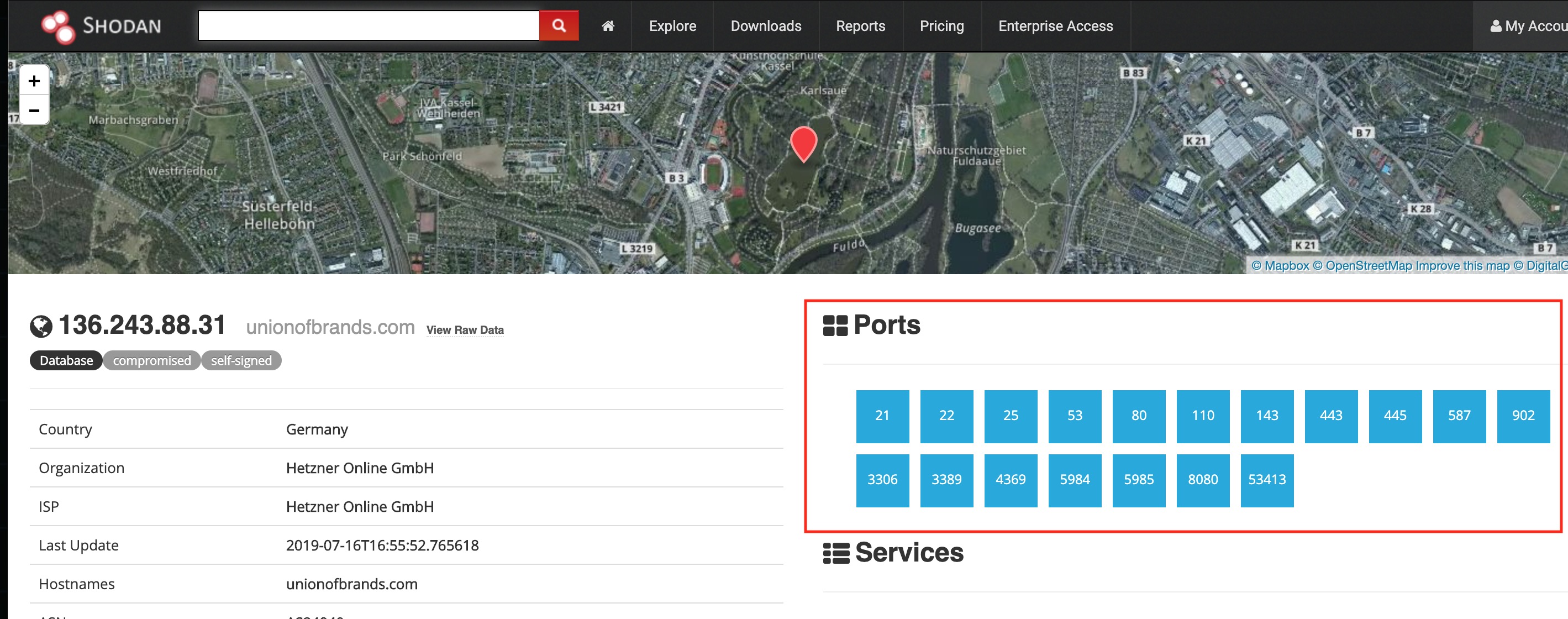
Yeah Filezilla server ..
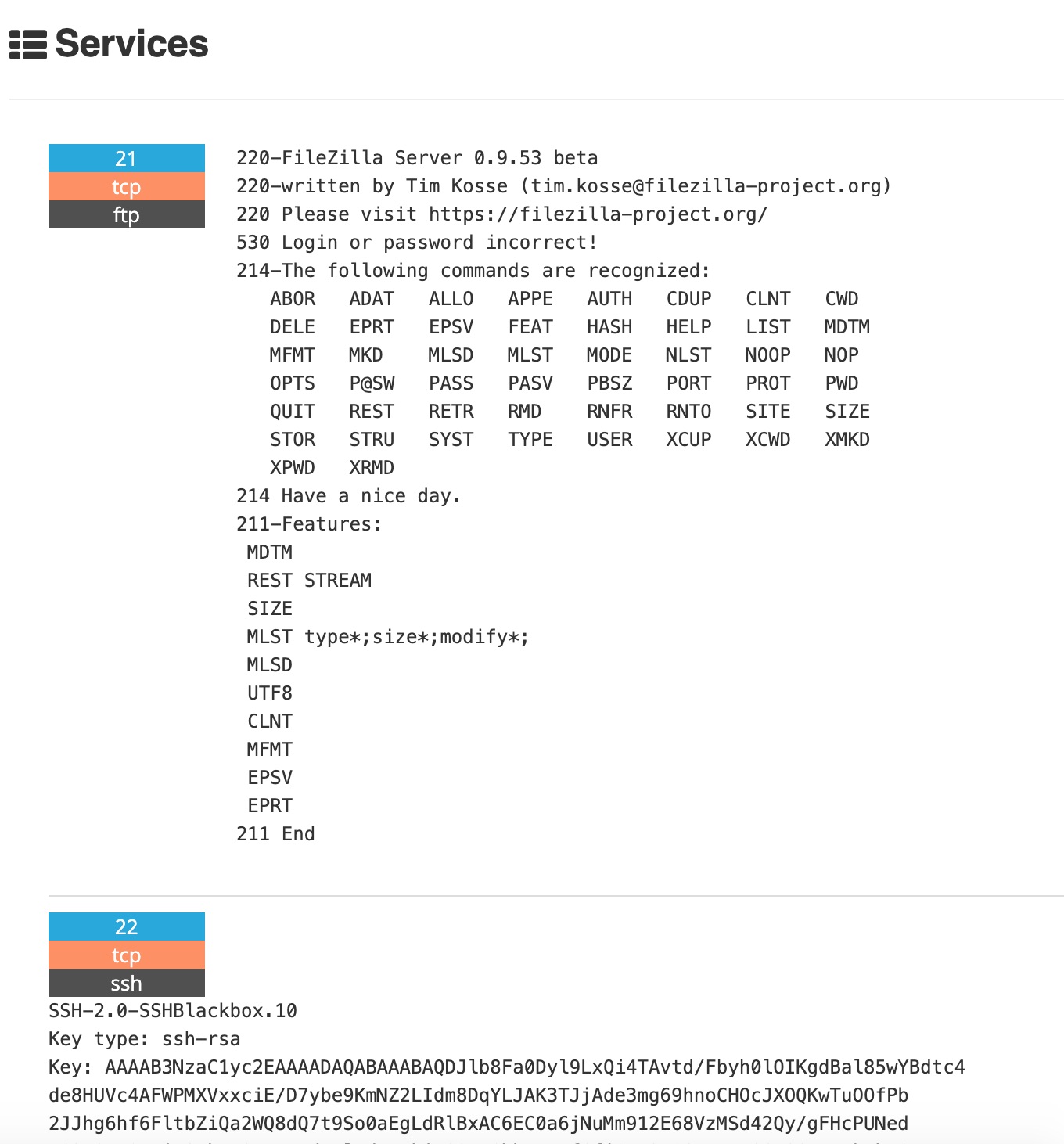
Oh looks like they’ve been compromised alright. Seems some new users accounts have been added !
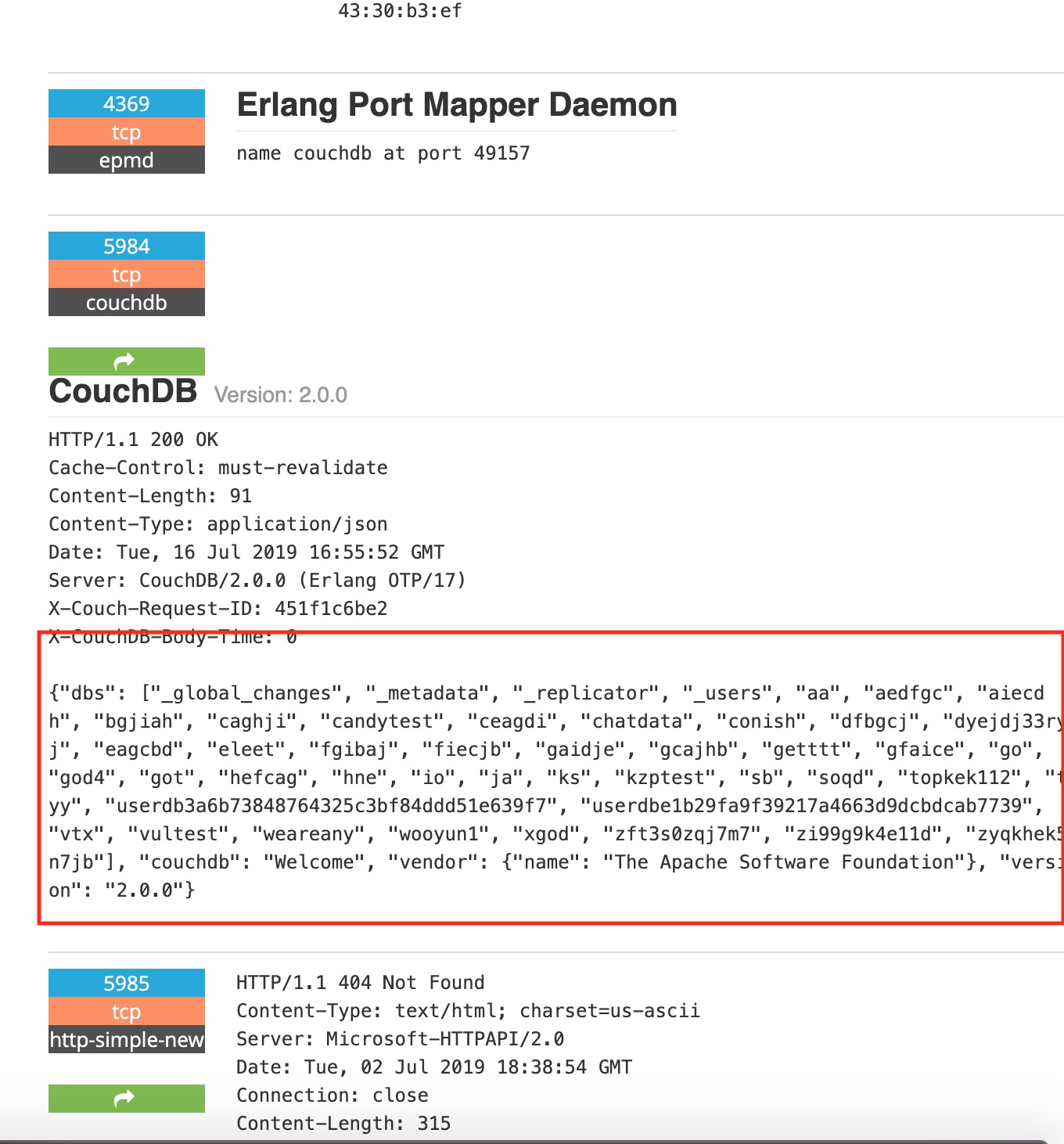
Oh that note .. It’s still very clear that people are still have massive misconfiguration issues and databases are no exception to this still.
Recent Posts
Tags
Categories
Active directory Burpsuite Cheatsheet Crackmapexec Empire Events Exploit File transfer Iis Implants Kcsec Kerberos Kernelpop Ksec Ksec snapshot Lab Metasploit Metasploitable Msfvenom Netcat Nfc & rfid Nikto Nmap Pivoting Privilege escalation Proxmark Proxychains Redteam Responder Rubber ducky Shells Sqlmap Sshutle Thefatrat Toolkit Webapp Windows domain Xss