KSEC Snapshot - Marine Vessels
I wanted to spend a bit of time performing some OSINT to show people what things are being leaked online. As part of this series “KSEC Security snapshot” we bring you “Scrutinize your security”. A short glance into how security systems can be vulnerable. That’s right .. Your security solutions are ones compromising your networks, assets and integrity.
Which is the whole purpose of a security system is to make you safe … Not the opposite. So maybe after this series, you wont trust anything. Not even water ! Who knows !
In the first snapshot we located Cameras & webcams.In this second snapshot, we’re going to use shodan and other online tools to track marine vessels (Ships/ boats). That are being leaked online and track their movement.
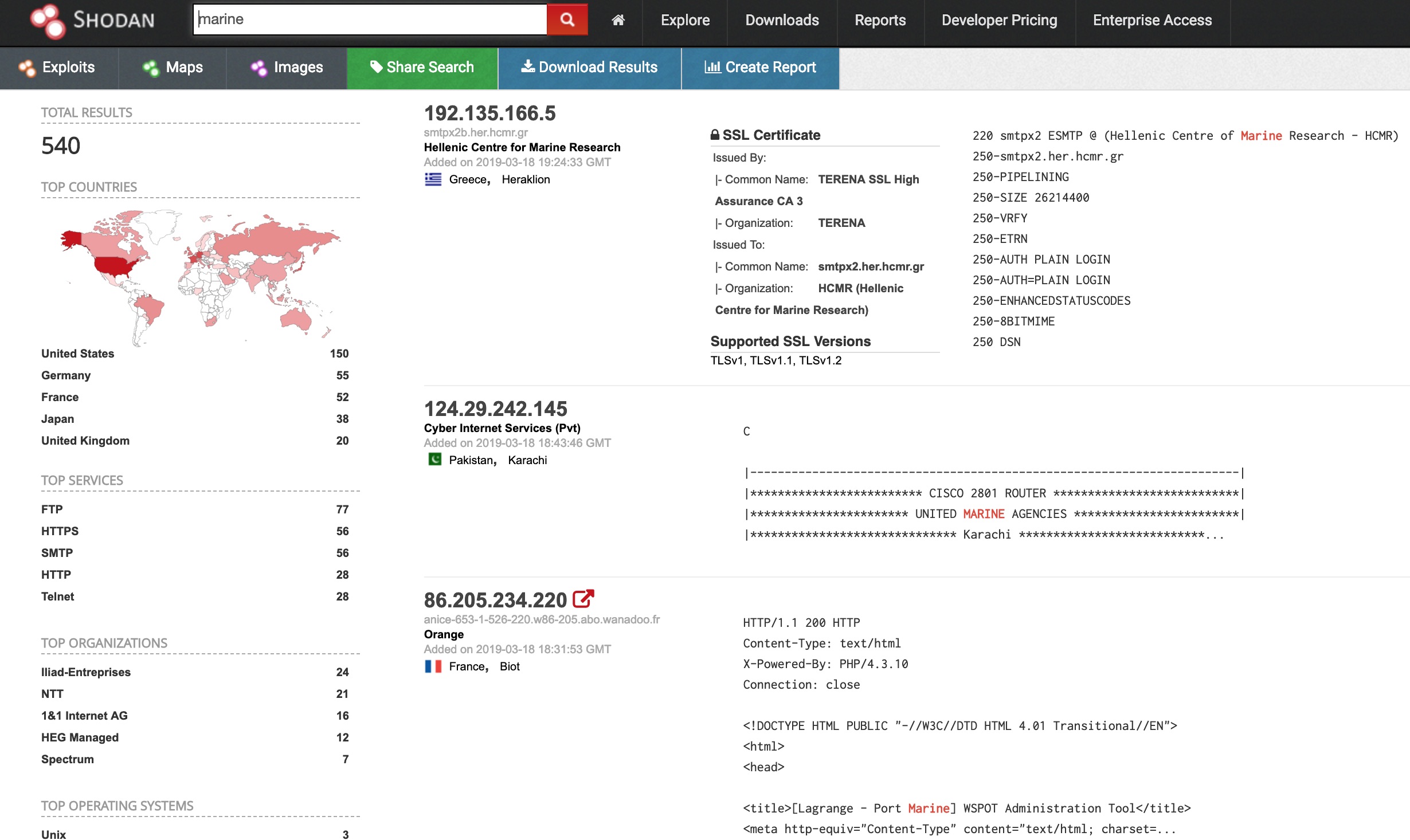
A Quick search for marine shows some interesting results.
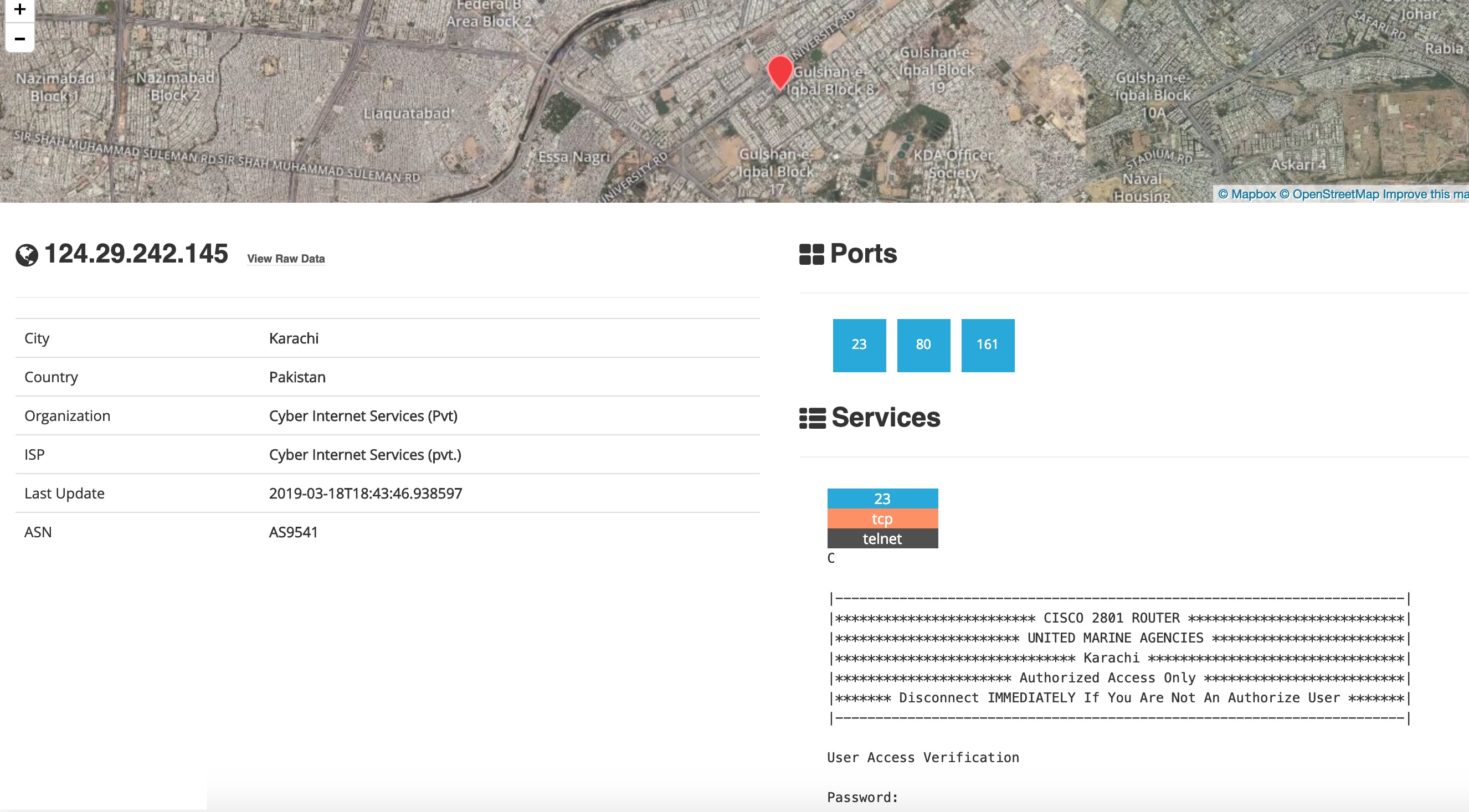
Nice FTP banner and RDP Login screen.
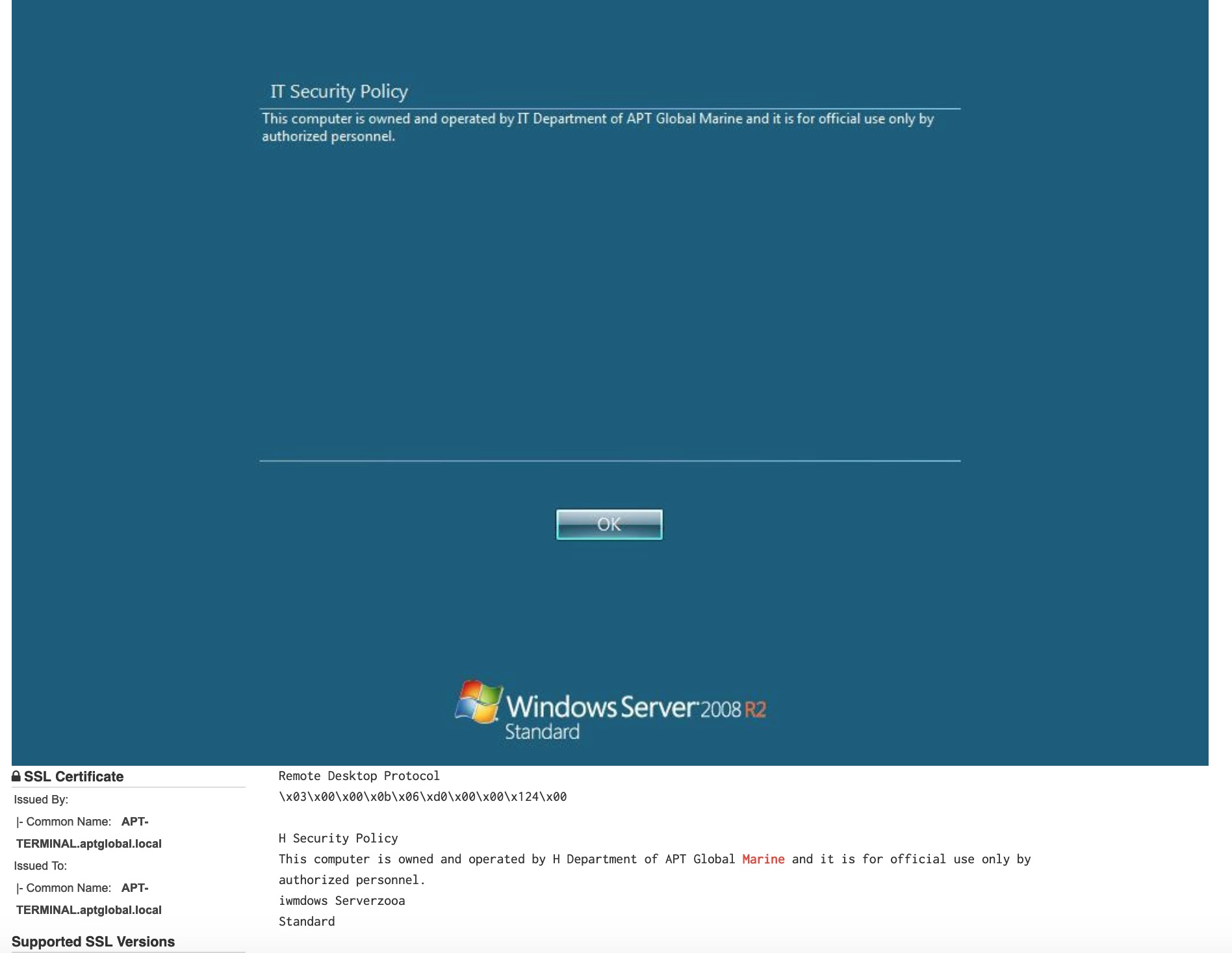
Some serious fails here … SMBv1 open to the internet let alone the rest.
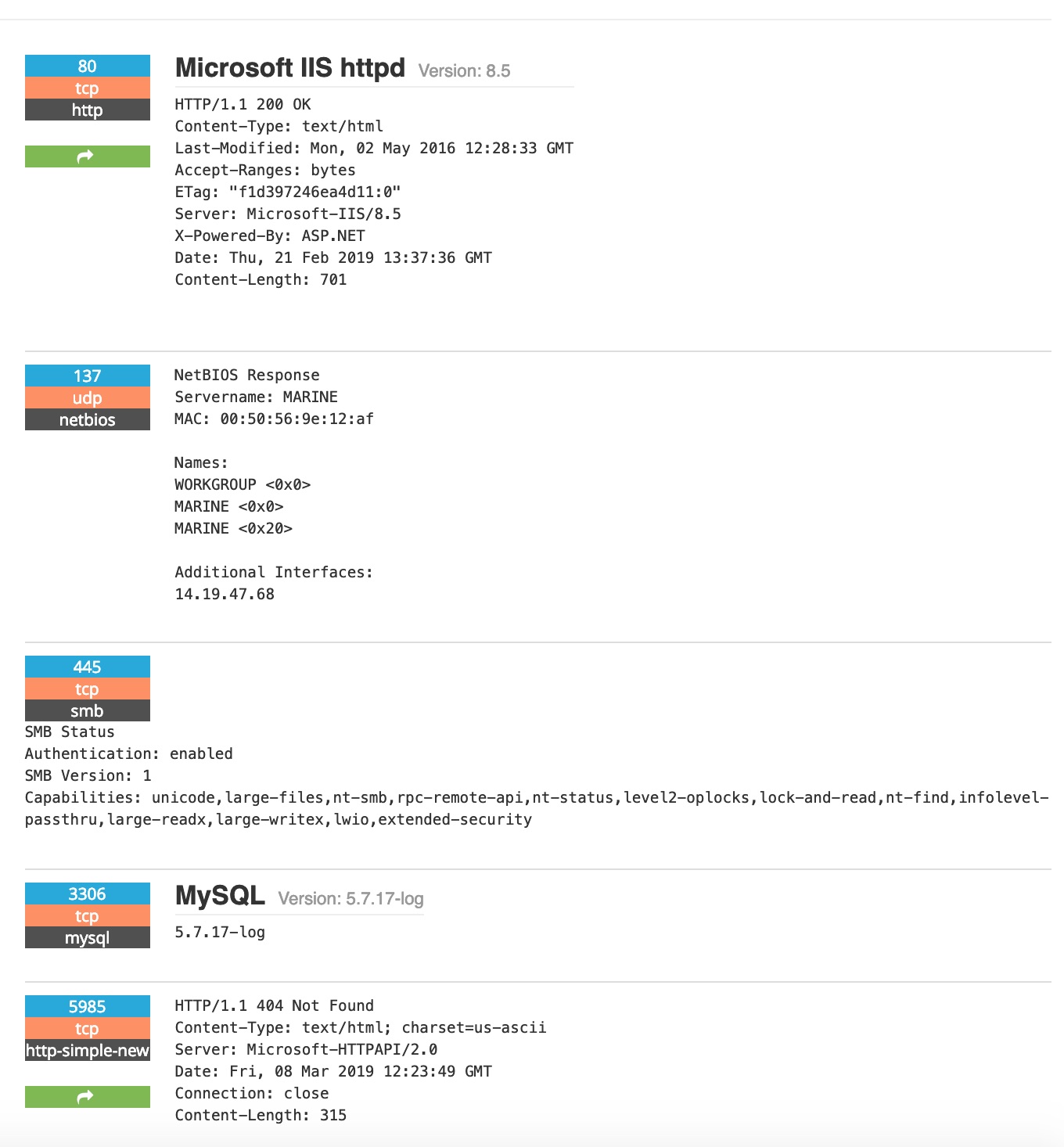
Boats/ships uses VSAT (Very-Small-Aperture Terminal) which uses satellite communication to communicate with the internet. VSAT uses IPv4 and can be found running on a range of ports.
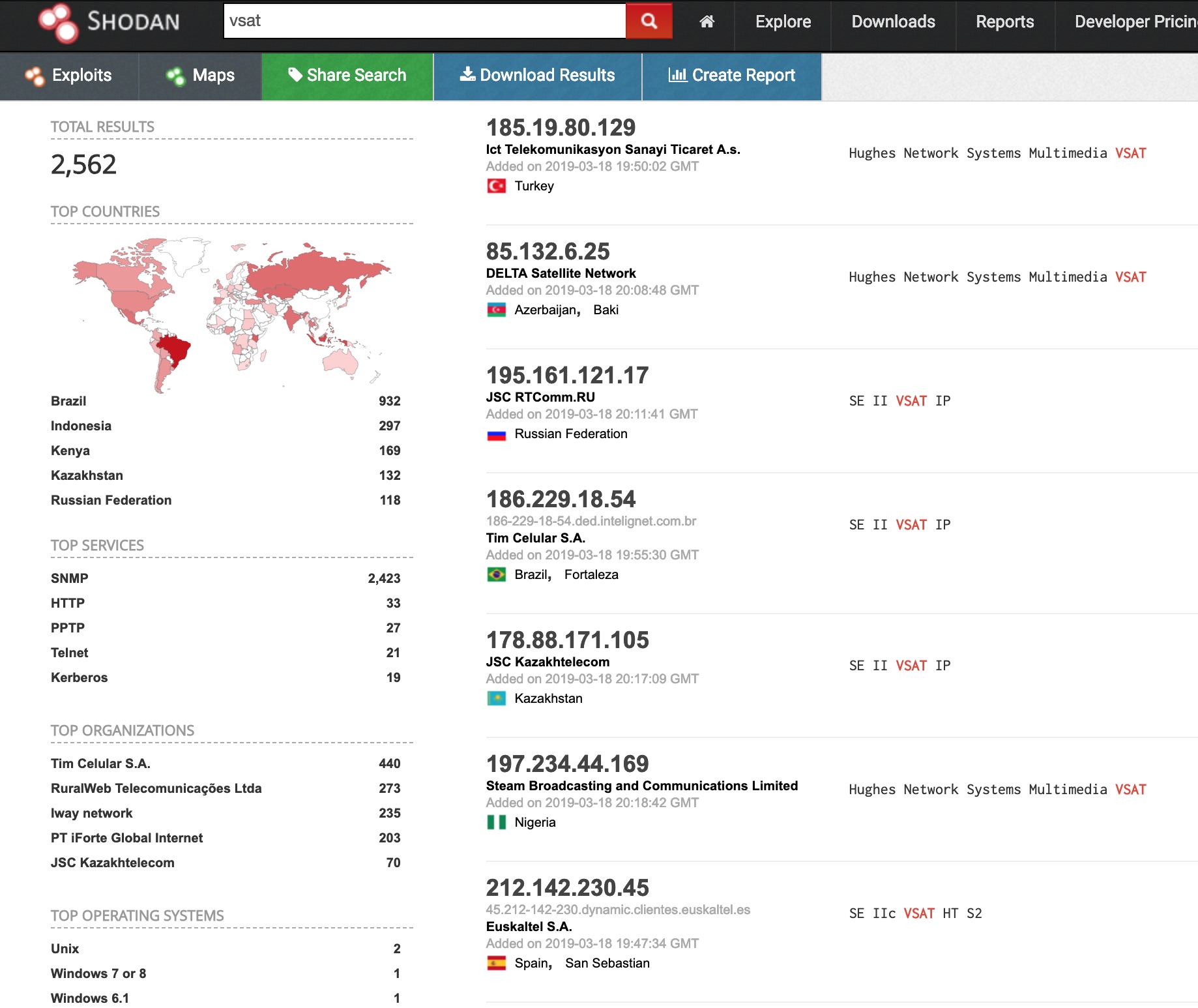
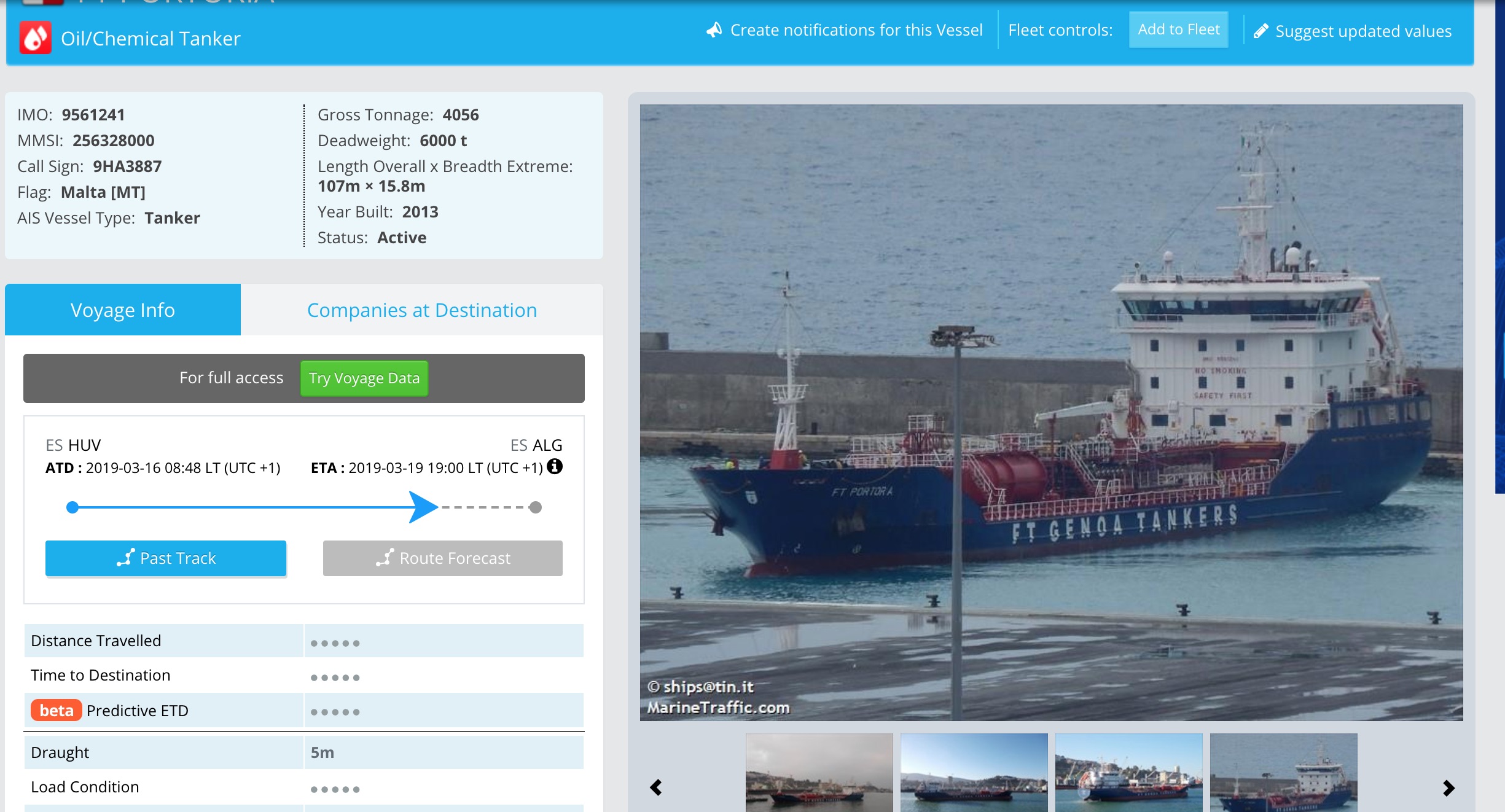
Here’s one that shows the location of a vessel in Russia.
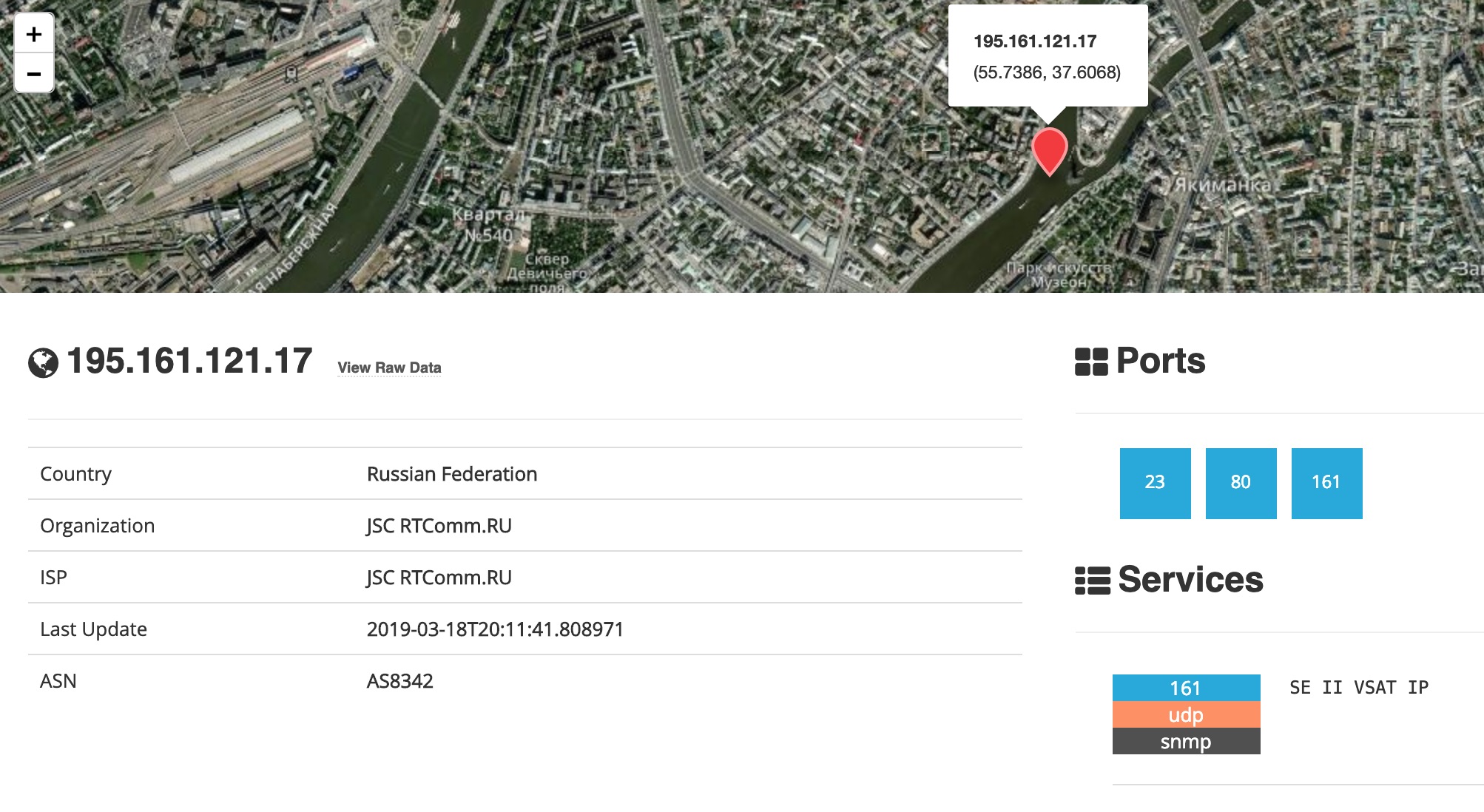
So we can track the vessel, here’s a better look at its location in google maps.
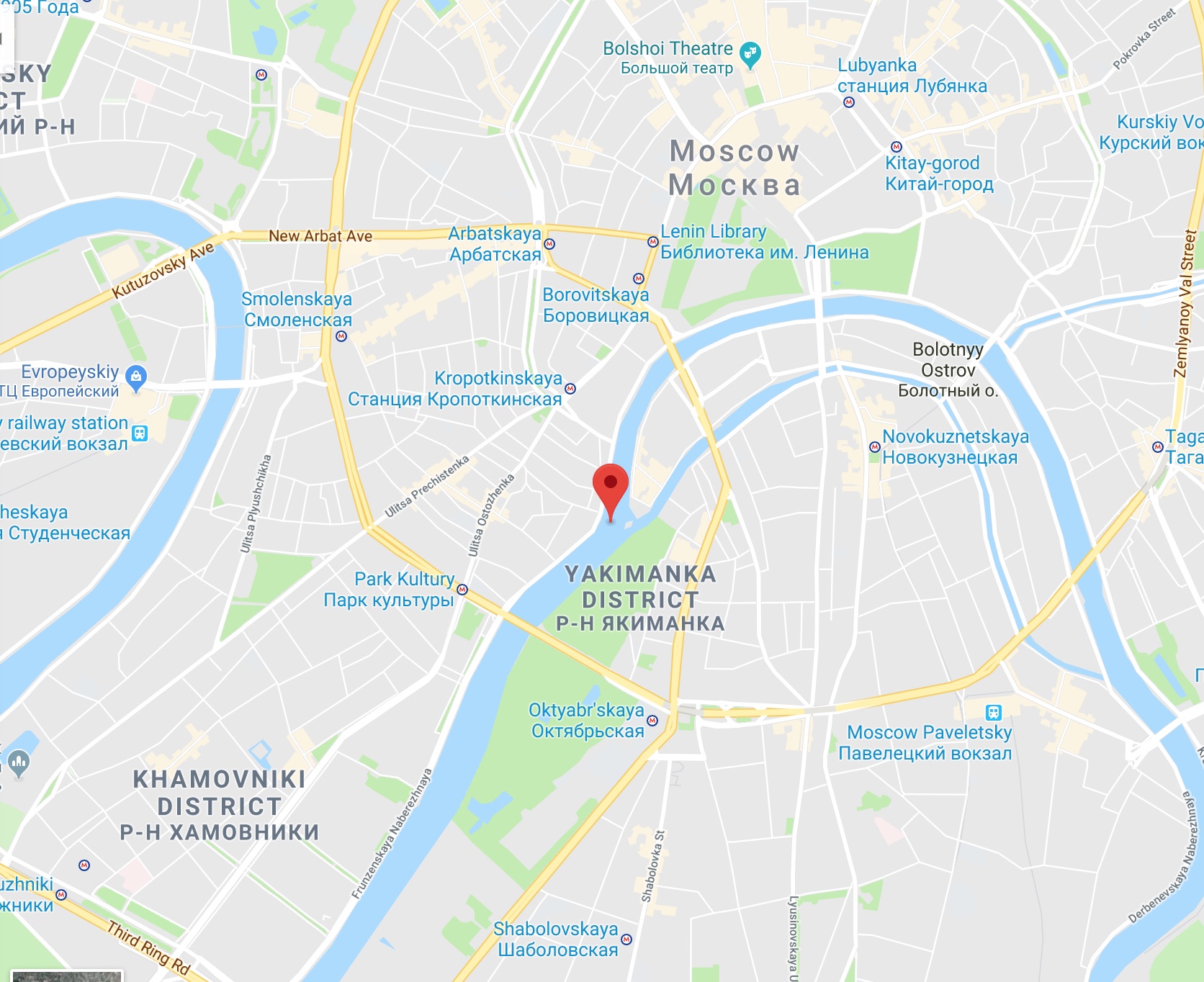
By using Marine traffic, it turns out the vessel is docked at a port. https://www.marinetraffic.com/en/ais/home/portid:20579/zoom:13
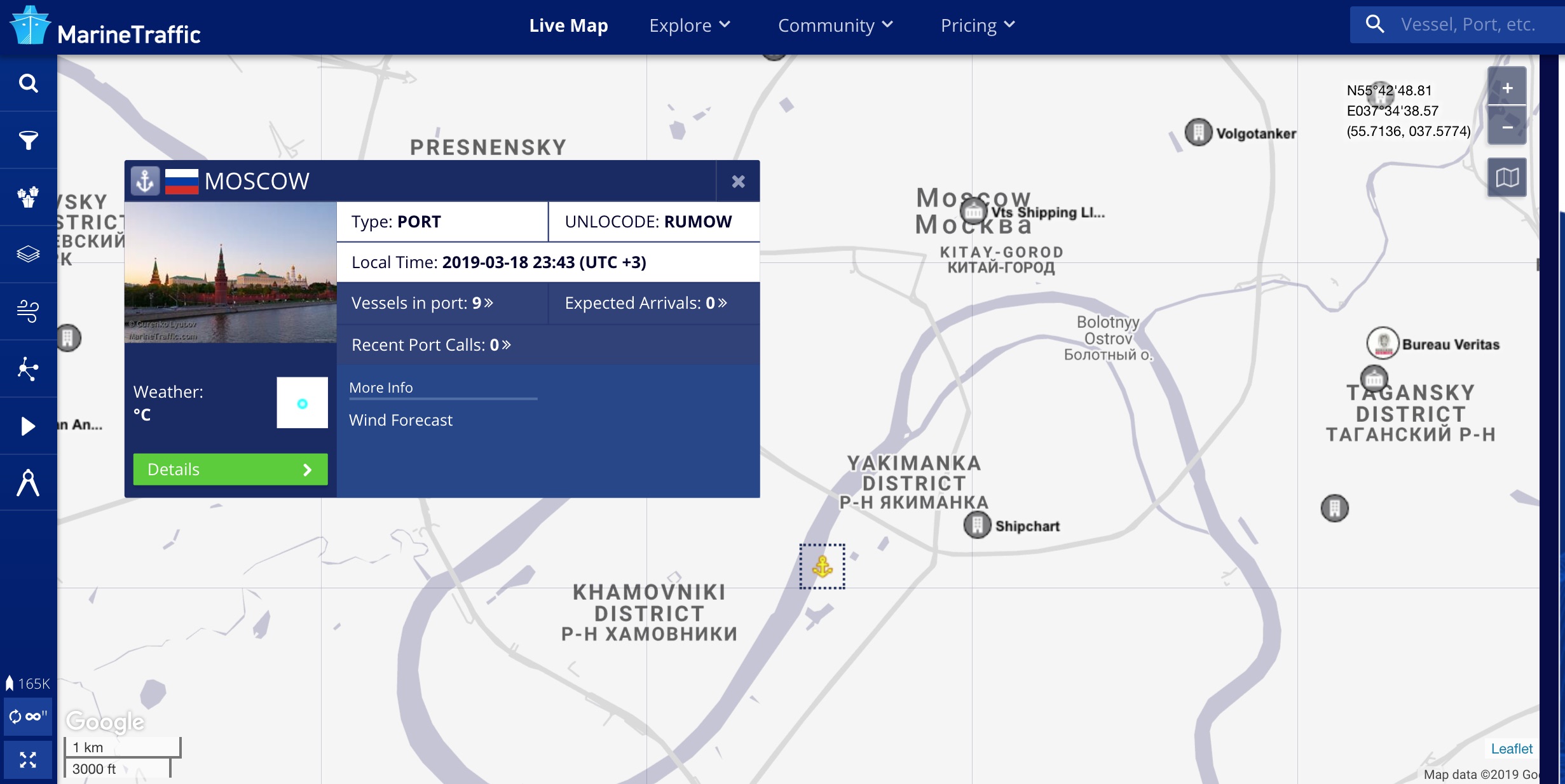
Lets try find one that’s not docked. Lets try search for inmarsat, another common VSAT.
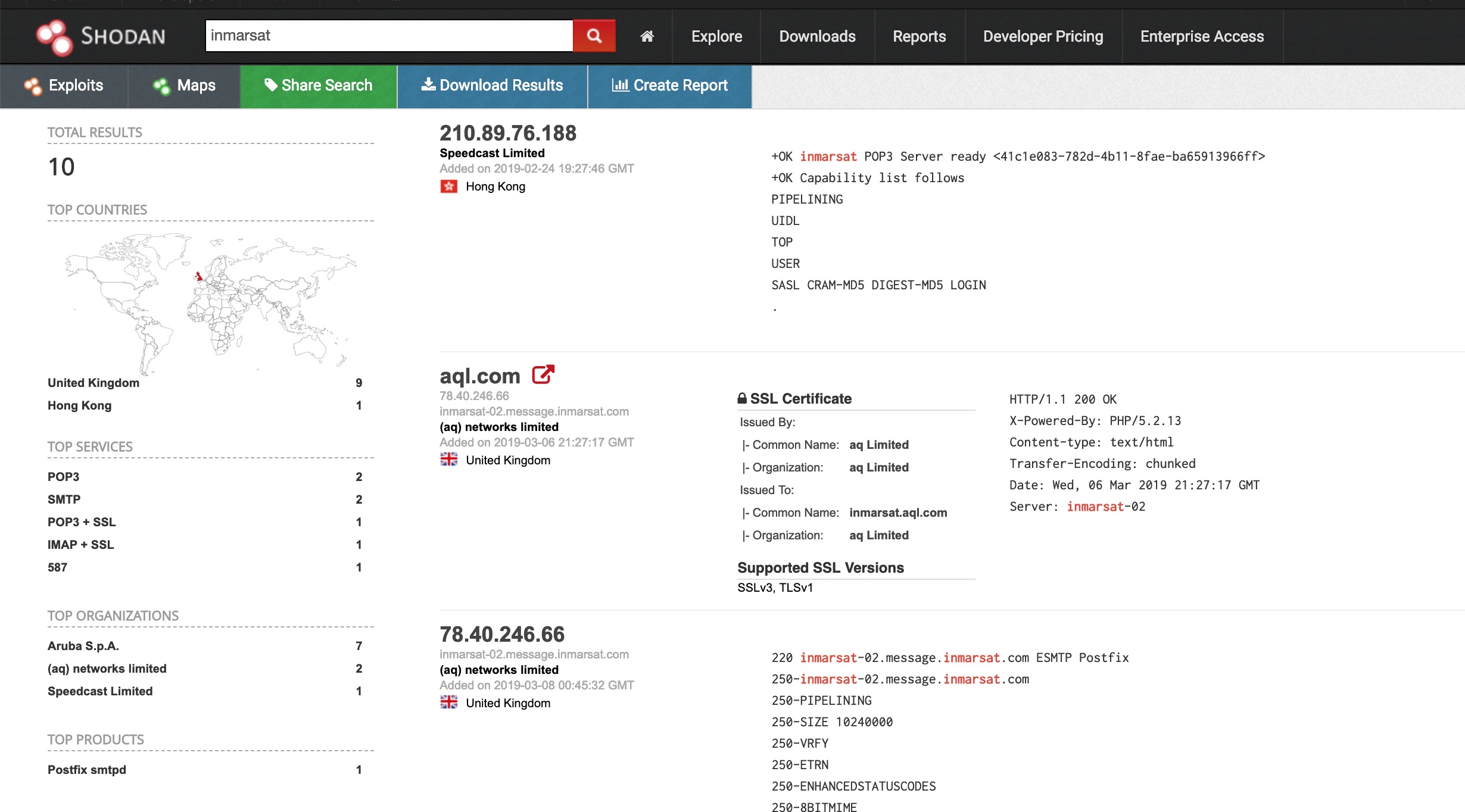
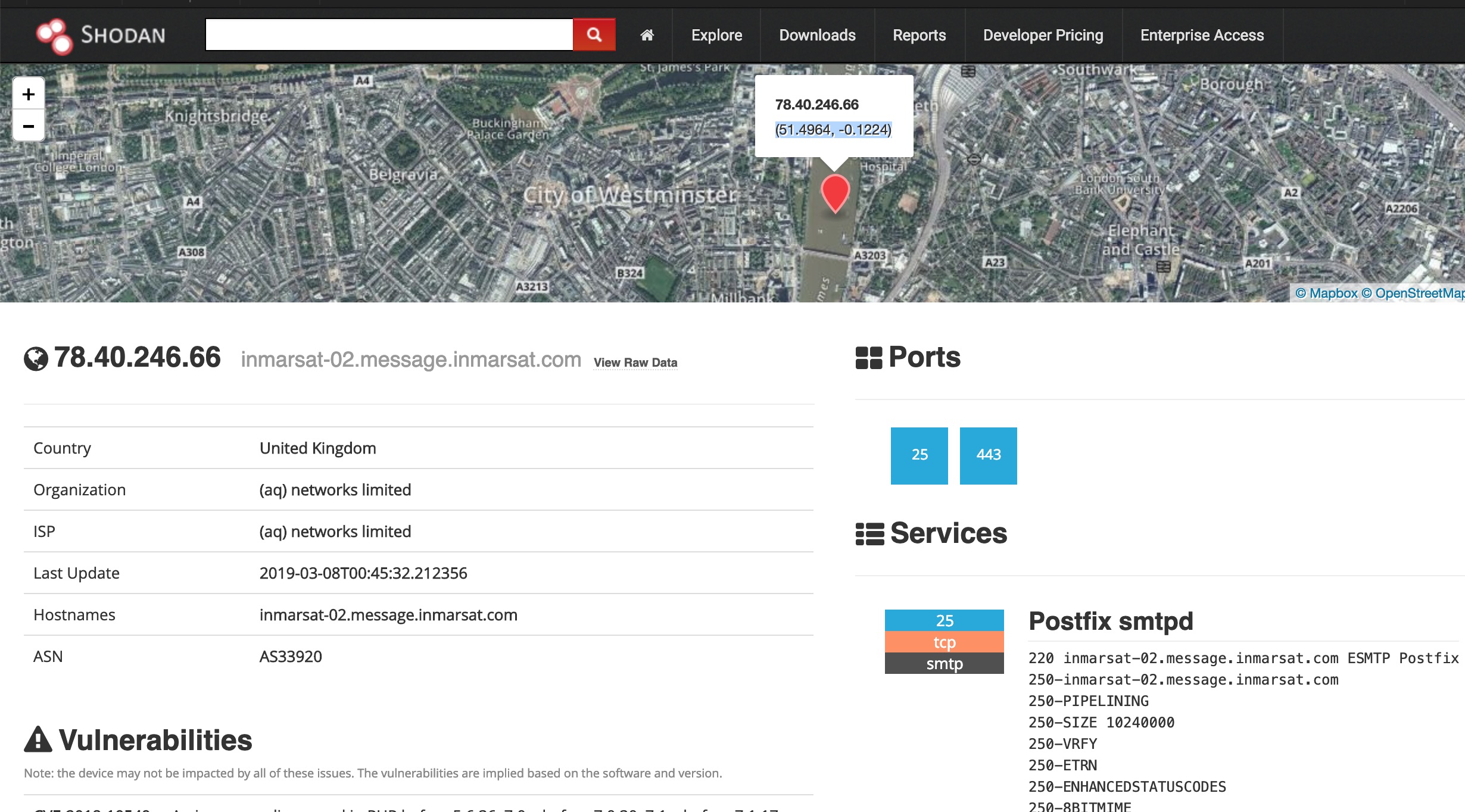
This one looks promising, lets collate the coordinates with marine traffic.
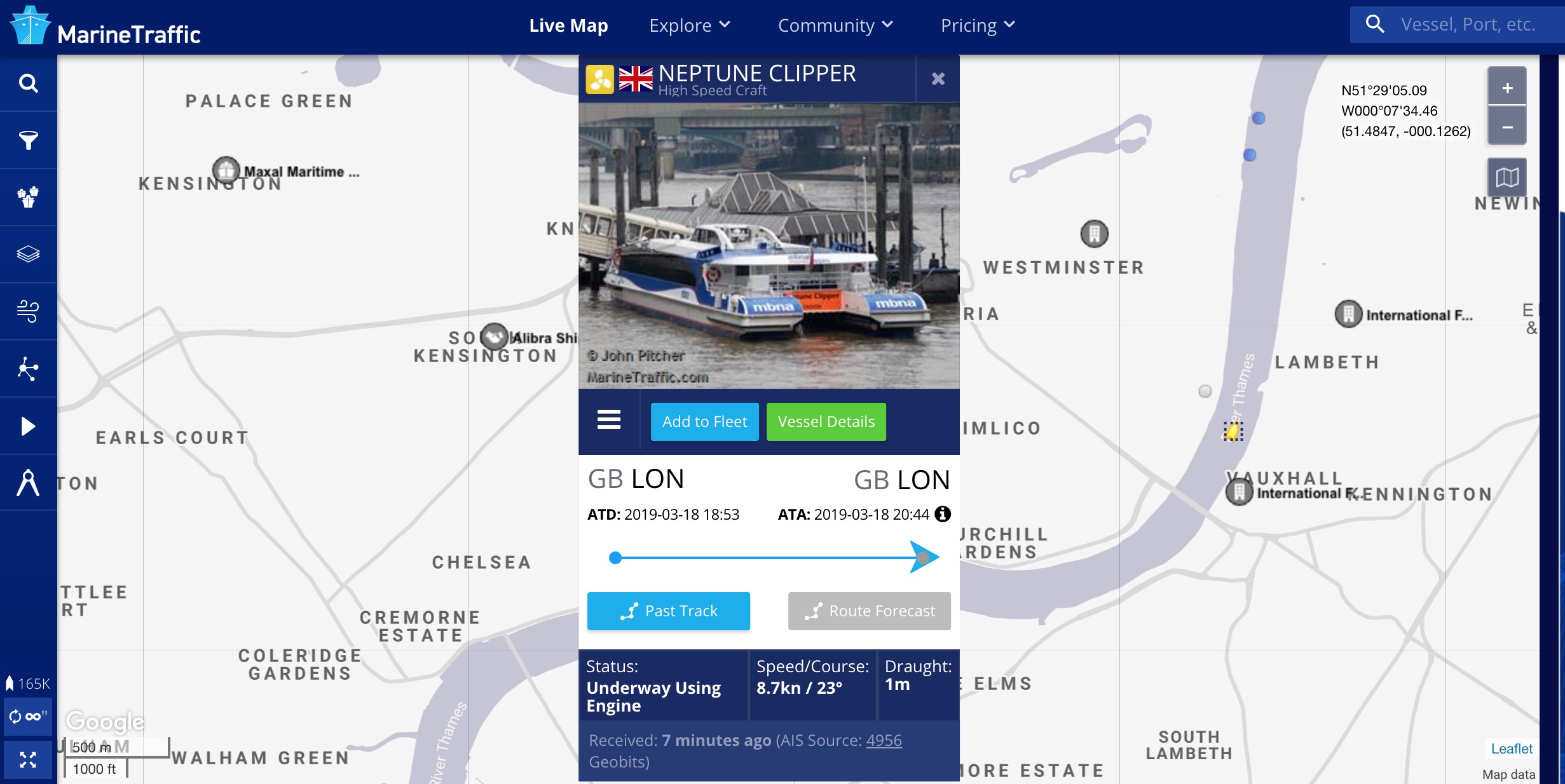
So now we’ve found a vessel, MarineTraffic shows a handy photo of it as well.
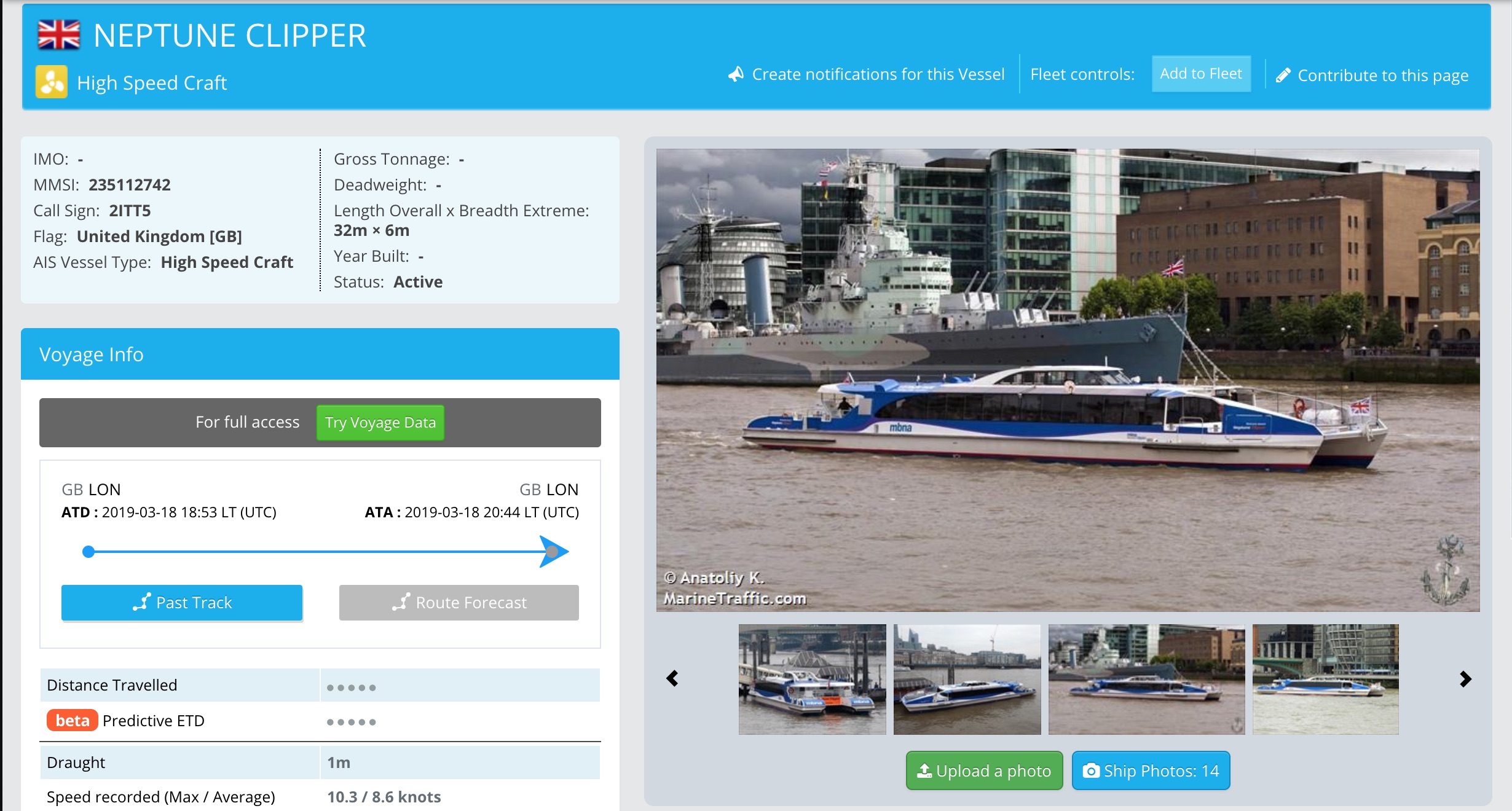
Going back to shodan, it also lists the vulnerabilities with the discovered services. Step forward to hacking into the VSAT of a vessel … ? Totally. Which is seriously bad news ! There’s thousands of these devices open to the internet.
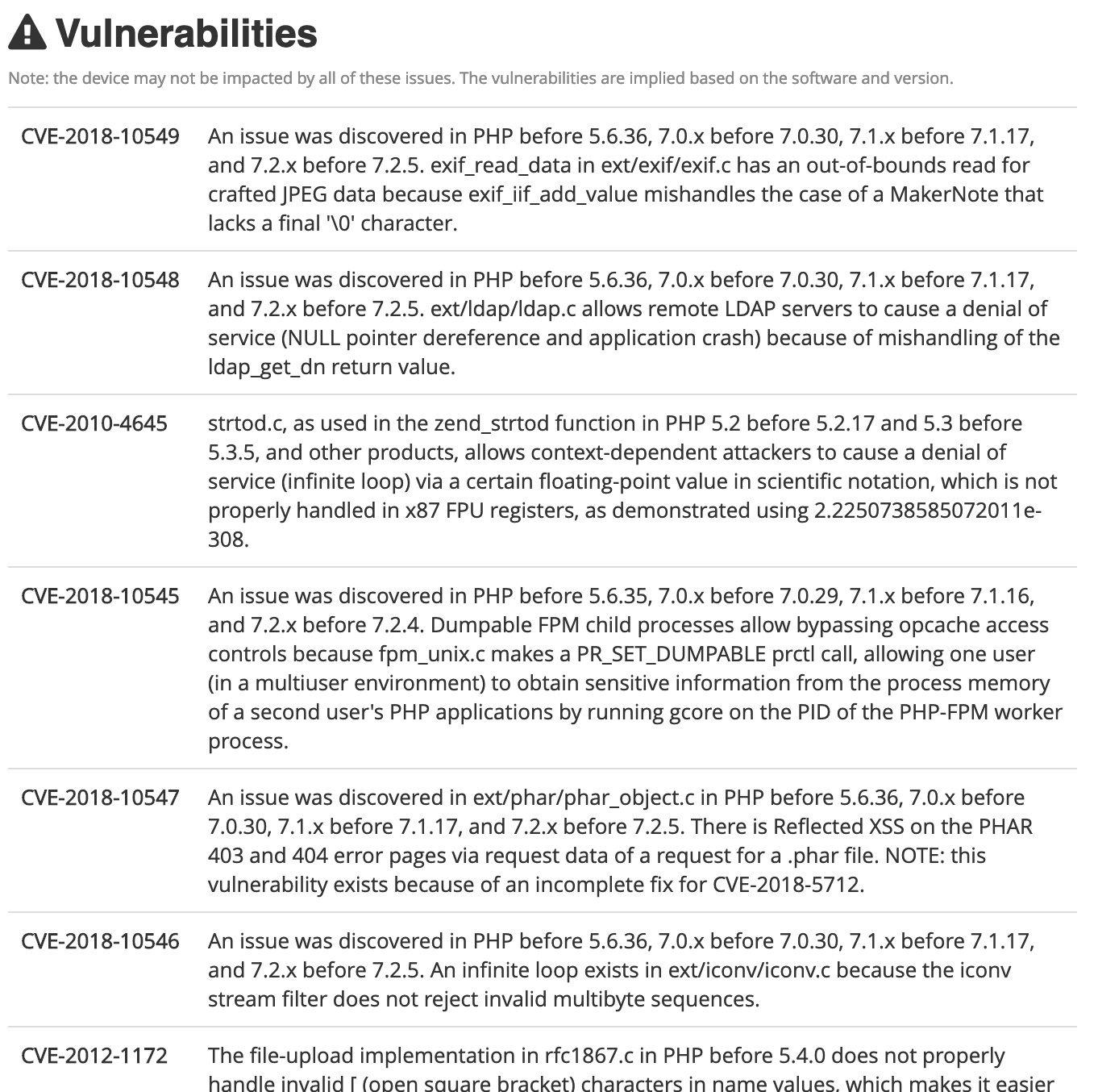
So now we can use the AIS GPS coordinates with the satcom boxes we’ve located on shodan. We can find a real vulnerability. If we search for some of the following we can locate other satcom boxes
- ‘inmarsat’
- ‘Sailor 900′
- ‘thrane’
These boxes have a web interface which often shows the firmware version running as well.
Here’s a Cobham satcom box running at firmware version 1.54 – serious out of date, The current version is 1.62 Build 008. https://sync.cobham.com/satcom/support/downloads/?type=2502&article=7399
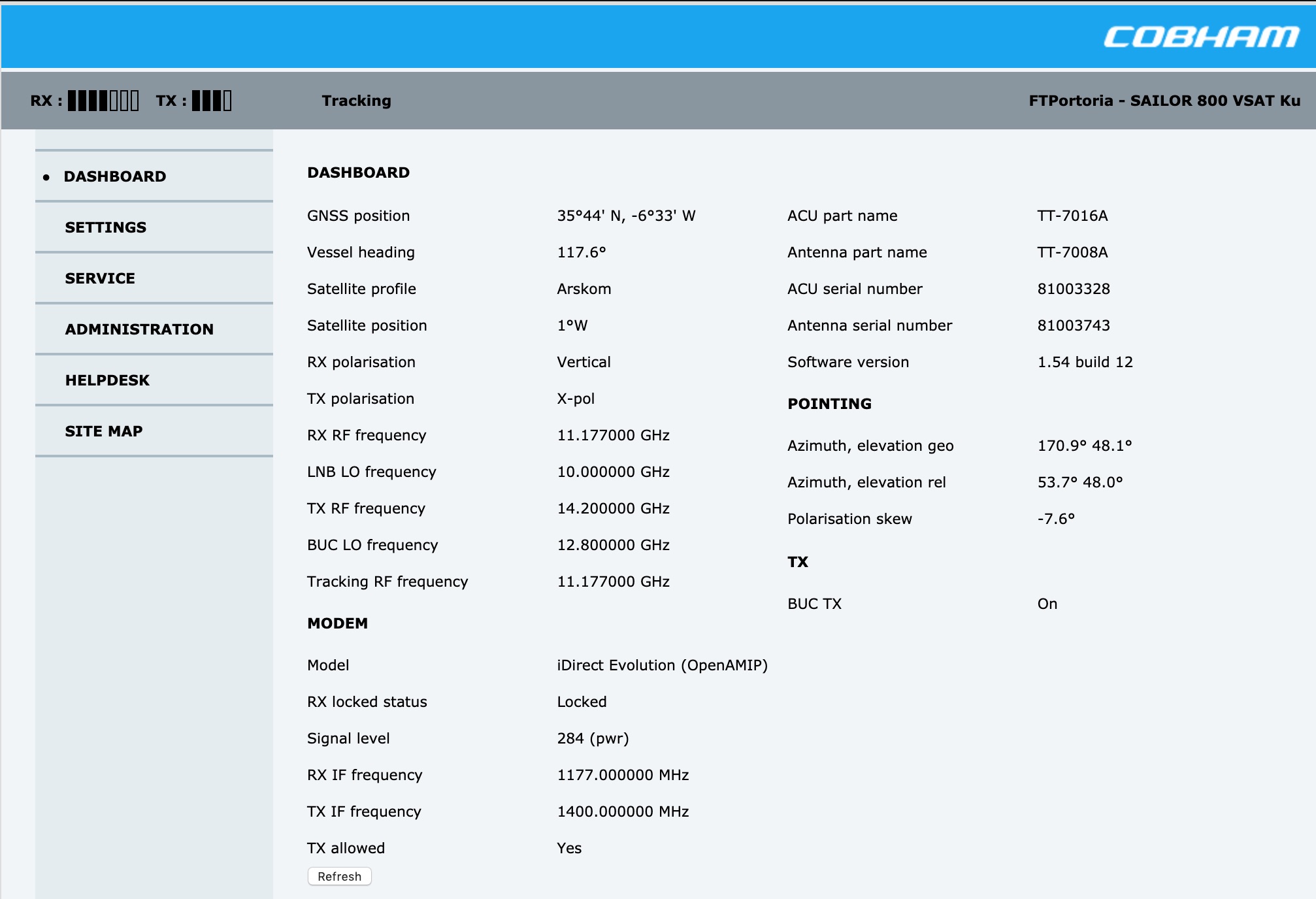
We can take the ships location live from the VSAT dashboard
GNSS position: 35°44' N, -6°33' W
Vessel heading: 116.9°
Yep defiantly not something you want exposed to the internet running seriously out of date firmware…

So going back to shodan, lets find some other VSAT Web interfaces. Search for ‘html:commbox’ and you’ll see a nice collection of KVH CommBox terminals.
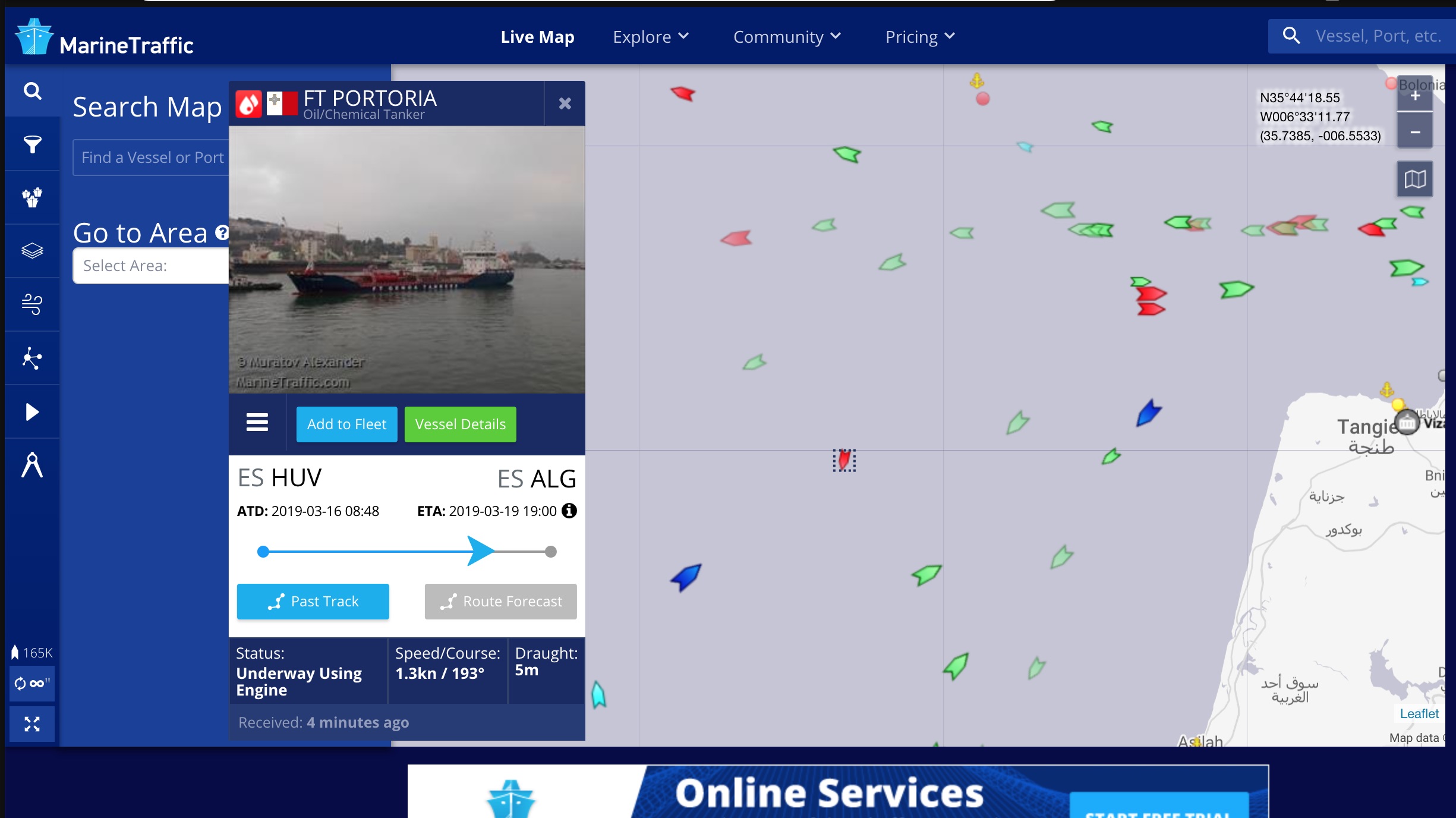
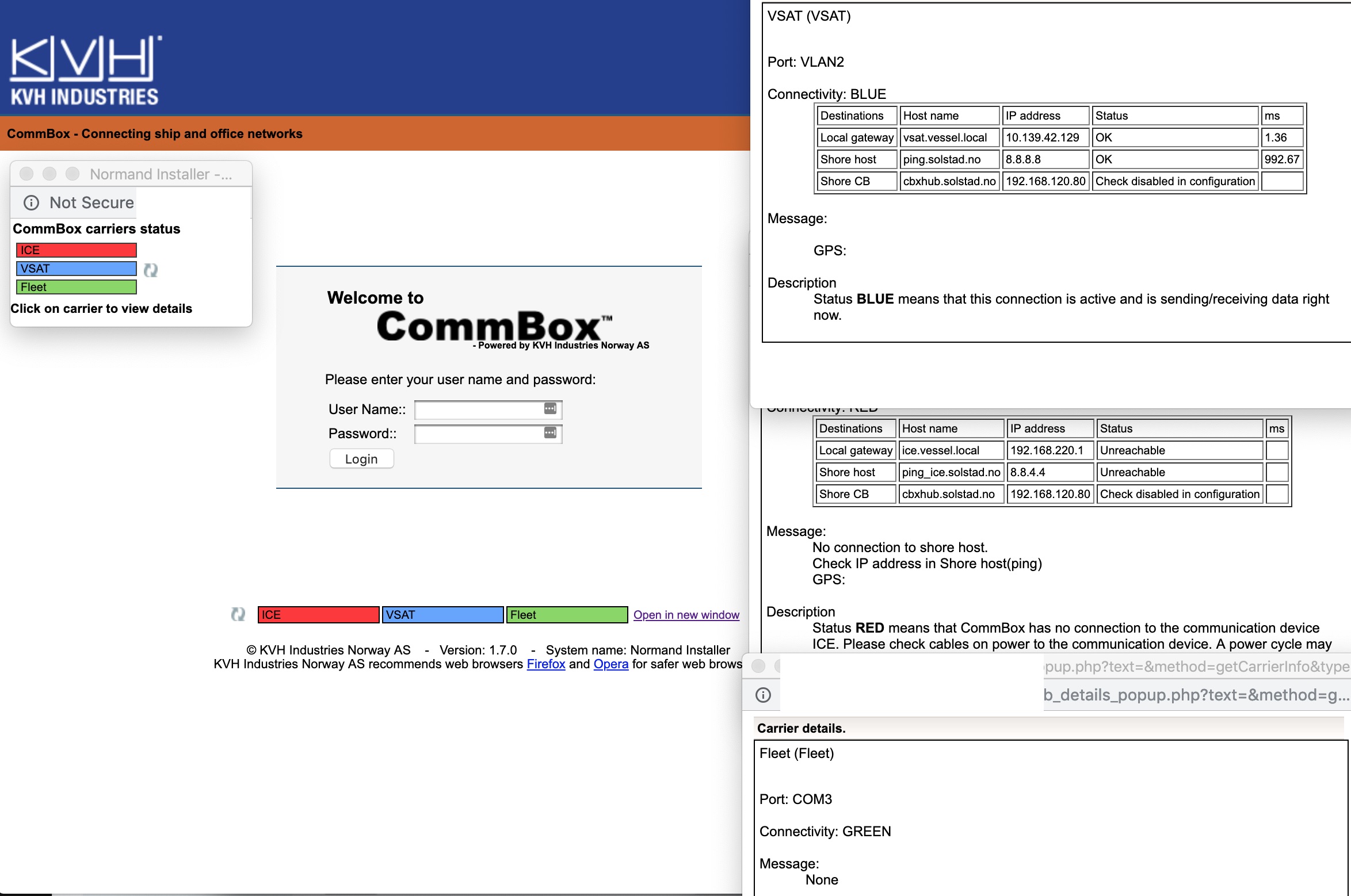
The status pages along the bottom contain the firmware version but also a whole load of other networking information about the vessel. Including the name “Normand Installer”
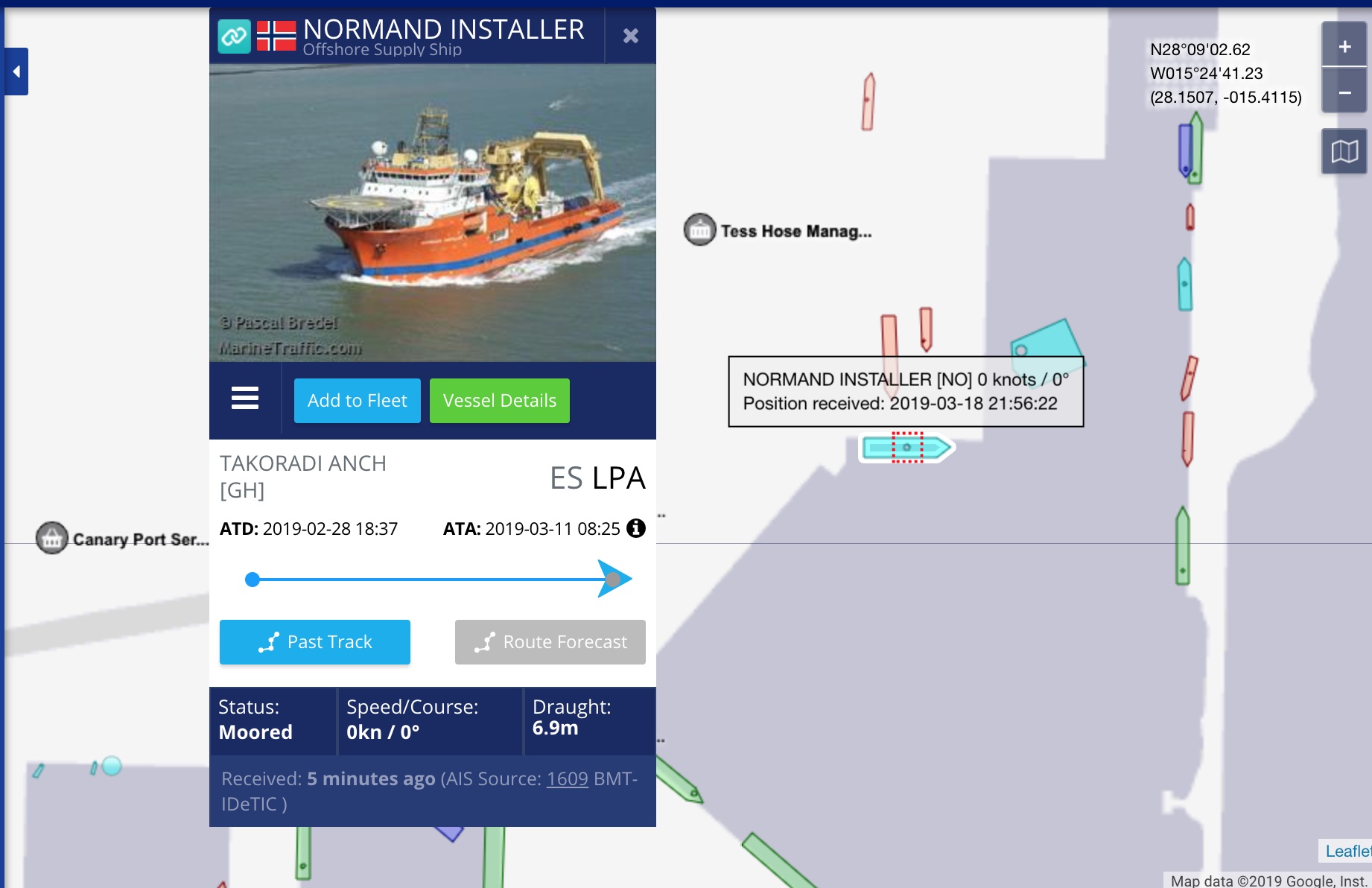
Which, back to marine traffic. We can find the location off and more information regarding this vessel.

Recent Posts
Tags
Categories
Active directory Burpsuite Cheatsheet Crackmapexec Empire Events Exploit File transfer Iis Implants Kcsec Kerberos Kernelpop Ksec Ksec snapshot Lab Metasploit Metasploitable Msfvenom Netcat Nfc & rfid Nikto Nmap Pivoting Privilege escalation Proxmark Proxychains Redteam Responder Rubber ducky Shells Sqlmap Sshutle Thefatrat Toolkit Webapp Windows domain Xss