Pivoting - SShuttle
Transparent proxy server that works as a poor man’s VPN. Forwards over ssh. Doesn’t require admin. Works with Linux and MacOS. Supports DNS tunneling.
sshuttle: where transparent proxy meets VPN meets ssh
As far as I know, sshuttle is the only program that solves the following common case:
- Your client machine (or router) is Linux, FreeBSD, or MacOS.
- You have access to a remote network via ssh.
- You don’t necessarily have admin access on the remote network.
- The remote network has no VPN, or only stupid/complex VPN protocols (IPsec, PPTP, etc). Or maybe you are the admin and you just got frustrated with the awful state of VPN tools.
- You don’t want to create an ssh port forward for every single host/port on the remote network.
- You hate openssh’s port forwarding because it’s randomly slow and/or stupid.
- You can’t use openssh’s PermitTunnel feature because it’s disabled by default on openssh servers; plus it does TCP-over-TCP, which has terrible performance (see below).
Obtaining sshuttle
Debian stretch or later:
apt-get install sshuttle
From PyPI:
sudo pip install sshuttle
Clone:
git clone https://github.com/sshuttle/sshuttle.git
cd sshuttle
sudo ./setup.py install
Homebrew:
brew install sshuttle
Documentation
The documentation for the stable version is available at:
http://sshuttle.readthedocs.org/
The documentation for the latest development version is available at: http://sshuttle.readthedocs.org/en/latest/
Usage
Connecting to remote systems using sshuttle is fairly simple and straight forward.
From your local system Terminal, enter command:
sshuttle -r username@sshserver 0.0.0.0/0 -vv
Or
sudo sshuttle -r username@sshserver 0.0.0.0/0 -vv
Or
sudo sshuttle -r username@sshserver 0/0 -vv
If you would also like your DNS queries to be proxied through the DNS server of the server you are connect to, then connect as shown below.
sshuttle --dns -vvr username@sshserver 0/0
Or
sudo sshuttle --dns -vvr username@sshserver 0/0
You will be may be prompted for one or more passwords; first, the local password to become root using either sudo or su, and then the remote ssh password.
That’s it. Now you’ll be able to access your remote clients.
Examples
This will connect as “sean” to “10.11.1.251” and set access to anything.
sshuttle -r [email protected] 0.0.0.0/24
This will connect as “sean” to “10.11.1.251” and set access to anything inside of the “10.1.1.0/24” Subnet
sshuttle -r [email protected] 10.1.1.0/24
Key Benefits
The account does not need to be admin! Low priv users will also work.
Sshuttle allows you to run most of it any other tools or commands which will auto route (like a VPN) via the pivot
If you use the following command
sshuttle -r [email protected] 10.1.1.0/24
And there are servers on the 10.1.1.0/24 subnet you want to access or connect to. After you’ve setup sshuttle you can for instance run nmap against a server such 10.1.1.1.223 and it will route the traffic via your pivot.
You can just run
nnmap 10.11.1.223
This works with most if not all other tools. You can then just target the servers IP and sshuttle auto routes the traffic without any need for config, setup or major drawback.
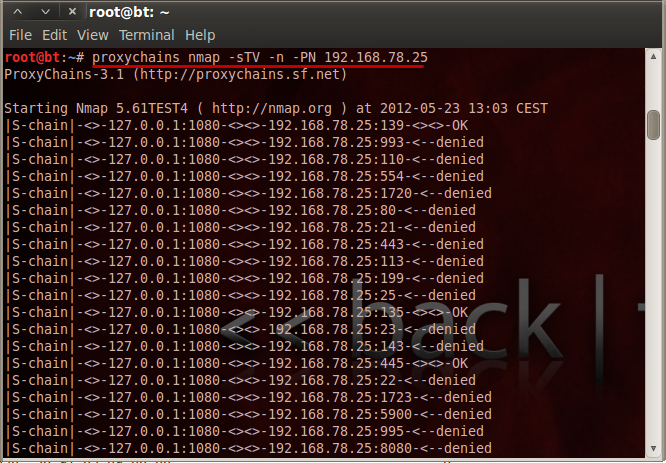
Where as in other methods such as proxychains, you have to run (After setting up config) + with the limitations of nmap via proxychains
More info on proxychains can be found here Proxy Chains Guide
proxychains nmap -sTV -n -PN 10.11.1.223
Recent Posts
Tags
Categories
Active directory Burpsuite Cheatsheet Crackmapexec Empire Events Exploit File transfer Iis Implants Kcsec Kerberos Kernelpop Ksec Ksec snapshot Lab Metasploit Metasploitable Msfvenom Netcat Nfc & rfid Nikto Nmap Pivoting Privilege escalation Proxmark Proxychains Redteam Responder Rubber ducky Shells Sqlmap Sshutle Thefatrat Toolkit Webapp Windows domain Xss