Posts

Upload a web.config File The web.config file plays an important role in storing IIS7 (and higher) settings. It is very similar to ...

What is a Rubber Ducky ? The USB Rubber Ducky is a keystroke injection tool disguised as a generic flash drive. Computers recogniz...
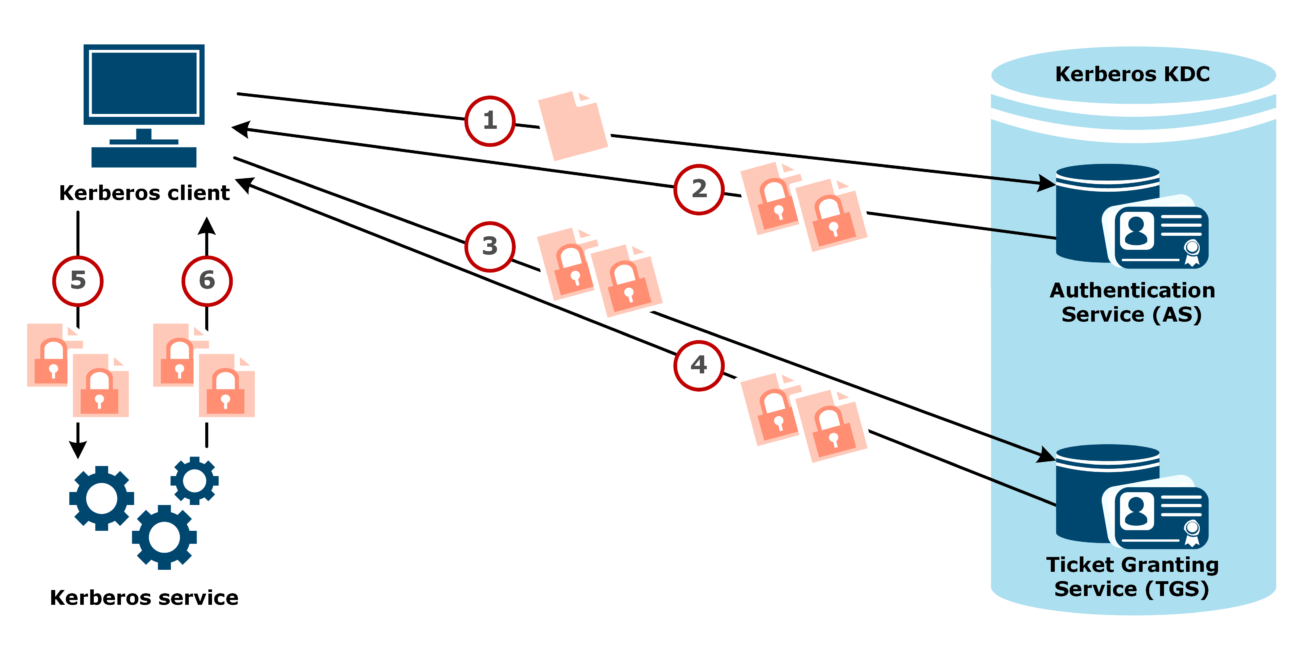
By Sean Metcalf in ActiveDirectorySecurity, Microsoft Security, Technical Reading, Technical Reference Usually Golden Tickets (for...

So Here is a tool called TheFatRat, can check out HERE. It’s still in development but it’s easy to follow and has some...

So Here is a tool called TheFatRat, can check out HERE. It’s still in development but it’s easy to follow and has some...
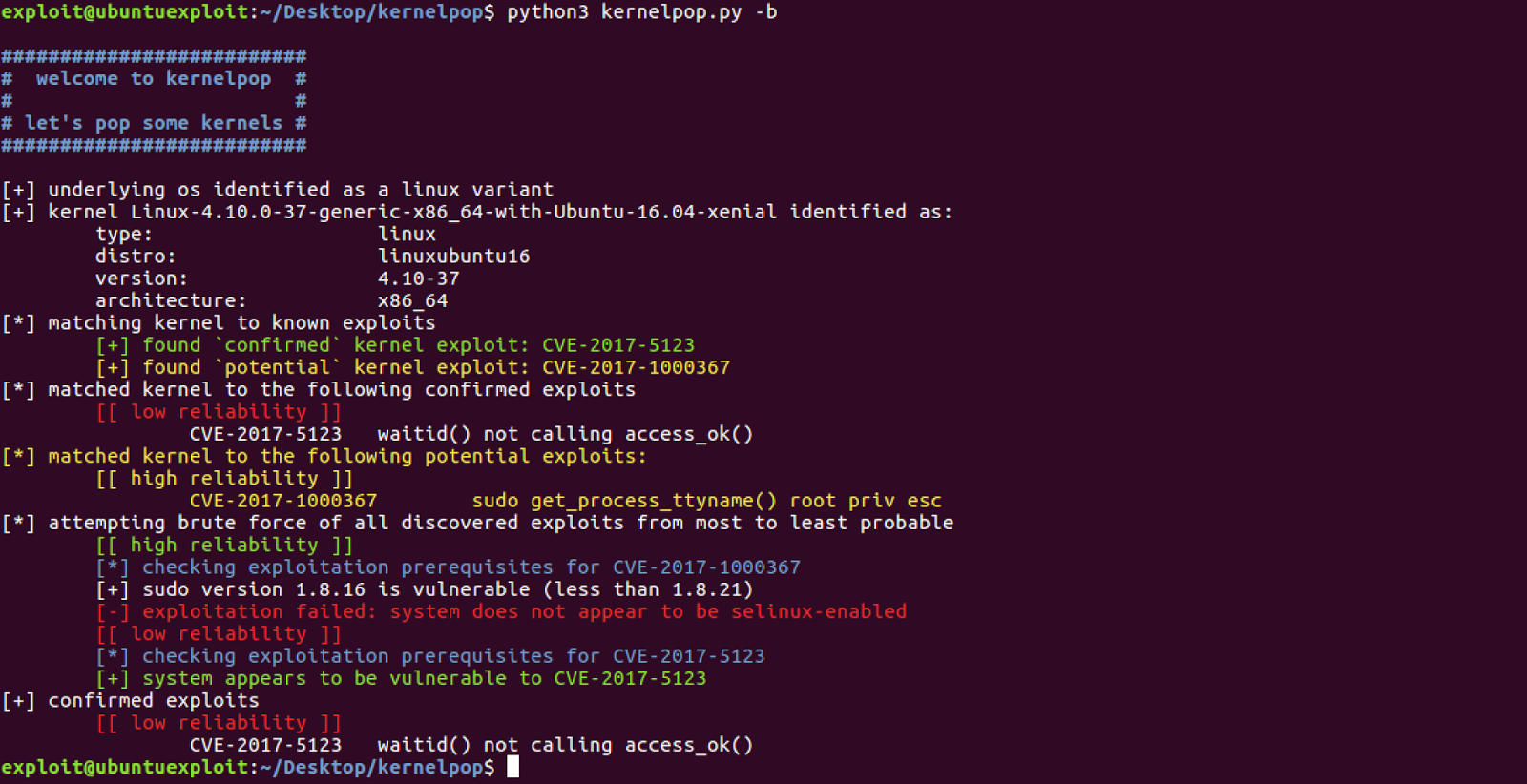
What is Kernelpop ? kernel privilege escalation enumeration and exploitation framework Supports the following OS’s Linux Mac...

KSEC do a range of implants, Too see for yourself check out their website and forum with the links bellow, There are two different...

xEM RFID Tag [T5577 Emulator] https://cyborg.ksecsolutions.com/x-series/xem/ The xEM is a great starter tag for people just gettin...
All of the blog posts regarding implants can now be found here https://cyborg.ksecsolutions.com/ We’ve a dedicated section on our ...

Overview This post will outline commands to read, write, simulate and clone RFID cards using the Proxmark 3 device. These commands...
Recent Posts
Tags
Categories
Active directory Burpsuite Cheatsheet Crackmapexec Empire Events Exploit File transfer Iis Implants Kcsec Kerberos Kernelpop Ksec Ksec snapshot Lab Metasploit Metasploitable Msfvenom Netcat Nfc & rfid Nikto Nmap Pivoting Privilege escalation Proxmark Proxychains Redteam Responder Rubber ducky Shells Sqlmap Sshutle Thefatrat Toolkit Webapp Windows domain Xss